A Practical E-Payment Protocol Based on Quantum Multi-Proxy Blind Signature?
Xu-Feng Niu(牛旭峰),Jian-Zhong Zhang(張建中),,? Shu-Cui Xie(謝淑翠),and Bu-Qing Chen(陳步青)
1College of Mathematics and Information Science,Shaanxi Normal University,Xi’an 710119,China
2School of Science,Xi’an University of Posts and Telecommunications,Xi’an 710121,China
3Teaching and Research Section of Political,PLA Information Engineering University,Luoyang 471003,China
AbstractA practical E-payment protocol is presented in this paper.It is based on quantum multi-proxy blind signature.Adopting the techniques of quantum key distribution,one-time pad and quantum multi-proxy blind signature,our E-payment system could protect user’s anonymity as the traditional E-payment systems do,and also have unconditional security,which the classical E-payment systems can not provide.Furthermore,compared with the existing quantum E-payment systems,this practical system could not only support mobile E-payment transactions but also inter-bank transactions.
Key words:mobile E-payment,inter-bank transaction,quantum multi-proxy blind signature,unconditional security
1 Introduction
Today,E-commerce is favored by the majority of individuals for its convenience and speediness with technological advancements. Hence,it is particularly important to choose an appropriate model of payment. In 1983,Chaum proposed the first concept of E-cash.[1]Subsequently,E-cash system has attracted much attention and researchers proposed a number of E-cash payment schemes.[2?6]However,the security of the most existing E-cash payment schemes depends on some computational problems,which may be not difficult to solve with quantum algorithms.[7?8]The application of quantum signature in E-payment has attracted much attention because that the security of quantum cryptography relies on the principles of quantum mechanics.
In 2010,Wen and Nie proposed an E-payment system based on quantum blind and group signature,employing two TTPs(Third Trusted Party)to enhance the system’s robustness.[9]In succession,Wen et al.proposed an interbank E-payment protocol based on quantum proxy blind signature.[10]However,Cai et al.[11]showed that the dishonest merchant can succeed to change the purchase information of the customer in this protocol.In 2017,Shao et al.[12]proposed an E-payment protocol based on quantum multi-proxy blind signature.However,these protocols can not be applied to the business transactions,which use mobile E-payment.In real life,there are many business transactions need mobile E-payment,such as pos terminals.And an E-payment system supports secure mobile transactions is desired from the view of practical application.
In this paper,we proposed a new E-payment protocol to solve the problem and not only support secure mobile business transactions but also secure business transactions between two different banks.In our system,quantum multi-proxy blind signature is adopted to implement mobile payment and inter-bank payment.To the best of our knowledge,this is the first time to proposed a mobile quantum E-payment scheme,which not only supports mobile payment and inter-bank payment but also enhances the transaction credibility and the success of business rate.The property of multi-proxy blind signature could protect the anonymity of E-payment system,while the quantum signature could guarantee unconditionally security.Our scheme only needs Bell state measurement,which can be easily implemented under the current experimental conditions.
2 Preliminary Theory
In this section,we introduce the basic theories of the quantum multi-proxy blind signature.
2.1 Multi-Proxy Blind Signature
Proxy signature allows a designated person,called proxy signer,to sign on behalf of an original signer.[13]As for blind signature,[14]the message owner could get the authentic signature for his own message,but not reveal the specific content of the message.In some cases,such as an inter-bank trading system,both the property of proxy and blind signature are required for application and security concern,so multi-proxy blind signature was proposed.
2.2 Controlled Quantum Teleportation
Our quantum multi-proxy blind signature is based on controlled teleportation,which takes a genuinely entangled six qubits as its quantum channel.It is given by
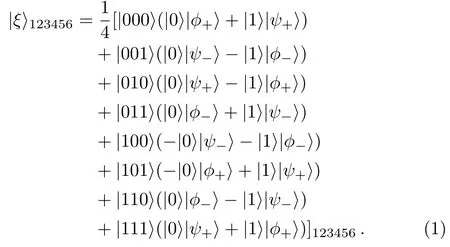
As shown in Fig.1,this controlled quantum teleportation involves the following three partners:a sender Alice,a controller Charlie,and a receiver Bob.Alice holds particle 1,Charlie and Bob own particles(2,3)and particles(4,5,6),respectively.
