Enhancing visual security: An image encryption scheme based on parallel compressive sensing and edge detection embedding
Yiming Wang(王一銘),Shufeng Huang(黃樹鋒),Huang Chen(陳煌),Jian Yang(楊健),?,and Shuting Cai(蔡述庭),?
1School of Integrated Circuits,Guangdong University of Technology,Guangzhou 510006,China
2School of Automation,Guangdong University of Technology,Guangzhou 510006,China
Keywords: visual security,image encryption,parallel compressive sensing,edge detection embedding
1.Introduction
Digital images have become a primary means of information storage and transmission in the modern era, playing a critical role in various aspects of daily life.As carriers for information, certain images may contain personal data, trade secrets,or military proprietary information.These images are susceptible to unauthorized tampering and interception when transmitted in an insecure network environment.Therefore,image encryption technology has considerable attention in the field of information security.
Numerous methods have been proposed to protect image security.The most traditional method is to use some encryption techniques to encrypt a plaintext image into cipher images of the same size, such as chaos systems,[1–5]DNA sequences,[6–8]neural networks,[9,10]optical technologies,[11,12]quantum computing,[13,14]and tensor theory.[15,16]In particular, chaotic systems are widely used due to their inherent uncertainty, unpredictability, and sensitivity to initial values.However, existing one-dimensional chaotic systems have drawbacks such as small key space and low complexity, researchers have proposed high-dimensional chaotic systems with better security properties.[17]Moreover,the scrambling-diffusion structure is the most common framework in encryption schemes based on chaotic systems.[18–22]
In recent years, compressive sensing (CS) techniques have been applied to image encryption.[23–27]The CS-based encryption method has the advantages of low computational cost, high security, and versatility.For instance, Xuet al.[28]combined the hyperchaotic system with CS.They took rowcolumn scrambling before compression to enhance the compression effect, and obtained cipher images with smaller size and higher security.In addition, some encryption schemes adopt two-dimensional compressive sensing to further reduce the size of the cipher image.[29–31]
The above-mentioned encryption techniques can encrypt images into noise-like images, so the attackers cannot obtain valuable information by analyzing the cipher images.Nevertheless,these encrypted images only provide content security and lack visual security,making them susceptible to interception by hackers when they are transmitted on open networks.In order to tackle this problem, Baoet al.[32]first proposed a visually meaningful image encryption algorithm,which encrypted the plain image and then embedded it into the carrier image to generate a visually secure cipher image.However,this method requires the carrier image to be four times the size of the plain image, resulting in higher storage requirement.Later, Chaiet al.[33]introduced CS to compress the image in the encryption stage before embedding,and obtained the visually secure encrypted image with the same size as the original image.This approach reduces the storage cost while maintaining the image quality.
According to the method of embedding encrypted image into carrier image, visual security image encryption schemes can be classified into two categories.The first method involves frequency domain analysis, such as integer wavelet transform,[34]discrete cosine transform,[35,36]singular value decomposition (SVD),[37,38]and so on.For example, Zhuet al.[38]proposed a robust meaningful encryption scheme which uses block CS to encrypt the plain image and embeds into carrier image through SVD.The method of embedding information in the frequency domain has strong robustness and high security.However, the embedding method utilized in this scheme is lossy, which means that the encrypted information cannot be entirely extracted from the cipher image.Additionally, its high computational complexity is unsuitable for practical applications.The second method is to operate in the spatial domain, the information is embedded by approaches such as the least significant bit replacement method[39–41]and pixel value difference.[42]In Ref.[41],Chaiet al.designed a dynamic LSB embedding method that can completely extract secret information from a cipher image.Although this method can achieve lossless embedding,it needs to be further improved in terms of robustness and visual quality.Moreover,many algorithms rely on fixed-location embedding,which means that the encryption system is not absolutely secure.When multiple images are encrypted by using the same method and one of them is decrypted,the security of the other images is compromised.
To solve the aforementioned issues,a visually secure image encryption scheme based on parallel compressive sensing(PCS) and edge detection embedding is proposed.PCS is a technique that integrates CS with parallel signal acquisition method, which is suitable for sampling by columns in image compression.PCS contributes to efficient compression of large-scale image data by simultaneously collecting data from each column.It not only reduces storage and transmission expenses but also ensures high-quality reconstruction.The edge detector is employed to identify the edges of the carrier image,which is crucial to divide pixels into edge and non-edge areas,enabling adaptive embedding for different carrier images with varying edge distributions.
The general process of encryption is as follows: the compressed image obtained after PCS is permuted and diffused to generate a secret image to resist attacks effectively.Subsequently,guided by the edge-detected carrier image,the pixels of the secret image are shuffled and embedded into the edge and non-edge pixels of the carrier image with various embedding bits.Due to variations in the edges of different carrier images, the embedding positions and bit numbers also differ.This adaptive embedding method enhances the visual security of the cipher image while maintaining high visual quality.The simulation results provide compelling proof of the security and reliability of the proposed scheme.The main contributions are as follows:
1.To effectively resist chosen plaintext attacks(CPA),the counter mode is used to update the keys to generate the measurement matrices.The initial vector of the counter derived from the hash values of the plain image.
2.To thoroughly scramble the pixels of the compressed image,a method of permutation is designed to enhance the randomness of the embedding process.
3.Based on edge detection, an adaptive lossless embedding method is devised, aiming to improve the embedding capacity of the carrier image and the visual security of the cipher image.
4.The simulation analysis demonstrates that the proposed encryption scheme can achieve excellent results in improving compression performance, visual security, and decryption quality under the framework of PCS and edge detection.
The rest of the paper is organized as follows: Section 2 introduces the relevant knowledge.Section 3 describes the proposed image encryption algorithm and its corresponding decryption algorithm in detail.The simulation experiments and performance analysis are conducted in Sections 4 and 5.Furthermore,in Section 6,the proposed algorithm is compared with existing visual image encryption algorithms.Finally,we summarize this paper and prospects for future research in Section 7.
2.Preliminaries
2.1.Chaotic systems
In our proposed algorithm, the chaotic sequence generated by the logistic-tent-sine chaotic system is used to construct the measurement matrix.In addition, the cascading infinite collapse system and the Chebyshev system generate two chaotic sequences to scramble and diffuse the compressed image,and then embed it into the carrier image.
2.1.1.Logistic-tent-sine chaotic system
In Ref.[43], the logistic-tent-sine (LTS) chaotic system is proposed to improve the performance of one-dimensional chaotic systems by providing a larger chaotic range and better chaotic behavior.The definition is as follows:
The values of chaotic sequences generated by the LTS chaotic system are within the range of(0,1).
2.1.2.Cascading Chebyshev system and infinite collapse system
As is well known,the Chebyshev system and the infinite collapse system are commonly used chaotic systems.However, their chaotic properties and traversal distributions are uneven, making them vulnerable to attacks.To address this problem,Jianget al.[44]proposed a cascading Chebyshev and infinite collapse system(2D-ICCS),defined as follows:
where the control parametersθ ∈[0,4].The outputs of the chaotic system are within the range of[?1,1].
2.2.Parallel compressive sensing
In CS,when a sparse signal is sampled at a rate lower than the Nyquist rate, the original signal experiences minimal distortion during the reconstruction of the sampled data.CS can simultaneously sample,compress,and encrypt images,which has attracted great attention from researchers in image security.To reduce computational complexity and storage space,parallel compressive sensing (PCS) samples and reconstructs a two-dimensional image in a column-wise manner.
In general,natural signals are non-sparse.Therefore,before further processing a signal with CS, it is necessary to transform the signal into the frequency domain to obtain its sparse representation.Suppose that there is a signalx ∈RN×1,under the orthogonal basisΨ ∈RN×N,which can be expressed as
wheresi={s1,s2,...,sN}is the coefficient vector.If the number of non-zero coefficients in the vectorsisK ?N, that is,the coefficient vector isK-sparse, then the signalxis sparse and compressible under the orthogonal basisΨ.
For a two-dimensional imageX ∈RM×N, denoted byxi ∈RN×1thei-th column of imageX.The image is sampled in a column-wise manner using measurement matricesΦ ∈Rm×N, wherem=CR×M,CRis the compression ratio.The measurement process of PCS can be expressed as
wherei=1,2,...,N,yiandΦirepresent the measurement vector and measurement matrix of thei-th column, respectively,Θ=ΦΨis the sensor matrix.
Signal reconstruction is also an important link of CS.To recover the original signalxfrom the observed valuey,the sensor matrixΘneeds to satisfy the restricted isometric property(RIP).The reconstruction process of signalxcan be expressed as al1-norm problem:
where‖s‖1represents thel1-norm of vectors.Several reconstruction algorithms have been proposed to solve the reconstruction problem, such as orthogonal matching tracking(OMP), matching tracking (MP), and smoothingl0parametric (SL0).In this paper, we employ the OMP algorithm for reconstructing the image.
2.3.Fisher–Yates shuffle
The Fisher–Yates shuffle algorithm, also known as the Knuth random permutation algorithm, is an effective method for scrambling pseudorandom sequences.The scrambling process can be described as follows:Given a sequenceZof lengthn, we start from the last elementZn, and randomly select an elementZifrom the 1st to then-th element, then swap them.Next, repeat this process for the elementZn?1.We select an element from the 1st to then?1-th elements and swap their positions.This operation is performed iteraively until all elements in this sequence are scrambled.
To provide a clearer illustration of the scrambling process,the sequence 21754386 is used as an example,as shown in Fig.1.
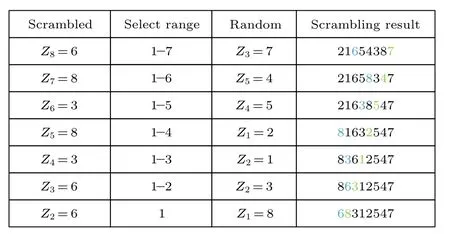
Fig.1.Fisher–Yates shuffle process.