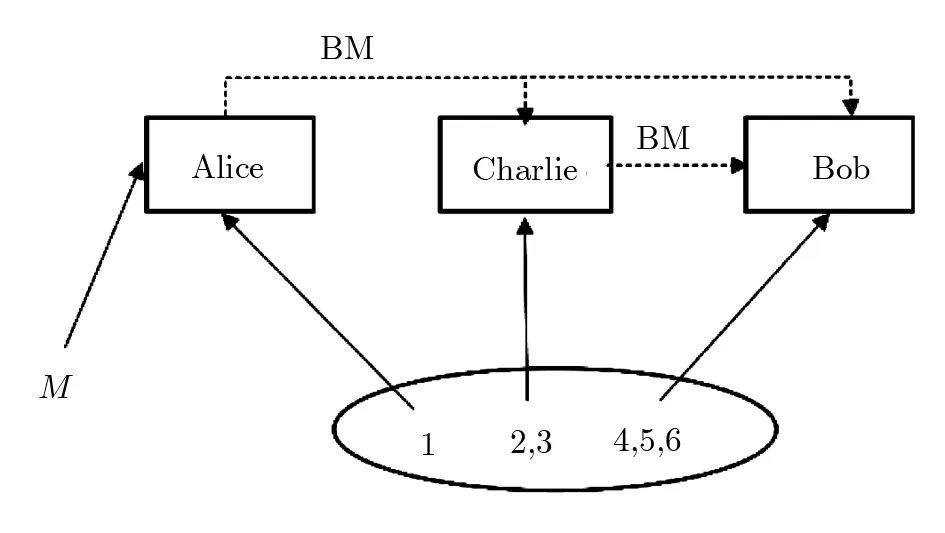
Fig.1 The model of quantum teleportation.(BM represents Bell state measurement).
Suppose that the quantum state of particle M carrying message in Alice is
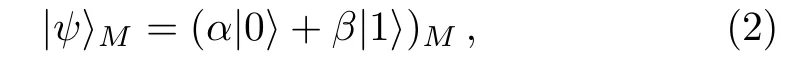
where the coefficients α and β are unknown and satisfy
The system quantum state composed of particle M and particles(1,2,3,4,5,6)are given by
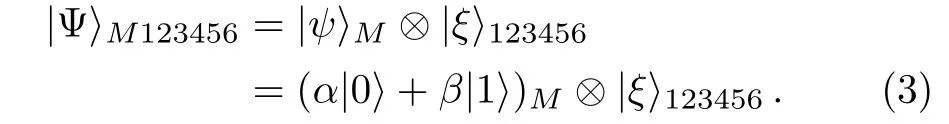
The details of the controlled teleportation are as follows.
(i)Alice performs Bell state measurement on particles M and 1.The measurement will collapse the state ofinto one of the following states


Then Alice sends her measurement result to Charlie and Bob.
(ii)If Charlie agrees Alice and Bob to complete their teleportation,he performs Bell state measurement on particles(2,3).
Suppose that Alice’s measurement outcome isand Charlie’s measurement result isandthe whole state of particles(4,5,6)will be projected into the following states,respectively.

Then Charlie sends his measurement result to Bob.
(iii)Bob performs Bell-state measurement on particles(5,6).Suppose that Alice’s measurement outcome isand Charlie’s measurement result isand Bob’s measurement result isandparticle 4 will be projected into the following states,respectively.

According to Alice’s,Charlie’s measurement outcomes,Bob performs an appropriate unitary operator on particle 4 to rebuild the original stateFor example,when particle 4 is in the state of Eq.(6),the unitary operators are ?σx,?iσy,I,σz.