2.4.Counter mode
In cryptography, the counter mode is commonly used in the process of packet encryption due to its effectiveness in resisting CPA,which can be described by
wherei=1,2,...,N,l·N <10λ,λis a security parameter,Ctr0is the initial vector,Nis the number of counters, andlindicates the number of encrypted images.
2.5.Edge detector
Edge detection is one of the fundamental methods in the field of image processing and computer vision.The purpose of edge detection is to identify points with significant brightness changes in digital images.These obvious image changes are attributed to crucial events or transitions.Through edge detection,the mutation of image intensity is identified,and each pixel is classified as a non-edge pixel or an edge pixel.Several basic edge detectors have been developed, including Sobel,Roberts,Laplacian,Prewitt,and Canny operators.The general criteria for edge detection include:(1)Low error rate.The objective is to identify all edges and minimize the occurrence of false responses.(2)High accuracy.The detected edges should closely match the actual edges.(3)Single edge point response.Each edge within an image should be marked only once to ensure that the potential noise in this image does not generate false edges.
Among the commonly used edge detection, the Canny edge detection algorithm stands out for its precise definition and reliable performance.It has become one of the most popular algorithms for edge detection due to its ability to satisfy the above three criteria.The Canny edge detection algorithm can be divided into the following steps.
Step 1 Use a two-dimensional Gaussian filter to smooth the image and filter out the noise.The choice of Gaussian kernel size has a significant effect on the performance of the edge detector.A larger kernel size results in less sensitivity to noise and may increase the positioning error in the edge detection.A kernel size of 5×5 is typically suitable for most applications,although the optimal size may vary depending on the specific case.
Step 2 Use the Sobel operator to calculate the magnitude and direction of the image intensity gradient.The Sobel operator is implemented through convolution with two-dimensional space gradient,whereSxrepresents the Sobel operator inxdirection, used to detect edges inydirection,Syrepresents the Sobel operator inydirection, used to detect edges inxdirection and is defined as follows:
For a 3×3 windowAin the image,the gradient of pixelecan be calculated after convolution calculation with the Sobel operator.The gradients of pixelein thexandydirections are expressed as follows:
where?is the convolution symbol, and the summations are taken over all elements in the matrix.Then we can calculate the gradient and direction of pixeleaccording to
Step 3 To eliminate spurious responses in edge detection,non-maximum suppression techniques are employed.Nonmaximum suppression is an edge refinement technique that refines blurred edges after gradient computation.It effectively suppresses all gradient values except local maximum to ensure that each edge has an accurate response.This method compares the gradient intensity of each pixel with its positive and negative gradient direction pixels.When the current pixel has the most significant gradient intensity, it is marked as an edge pixel.Otherwise,it is marked as a non-edge pixel.
Step 4 Perform dual-threshold technique to identify potential edges.After non-maximum suppression,the remaining pixels can better represent the actual edges in the image.However,there may still be edge pixels caused by noise and color variations.To address these false responses, a dual-threshold technique is applied.It involves filtering the edge pixels using a high thresholdThhand a low thresholdThl.Pixels with gradient values higher thanThhare labeled as strong edge pixels,and pixels within the threshold range [Thl,Thh] are identified as weak edge pixels.Pixels with gradient values lower thanThlare suppressed.The choice of thresholds depends on the input image.
Step 5 Suppress isolated low threshold points.Up to this point, the strong edge pixels are easily recognized, while the weak edge pixels may be mistaken for noise or color changes.The weak edge pixels and their eight adjacent pixels are examined to identify actual edges.If at least one of the adjacent pixels is a strong edge pixel,the weak edge pixel can be identified as an authentic edge.
The above five steps can complete the image edge detection based on the Canny algorithm, and Fig.2 shows the detection effect of the algorithm.
3.Visual security image encryption scheme
3.1.Keys generation
In our scheme, the SHA-256 hash function values of the plain image are used with the external keysK=(x',r',y',z',μ')to calculate the internal keys.Specifically,the initial values and parameters of the LTS chaotic system are updated by the counters withx0andr0.The 2D-ICCS is iterated with initial valuesy0,z0, and parameterμto generate chaotic sequences for permutation,diffusion,and embedding.The specific steps are as follows.
Step 1 Obtain the SHA-256 hash values of the plain image.Subsequently, segment the hash values into 8-bit blocks and convert them to decimal digitsh1,h2,...,h32.
Step 2 The internal keys are computed as follows:
Step 3 To construct the measurement matrices, the counter code is used to update the initial valuesxiand parameterriof the chaotic system, according to the following equations:
3.2.Encryption process
The flow chart of the proposed visual image encryption algorithm is shown in Fig.3.First, the plain image is preencrypted and compressed by the Fisher–Yates shuffle and PCS.Then,perform the permutation and diffusion operation to obtain the secret image.Finally,the secret image is embedded into the carrier image by using the edge detection technique.
Assume that the plain image isP ∈RM×N,and the carrier image isCI ∈RM×N,the detailed encryption process is shown in the following.
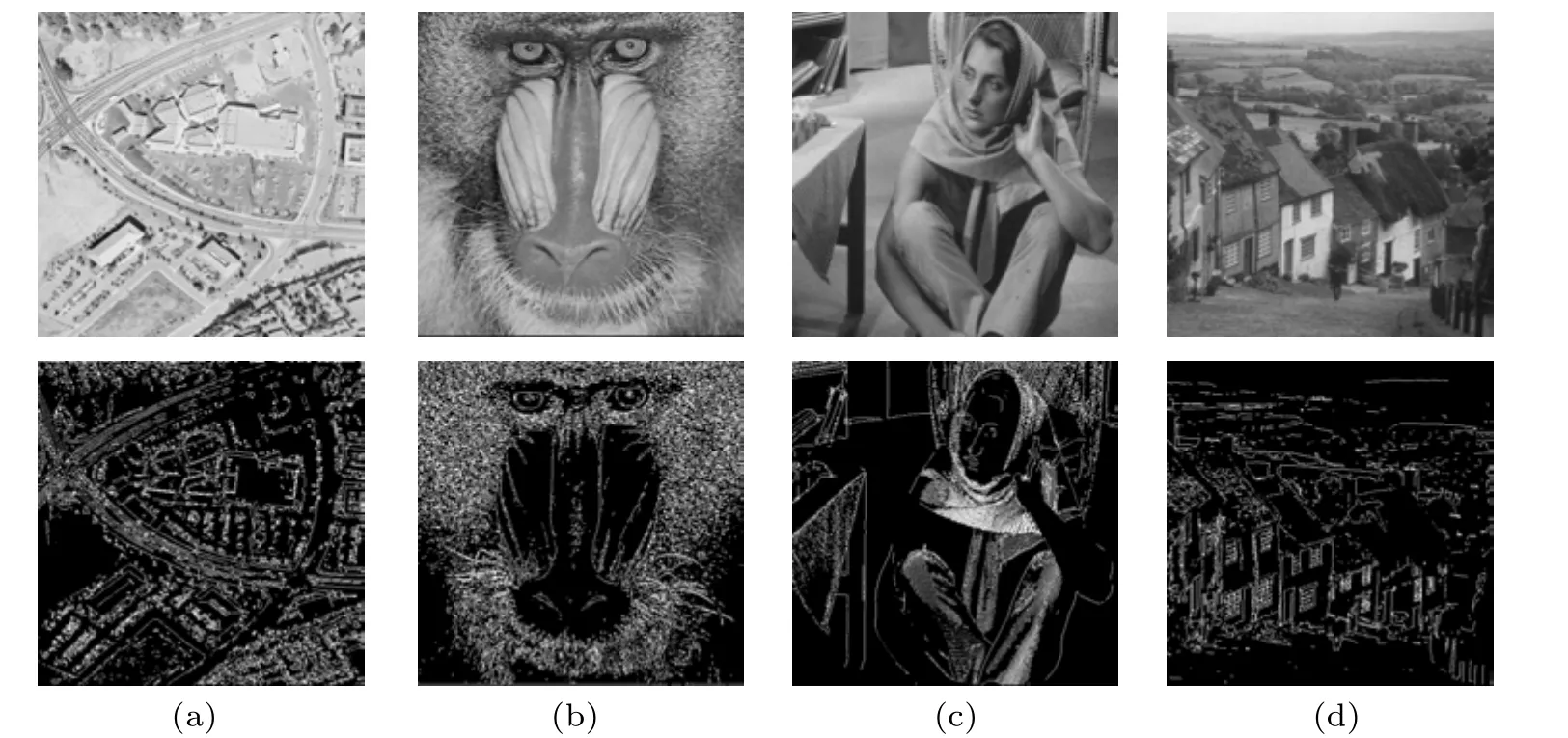
Fig.2.Plain images and the corresponding edge images: (a)–(d)are plain images of Aerial,Baboon,Barbara and Goldhill,and their corresponding edge images.
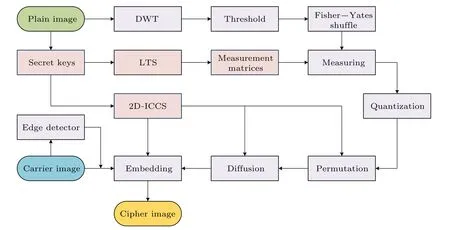
Fig.3.The flow chart of the proposed image encryption algorithm.
3.2.1.Compression process
Step 1 The sparse basisΨ ∈RN×Mis obtained via the discrete wavelet function(DWT),and transform the plain imagePto obtain the sparse coefficients matrixP1:
Step 2 Use Fisher–Yates shuffle to scramble the pixels of the imageP1.First, arrangeP1 into a one-dimensional sequence, then use the method described in Subsection 2.3 to scramble it,and the subscripts of randomly selected elements are recorded in the index sequenceorder.Finally, the scrambled sequence is rearranged into a two-dimensional matrixP2.
Step 3 Assign the thresholdTSto improve the quality of the reconstructed image.Set the values in matrixP2 with absolute values less than or equal toTSto zero, resulting in matrixP3.
Step 4 Construct measurement matricesΦi ∈Rm×N,wherei=1,2,...,N.The LTS chaotic system is iteratedm×N+t0times using the initial valuexiand parameterri,and discard the formert0elements to obtain the chaotic sequence.The measurement matrices are obtained by executing the following equation:
Step 5 Apply the measurement matrixΦito the corresponding columns ofP3 to generate the measurement value sequence,and combine all the sequences to obtain the matrixP4∈Rm×N,the process can be expressed as
Step 6 For the subsequent embedding operation, the imageP4 is quantified and mapped to the range[0,255]to obtain imageP5,
where min and max are the minimum and maximum of the matrixP4.
3.2.2.Permutation and diffusion
To augment the confidentiality and randomness of the scheme,the compressed image is permuted and diffused.The specific process is as follows:
Step 1 Generate two chaotic sequences by iterating the 2D-ICCS with the initial valuesy0,z0and parameterμ, takingm×Nelements after discarding the formert0elements,as follows:
Step 2 Arrange the sequencesYandZinto twodimensional matricesPY ∈Rm×N,PZ ∈Rm×N.Sort the elements in each column of in ascending order to obtain the index sort matrixPY'.
Step 3 Combine the elements of the indexed sort matrixPY'and their corresponding column coordinate to obtain the coordinate matrixOi,j=O(PY'i,j,j),wherei=1,2,...,m,j=1,2,...,N.
Step 4 Set the current row numberr=1.
Step 5 According to the coordinates in ther-th row of the coordinates matrixOi,j, seek{PYOr,1,PYOr,2,...,PYOr,N}from the two-dimensional matrixPZ, ascending order to get index sequenceIOr,j.The process can be expressed as
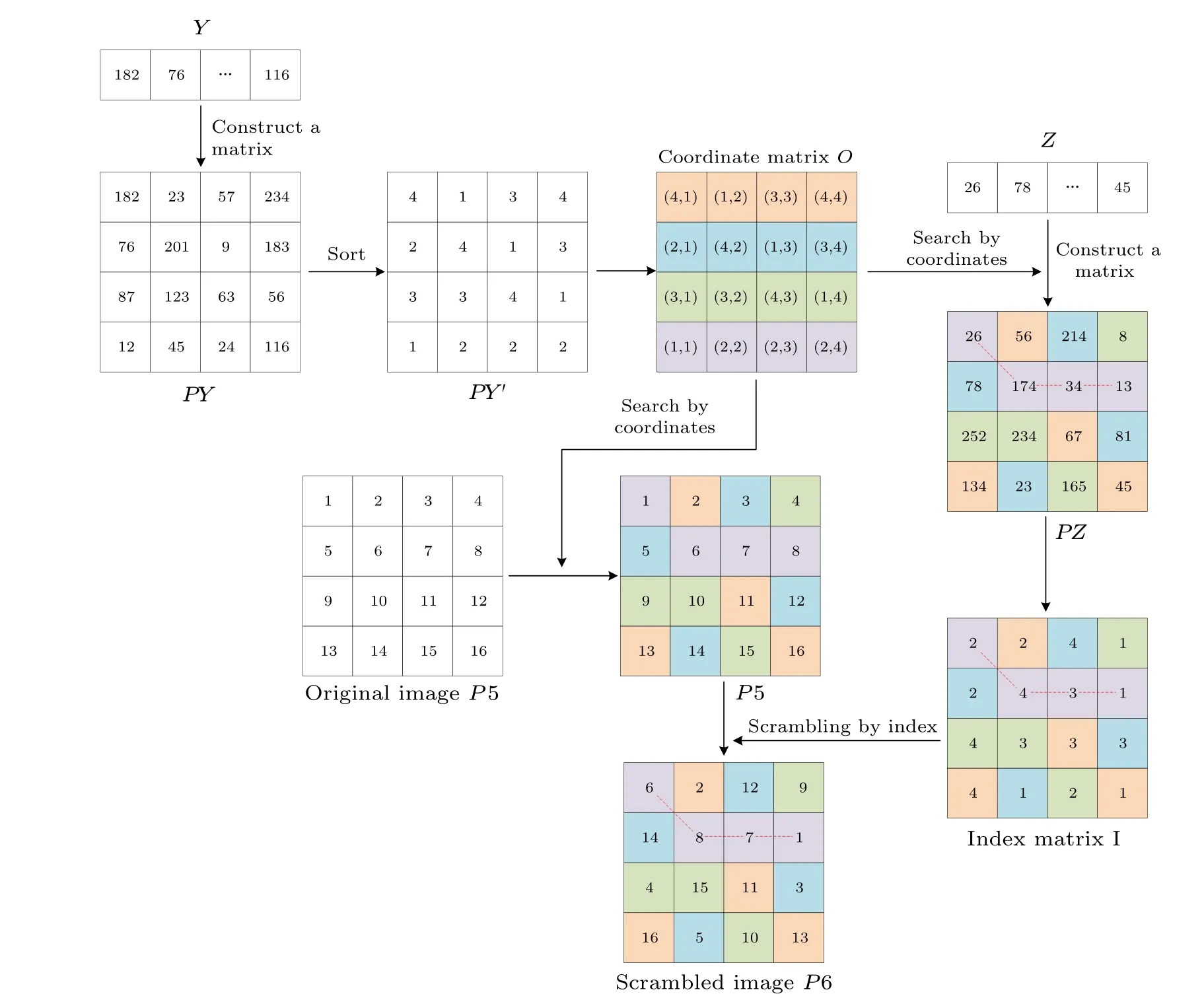
Fig.4.The flow chart of the designed permutation.
Step 6 According to the coordinates in ther-th row of the coordinates matrixOi,j,seek{P5Or,1,P5Or,2,...,P5Or,N}from the two-dimensional matrixP5, sort them according to index sequenceIOr,j.
Step 7 Set the row numberr=r+1.Repeat Steps 5 and 6 untilr=mto obtain the scrambled imageP6.To clearly illustrate the permutation process described above, we use a 4×4 matrix as an example,as shown in Fig.4.
Step 8 The chaotic sequencesYandZare transformed as follows:
The sequencesT1 andT2 are applied for forward and reverse diffusion, respectively, and the diffusion process can be described as
where⊕denotes theXORoperation.We can get the secret imageSI.
3.2.3.Embedding process
Step 1 Use the Canny edge detector to detect the edges of the carrier image through the process described in Subsection 2.5,and the edge imageEI ∈RM×Nis obtained.
Step 2 Aiming to avoid possible overflow, the grayscale value of the carrier imageCIis adjusted to the range[15,240]to obtain the imageCI'by the following equation:
wherea=15 andb=240.
Step 3 Based on the edge imageEI, the pixels of imageCI'are divided into edge and non-edge parts.Then, arrange them into a one-dimensional arrayC1=[U,V]with edge pixels first, followed by non-edge pixels.Suppose that the number of edge pixelsUisn, and the number of non-edge pixelsVisM×N ?n, denoted asU={u1,u2,...,un}andV={v1,v2,...,vM×N?n}.
Step 4 Take the formernelements of the chaotic sequenceYand the formerM×N ?nelements of sequenceZ,and sort them in ascending order to obtain index sequencessyandsz.ScrambleYandZin the order ofsyandszto getU'={u'1,u'2,...,u'n}andV'={v'1,v'2,...,v'M×N?n}, and then combine them into a scrambled arrayC2=[U',V'].
Step 5 All elements of the secret imageSIare converted to eight-bit binary and stretched into a one-dimensional secret bits arrayS={s1,s2,...,s8mN}of length 8×m×N.Each element of the arrayC2is also represented by an eight-bit binary.Then,each group of four secret bits is embedded in the lowest four bits of each edge pixelu'i, and the remaining 8mN ?4nsecret bits are embedded in the lowest two bits of non-edge pixelsv'isequentially.Finally,convert pixels in binary format to decimal.It is worth noting that certain non-edge pixels are devoid of any embedded secret bits.
Step 6 After embedding operation, scramble theU'andV'according to the reverse order of the index sequencesyandszto obtainU''andV'',and then get the arrayC3=[U'',V''].
Step 7 The arrayC3is rearranged into a two-dimensional matrix to obtain the final visually meaningful cipher imageVI.The encryption process is completed.
3.3.Decryption process
To decrypt the cipher image, the keys are transferred to the decryption side, including the compression ratioCR, the initial vectorCtr0of the counter, the parameters and initial values{x0,r0,y0,z0,μ0}of chaotic systems.The flow chart of the decryption algorithm is shown in Fig.5.The specific decryption process is as follows:
Step 1 Perform edge detection on the carrier imageCI.Then, the pixel positions of the cipher imageVIcorrespond to the detection result, divided into edge and non-edge segments.Extract the edge pixelsU''are arranged in the front and the non-edge pixelsV''are arranged in the back to form a one-dimensional array.
Step 2 Iterate the 2D-ICCS to obtain two chaotic sequencesYandZ, and take the firstnand the firstM×N ?nelements, respectively.Arrange them in ascending order to obtain the index sequencessyandsz, scramblingU''andV''to obtainU'andV'.
Step 3 The elements inU'andV'are converted to eightbit binary, then the lowest four bits of each elementu'iinU'and the lowest two bits of the elementv'iinV'are extracted and arranged into an array in turn.Take the first 8×m×Nelements to construct the secret bit arrayS,and convert it into decimal in a group of each eight elements.Finally, the array of lengthm×Nis rearranged into a two-dimensional matrix to acquire the secret imageSI.
Step 4 The chaotic sequencesT1 andT2 are used for the inverse forward and backward diffusion according to the following equations:
Step 5 The index matrixIis obtained according to Section 3.2.2 for implementing the inverse permutation to generate the matrixP5.
Step 6 Execute the inverse quantization on the matrixP5.
Step 7 Calculate the measurement matrixΦi, and then use OMP to reconstruct the matrixP3,the process is shown as follows:
Step 8 According the index sequenceorder,perform the inverse Fisher–Yates shuffle to obtain the sparse coefficient matrixP2.
Step 9 The decrypted imagePis obtained by applying inverse discrete wavelet transform(IDWT)onP2,and can be expressed as
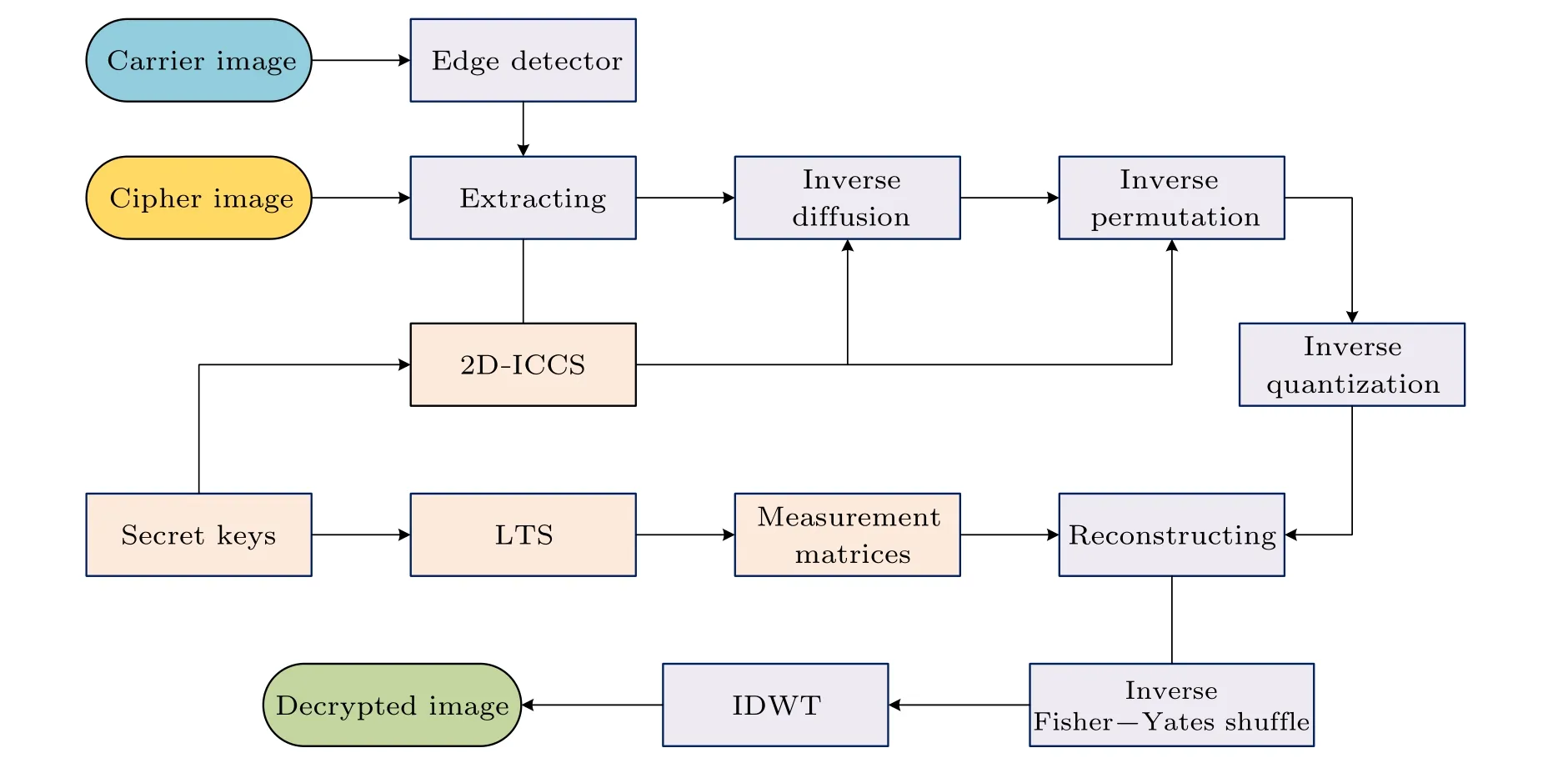
Fig.5.The flow chart of the proposed image decryption algorithm.
4.Simulation results
4.1.Encryption and decryption results
To verify the effectiveness of the proposed encryption algorithm,the simulation experiments are implemented on Matlab R2018a.The hardware condition is Intel(R)Core(TM)i5-12500 CPU@3.00 GHz with 16.00 GB RAM,and the operating system is Microsoft Windows 10.The 512×512 sized images including Lena, Girl, Peppers, and Jet are selected as the plain images, and the same size images including Baboon, Goldhill, Aerial, and Bridge are selected as carrier images for testing.The keys are set asx'=0.6107,r'=0.8915,y'=0.3109,z'=0.1681,μ'=0.3057, and other parameters areCR=0.25,TS=30.In the decryption process, OMP is chosen as the reconstruction method.
The simulation results are shown in Fig.6,where from the first to the fifth column are listed the plain image,secret image,carrier image, secret image, cipher image, and decrypted image.Notably,the noise-like secret image is one-fourth the size of the plain image and cannot provide any helpful information,proving the effectiveness of the encryption and compression of the scheme.Meanwhile, the generated steganographic image has the same visual effect as the carrier image, which indicates that the proposed encryption scheme has visual security and can protect the secret information effectively.Additionally, the decrypted image is similar to the plain image, and since the embedding process is entirely reversible,it is demonstrated that the reconstruction quality is satisfactory.
To quantitatively assess the performance of the proposed encryption scheme,this paper applies the peak signal-to-noise ratio (PSNR) and mean structural similarity index measure(MSSIM) to compare the similarity between the carrier image and the cipher image as well as to measure the quality of the decrypted image.Their equations are given as follows:
whereC1= (k1×L),C2= (k2×L),k1= 0.01,k2= 0.01,L=255;σX,σY,μX,μY, andσXYdenote the variance, average and covariance values of the plain image and the decrypted image,respectively,andNis the number of the image blocks.
The test results of PSNR and MSSIM are listed in Table 1.Numerically,all PSNRcipvalues are greater than 40 dB,the values of PSNRdecare about 35 dB, and the values of MSSIM are close to 1.The above results demonstrate that our scheme can encrypt the plain image into a visually meaningful steganographic image,and the decrypted image maintains high quality.
4.2.The relationship between decrypted images and different carrier images
Considering the effect of different carrier images on the quality of cipher image and decrypted image is helpful to evaluate the performance of encryption schemes.The 512×512 sized image is embedded into five different carrier images,i.e.,Goldhill, Barbara, Baboon, Aerial, and Bridge.The simulation results are shown in Fig.7.The influence of the carrier image on the decryption results is assessed by calculating the PSNR and MSSIM values of the decrypted image.It can be seen from Table 2, all the PSNRdecare about 36 dB, indicating that the different carrier images have almost no effect on the quality of the decrypted images.It needs to be explained that the slight numerical differences are due to the randomness of the Fisher–Yates shuffling process,even though the embedding process is reversible.

Fig.6.Simulation results: [(a),(f),(k),(p)]the plain images Girl,Lena,Peppers and Jet; [(b),(g),(l),(q)]the corresponding secret images; [(c), (h), (m), (r)] the carrier images of Baboon, Goldhill, Aerial and Bridge; [(d), (i), (n), (s)] the corresponding cipher images;[(e),(j),(o),(t)]the corresponding decrypted images.
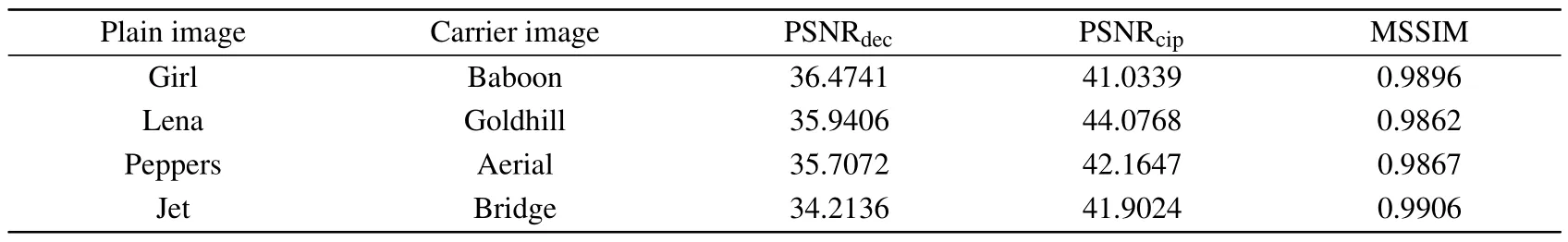
Table 1.PSNR and MSSIM values of simulation results.PSNRcip and MSSIM are used to compare the similarity between the cipher image and the carrier image,and PSNRdec is employed to quantify the quality of the decrypted image.
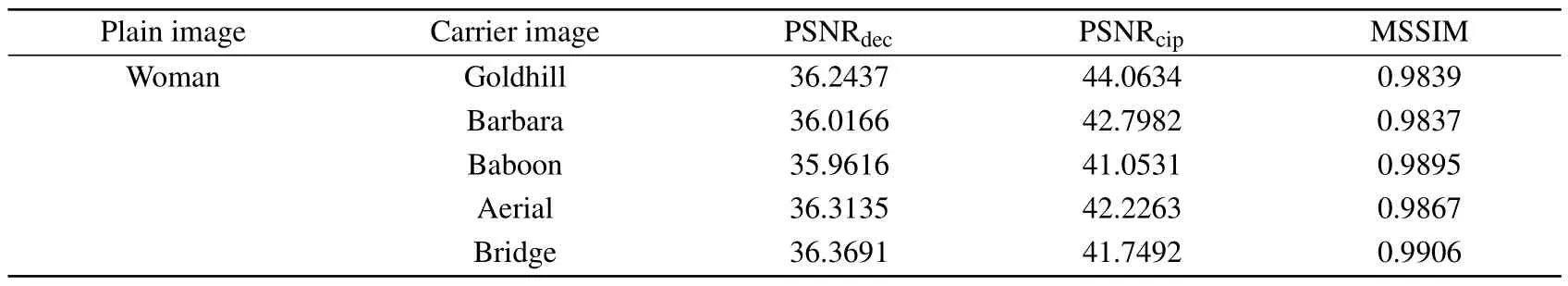
Table 2.PSNR and MSSIM values of the different carrier images.
4.3.The influence of TS and CR
In the proposed encryption scheme,the choice of threshold value TS has a direct impact on the quality of the decrypted image.We conduct an evaluation using four 512×512 sized plain images, including Peppers, Barbara, Lena, and Boat, as depicted in Fig.8.As can be observed, when TS is less than 30, the quality of the decrypted image is improved as TS increases.However, when TS exceeds 30, the quality starts to degrade.Therefore,the threshold value should be set to 30 for optimal decryption performance.
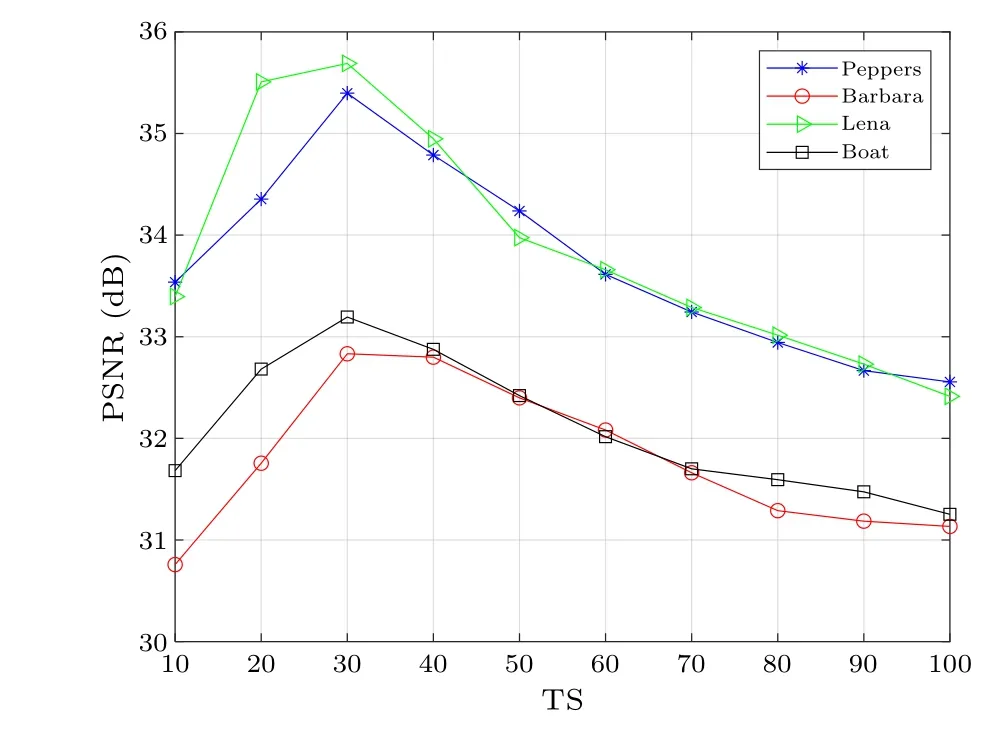
Fig.8.Influence of TS changes on PSNRdec.
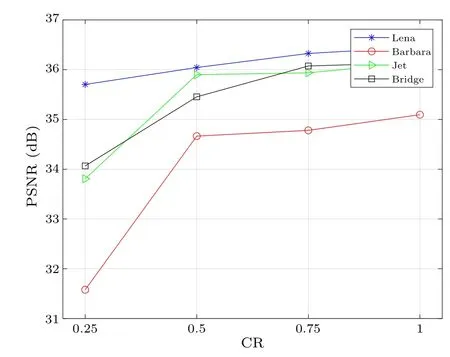
Fig.9.Influence of CR changes on PSNRdec.
Meanwhile, the quality of the decrypted image is also related to the compression ratio CR.In the PCS-based compression-encryption process, to assess the impact of CR on the decryption results, different compression ratios are set to compress the plain images.Subsequently,the generated secret images are decrypted and reconstructed for analysis.The values of CR are set to 0.25,0.5,and 0.75,respectively.Figure 9 shows the experimental results.
5.Performance analysis
5.1.Key space analysis
The security of an image encryption system is proportional to its key space.Expanding key space enhances the ability of the system to resist brute-force attacks.Typically,the key space for the image encryption scheme should exceed 2100.The keys of the proposed encryption scheme consist of the hash values and the initial keys{x',r',y',z',μ'}.Assume that the calculation accuracy of the computer is 10?14,and the size of the key space is 2256×(1014)5>2100.Moreover, if parameters such asCtr0andTSare also considered as keys,the value of key space will become larger.The results indicate that the key space of the scheme is sufficiently large to resist brute-force attacks.
5.2.Key sensitivity analysis
Key sensitivity is one of the crucial parameters for evaluating the effectiveness of an image encryption system against differential attacks.When slight modifications to the decryption key result in a decrypted image that resembles noise, it indicates that the scheme has good key sensitivity.The differences among decrypted images can be quantified by using the number of pixel change rate (NPCR) and unified average change intensity(UACI),defined as
We utilize the 512×512 sized image Peppers as plain image and Barbara as the carrier image for test.The initial keys are set tok= (x',r',y',z',μ'), and then each parameter is slightly modified to generate the incorrect keys ask1= (x'+10?14,r',y',z',μ'),k2= (x',r'+10?14,y',z',μ'),k3= (x',r',y'+10?14,z',μ'),k4= (x',r',y',z'+10?14,μ'),k5=(x',r',y',z',μ'+10?14).As shown in Fig.10, after decrypting the image using the correct keys and the modified keys respectively,it is observed that the decrypted image with the modified key resembles a noisy image.Table 3 lists the NPCR and NACI values of the cipher images with the correct key and the modified keys.
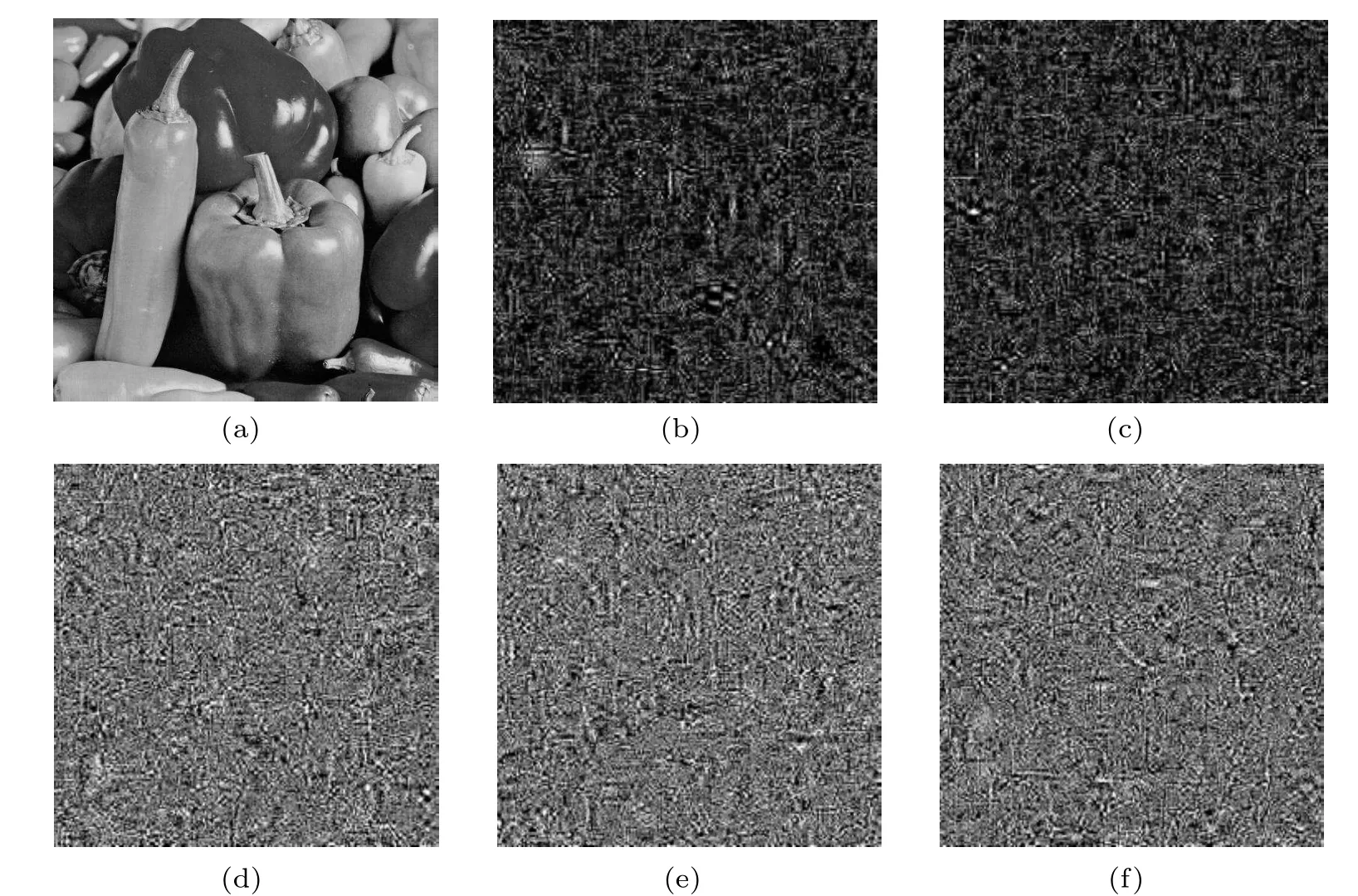
Fig.10.Key sensitivity analysis: (a) the decrypted image with the correct key; (b) the decrypted image with k1; (c) the decrypted image with k2;(d)the decrypted image with k3;(e)the decrypted image with k4;(f)the decrypted image with k5.

Table 3.The NPCR and UACI of the modified keys.
5.3.Plaintext sensitivity analysis
The strength of plaintext sensitivity measures the impact of minor changes in the original image on the encrypted image.When the image encryption algorithm exhibits strong plaintext sensitivity, small changes in the original image can lead to significant alterations in the encrypted image, which makes it challenging to predict and analyze the cipher image.To assess plaintext sensitivity,the original image is encrypted to obtain the secret image.Then,according to the equation below,we select and modify the pixel at a random position(x,y)in the original image.Subsequently,the slightly modified image is encrypted using the same key.Four different 256×256 images, four different 512×512 images, and three different 1024×1024 images are tested for 200 times and the average values are shown in Table 4.Clearly, all test values are very close to the ideal values.The proposed method is compared with others listed in Table 5,demonstrating its effectiveness in resisting various attacks.
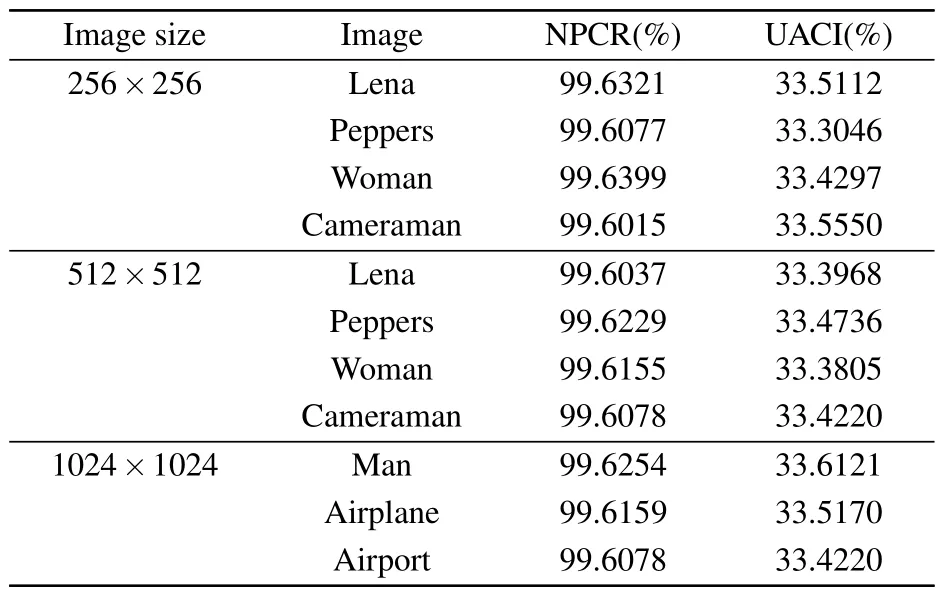
Table 4.The NPCR and UACI values of secret images encrypted from images of different sizes.
5.4.Histogram analysis
The pixel intensity values in an image can be intuitively visualized by using the histogram, which illustrates the frequency of each pixel value.An ideal image encryption algorithm should generate a secret image with a uniform histogram to effectively hide image information.Moreover, the proposed algorithm generates a cipher image with visual security,so the difference between the carrier image and the cipher image should be minimized.As shown in Fig.11,we can observe that the histograms of the secret images are uniformly distributed, and the histograms of the carrier images and the cipher images are indeed similar.This further confirms the effectiveness and robustness of the algorithm.
5.5.Information entropy
Information entropy reflects the uncertainty of image information.For a 256 grayscale level, the ideal information entropy value is 8, indicating low information visibility and superior encryption performance.The information entropy is calculated according to
wherep(mi)represents the probability ofmi,andNrepresents the gray scale level.In the test, four images are chosen for testing, including Lena, Peppers, Baboon, and Boat.Table 6 shows the information entropy values of the plain images and the corresponding secret images.As can be seen, the values of information entropy are very close to 8, demonstrating the excellent randomness of the proposed scheme.
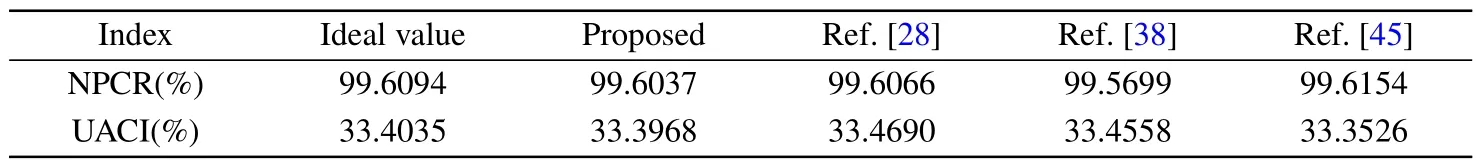
Table 5.NPCRs and UACIs of Lena(512×512)for different algorithms.
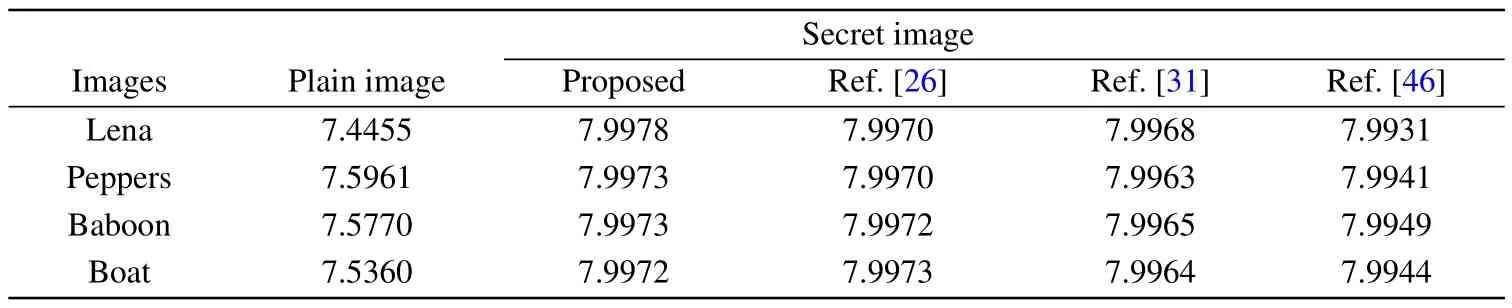
Table 6.Information entropy of plain images and secret images.
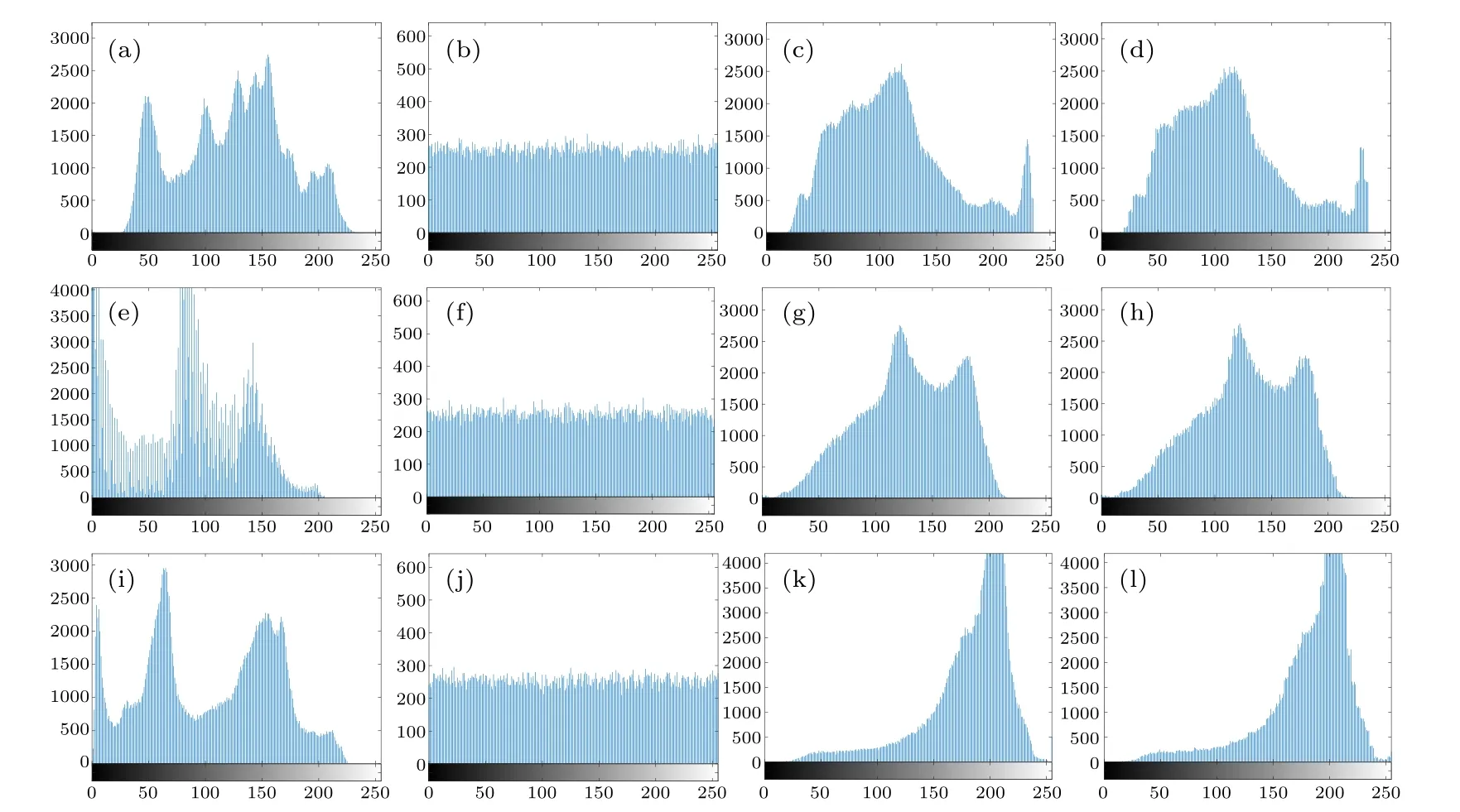
Fig.11.Histogram analysis: [(a),(e),(i)]histograms of the plain images of Lena,Girl,and Peppers; [(b),(f),(j)]histograms of the corresponding secret images;[(c),(g),(k)]histograms of the carrier images of Goldhill,Baboon,and Aerial;[(d),(h),(l)]histograms of the corresponding cipher images.
5.6.Correlation coefficients
The correlation between adjacent pixels in the original image is strong, making it susceptible to be exploited by attackers.In this experiment, the correlation coefficients are used to quantify the level of correlation between adjacent pixels in an image.It is advisable to minimize the correlation coefficients in the secret image and make them close to 1 in the steganographic image.We choose Lena and Baboon as plain image and carrier image,and 3000 pairs of adjacent pixels are randomly selected to calculate the correlation coefficients in horizontal, vertical, and diagonal directions.The equation of the correlation coefficient is defined as follows:
wherexandyare adjacent pixels.Figure 12 and Table 7 show the simulation and numerical results.In addition, the comparison with other algorithms is shown in Table 8.One can observe that there is a strong correlation between adjacent pixels in the plain image, carrier image and cipher image.Conversely,the secret image exhibits weak correlation.It is worth noting that the correlation coefficients of the carrier image and the cipher image are very close.Therefore,it is difficult for attackers to extract useful information through correlation analysis.
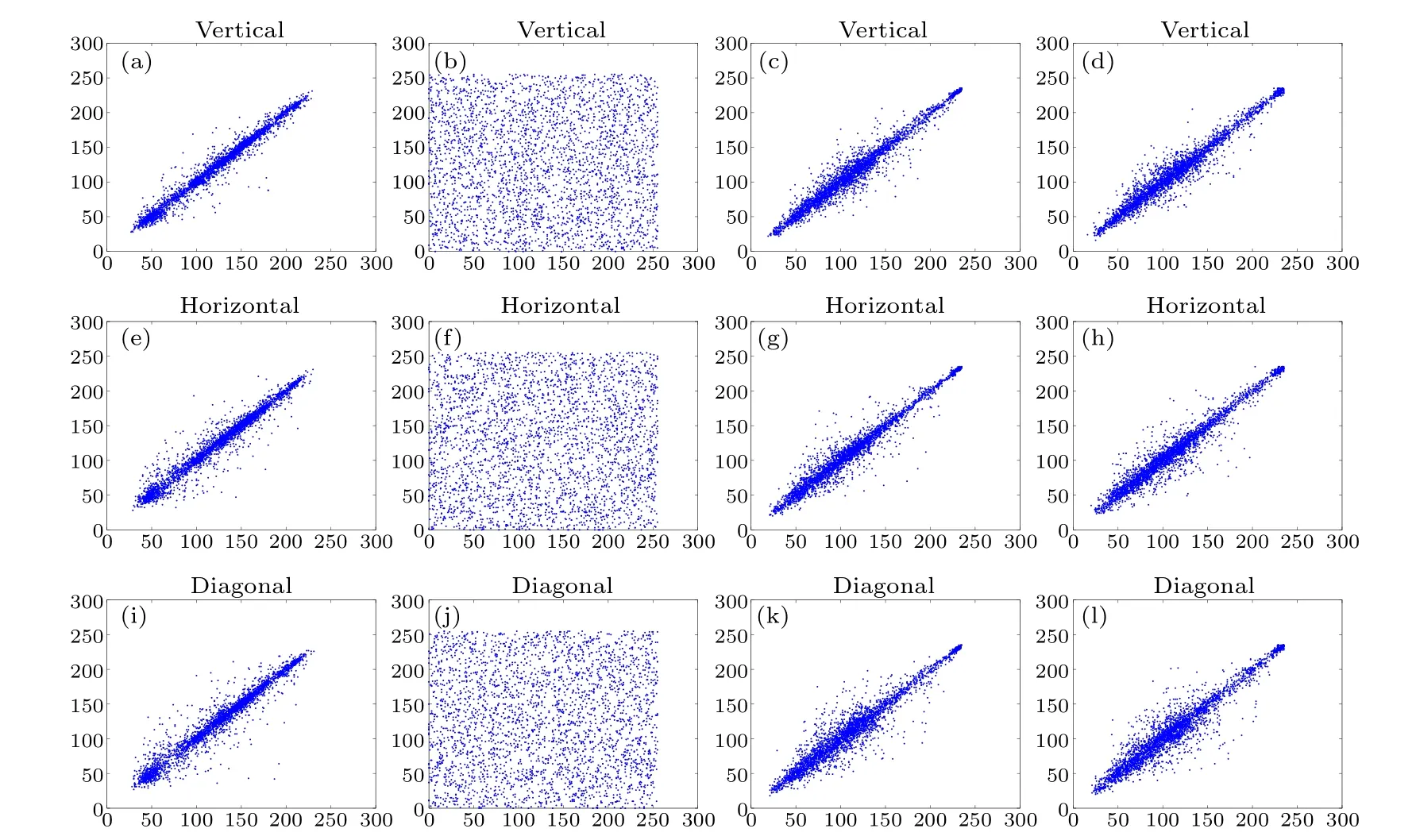
Fig.12.Correlation coefficients analysis: [(a), (e), (i)] correlation coefficients of plain image Peppers in horizontal, vertical, and diagonal directions; [(b), (f), (j)]correlation coefficients of the secret image in horizontal, vertical and diagonal directions; [(c), (g),(k)]correlation coefficients of carrier image Baboon in horizontal,vertical and diagonal directions;[(d),(h),(l)]correlation coefficients of cipher image in horizontal,vertical and diagonal directions.
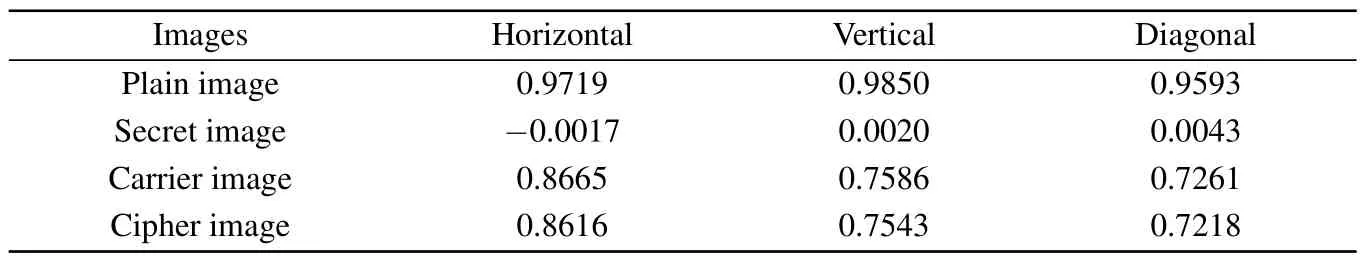
Table 7.Correlation coefficients of adjacent pixels in three directions.

Table 8.Correlation coefficients of encrypted Lena images with different algorithms.
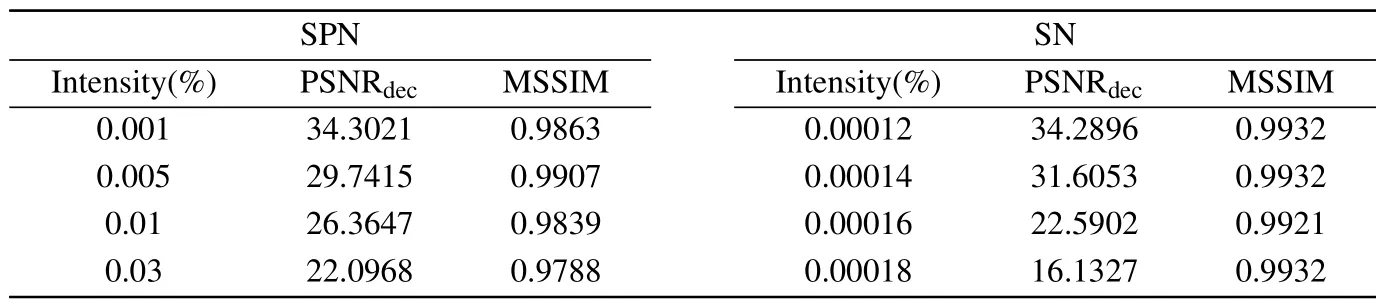
Table 9.PSNR and MSSIM values with different noise attack.
5.7.Noise attack
In the process of image transmission, the encrypted images are vulnerable to various noises that can degrade the quality of the decrypted images.In the test, we analyze the ability of the scheme to resist noise attacks.The images Lena and Bridge are selected as the plain image and the carrier image.Subsequently, the salt and pepper noise (SPN)with intensities of 0.001%, 0.005%, 0.01%, 0.03%, and the speckle noise (SN) with intensities of 0.00012%, 0.00014%,0.00016%, 0.00018% are added to the cipher image, separately.The results are shown in Fig.13.Furthermore, the PSNR and MSSIM values of the decrypted image and the plain image are listed in Table 9.From the results,we can identify the main features of the decrypted image after being attacked by the noise.Therefore,the proposed algorithm has the ability to resist the noise attack.

Fig.13.Noise attack analysis:(a)–(d)encrypted images with 0.001%,0.005%,0.01%and 0.03%SPN,respectively;(e)–(h)encrypted images with 0.00012%,0.00014%,0.00016%and 0.00018%SN,respectively.
6.Comparison with other schemes
In this section,we analyze the proposed scheme in comparison with other existing schemes,including visual security,decryption quality, and running efficiency.To ensure a fair comparison, the plain images and carrier images used in this test are identical,and the result data of the compared schemes are directly cited from the respective references.
6.1.Visual security
It is crucial to minimize the difference between the carrier image and the cipher image,which indicates that the concealment of secret information and the visual security of the algorithm are superior.The algorithm embeds secret information in the lower bits of the carrier image pixels.Since edge regions usually consist of longer pixel sequences, and such pixel sequences can hold more bits of information.Therefore,we embed more bits in the edge pixels relative to the non-edge pixels, ensuring that some non-edge pixels do not need to be embedded with any information, which can significantly improve the visual quality.
To verify the visual security of the image encryption scheme proposed in this paper,we conduct a comparison with Refs.[24,41], and evaluate the results based on PSNR and MISSIM values shown in Table 10.The proposed scheme demonstrates superior performance in these metrics.Specifically, our PSNR values are all greater than 40 dB, which is superior to other algorithms.Although the MSSIM values are slightly different from the references,the average value is around 0.99.These results indicate that the proposed scheme has excellent visual security and high-quality visual effects.
6.2.Decryption quality
In the proposed image encryption algorithm, both the threshold and quantization inherently impact the decryption quality.However, it is crucial that our scheme consistently maintains superior decryption quality.This algorithm can adequately extract secret information from the steganographic image.Moreover,the use of PCS effectively utilizes the sparsity of the signal,ensuring high reconstruction quality.In this experiment, we measured the PSNR value of the decrypted image and compared it with Refs.[24,41], as shown in Table 11.Obviously,the average PSNR value computed by our proposed scheme is greater than 35 dB,which means that our proposed scheme has outstanding decryption quality.
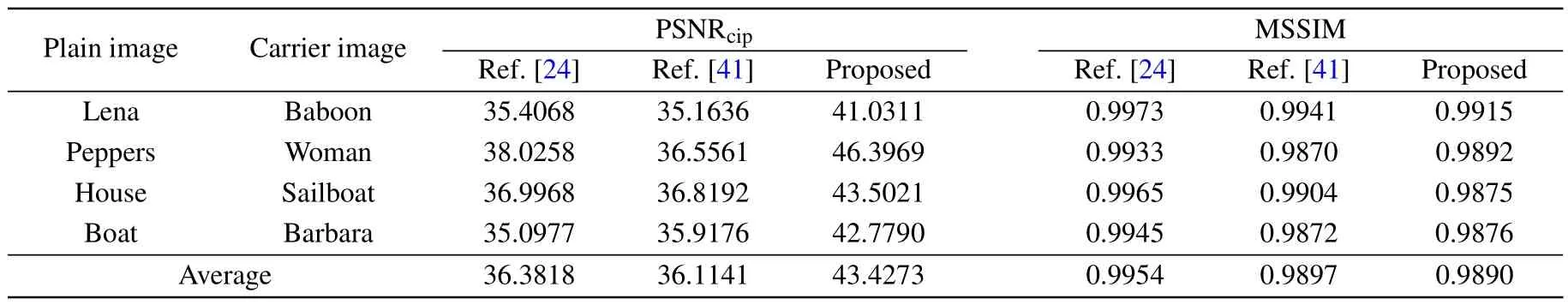
Table 10.Comparison of visual security.
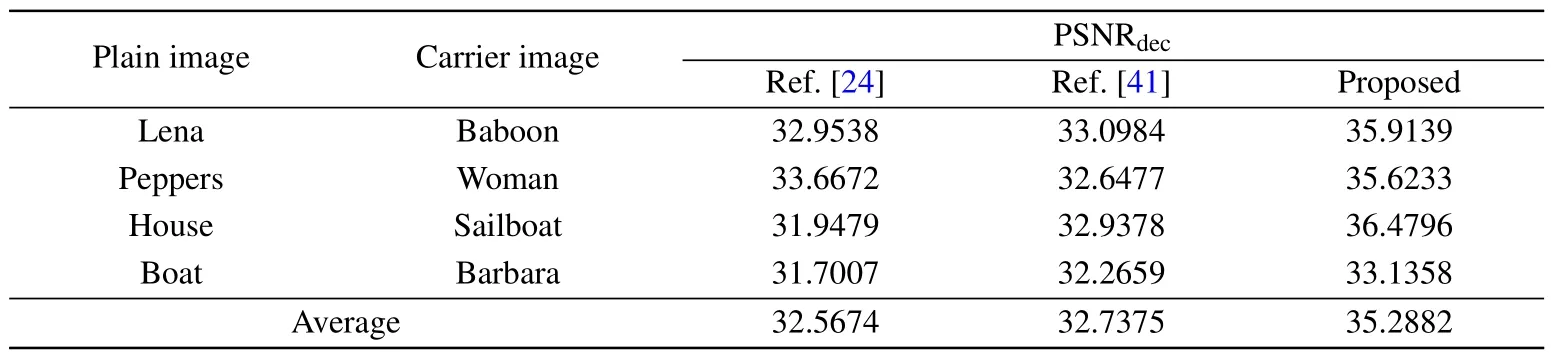
Table 11.Comparison of decryption quality.
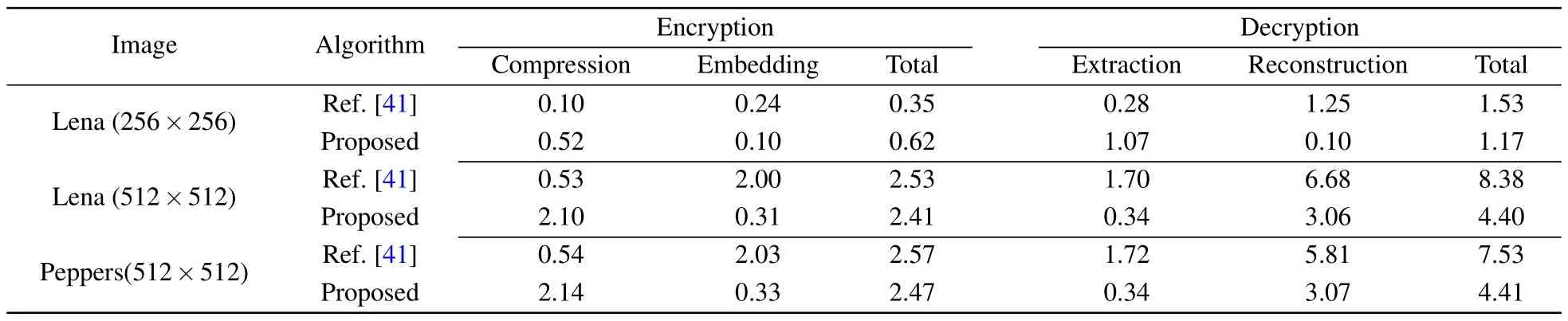
Table 12.Comparison of running time in units of second.
6.3.Running efficiency
For real-time applications, the running time of the encryption algorithm is an important performance index.In this section,we evaluate the running time required for the encryption, embedding, extraction, and reconstruction phases of the algorithm for images of different sizes, including 256×256 and 512×512.Table 12 presents the results in comparison with Ref.[41].It can be seen that in the encryption phase,the compression process takes up the majority of the time, about 87%of the total encryption time.Moreover,the running time increases with the increase of image size.In the decryption process, the extraction phase consumes less time, while the reconstruction phase needs more time.Overall,our proposed scheme requires less encryption and decryption time than the comparative literature,which runs more efficiently.
7.Conclusion
This paper introduces a novel image encryption algorithm that combines PCS and edge detection technology.The proposed algorithm utilizes PCS to optimize compression performance and reconstruction quality.It effectively scrambles the compressed image using a specific permutation method to enhance security and randomness.The edge detection embedding capitalizes on the property that image edges can accommodate more embedding bits to design a lossless embedding method to improve the visual quality of encrypted images.Moreover, the method has ability to different carrier images,which further improves security.The encryption process is closely related to the plain image and is highly sensitive to the plaintext.The simulation results and performance comparisons show that the encrypted and decrypted images perform well regarding PSNR values,indicating that the proposed image encryption scheme has excellent visual security and decryption quality.Future research will focus on improving the encryption algorithm to enhance its robustness.
Acknowledgments
This work was supported by the Key Area R&D Program of Guangdong Province(Grant No.2022B0701180001),the National Natural Science Foundation of China(Grant No.61801127), the Science Technology Planning Project of Guangdong Province, China (Grant Nos.2019B010140002 and 2020B111110002), and the Guangdong-Hong Kong-Macao Joint Innovation Field Project(Grant No.2021A0505080006).
——楊健攝影作品選登
- Chinese Physics B的其它文章
- High responsivity photodetectors based on graphene/WSe2 heterostructure by photogating effect
- Progress and realization platforms of dynamic topological photonics
- Shape and diffusion instabilities of two non-spherical gas bubbles under ultrasonic conditions
- Stacking-dependent exchange bias in two-dimensional ferromagnetic/antiferromagnetic bilayers
- Controllable high Curie temperature through 5d transition metal atom doping in CrI3
- Tunable dispersion relations manipulated by strain in skyrmion-based magnonic crystals