3 The Practical Quantum E-payment System
To clarify our mobile quantum E-payment system, five characters are defined as follows:
(i)Alice:the customer.
(ii)Bob1:the bank where Alice opens her account.
(iii) Uj:one number of the mobile terminals(j=1,2,...,t).
(iv)Charlie:the merchant.
(v)Bob2:the bank where Charlie opens his account.
As shown in Fig.2,at the beginning of this transaction,the customer Alice informs Ujabout her purchase.Then Ujapplies to the bank Bob1 for deducting the corresponding amount of money from Alice’s account.Bob1 transfers the money to the bank Bob2 and delegates Bob2 sign to merchant Charlie,such that Charlie should receive the proper money in his account.After verifying,Charlie gives the corresponding goods to Alice.

Fig.2 Framework of the mobile E-payment system.
The detailed procedure of our scheme can be described as follows.
3.1 Initial Phase
Step 1Alice divides her purchase message into two parts:
M1(n bit),involving the amount that Alice ought to pay,information of Alice’s opening account in the bank Bob1 and Charlie’s opening account in the bank Bob2;
M2(n bit),including Alice’s detailed purchase information,which can not be seen by others.So Alice needs to blind the part M2.
Step 2Alice,Bob2 share secret keys KAC,KB2Cwith Charlie,respectively.Alice,Bob1 share secret keys KAUj,KB1Ujwith Uj,respectively.In addition,Bob1 establishes secret key KB1B2with Bob2.These distribution tasks can be ful filled via QKD protocols,which have been proved unconditionally security.[15?18]
Step 3Ujprepares Q(Q?n)EPR pairs such that
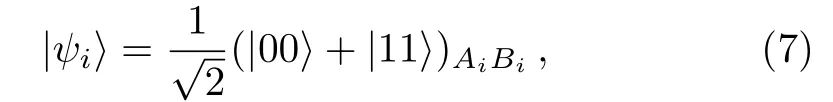
where the superscripts Aiand Biindicate the i-th of two entangled particles.And in each EPR pair,Ujsends particle Aito Alice,while he keeps particle Bi.In addition,Charlie generates TN(TN?tn)genuinely entangled six qubits states as shown in Eq.(1)to be the quantum channel.He sends particle 1 to Uj,(2,3)to Bob1,(5,6)to Bob2 while leaving particle 4 to himself.The schematic of transmission on the i-th particles is shown in Fig.3.
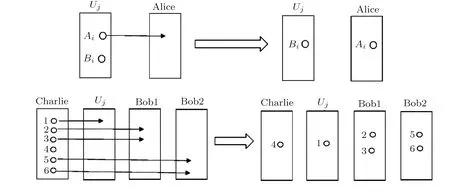
Fig.3 Schematic of transmission on the i-th particles.
Step 4To guarantee the security of the quantum channel,Charlie and Ujarrange eavesdropping checks.On the one hand,Charlie chooses TN-tn groups of particle 4 randomly,remembers the positions and performs a measurement with the basisthen Charlie publishes the positions of these chosen particles.According to Charlie’s published positions,Ujperforms measurement on the particle 1 with the basisBob1,and Bob2 respectively perform measurement on the particles(3,4)and(5,6)with the basisThen,Charlie,Uj,Bob1,and Bob2 all declare their measurement outcomes.Here,the declared order of them should be random.If their measurement outcomes satisfy the correlation of state as shown in Eq.(1)or error rate is less than the threshold value,the quantum channel is safe.Otherwise,they give up this process.On the other hand,Ujalso arranges eavesdropping check by randomly choosing Q-n EPR pairs to ensure the safety of the quantum channel between Ujand Alice.This process is similar to the above mentioned,we do not repeat the details.
3.2 Blind the Message M2 Phase
Step 1Alice measures her particle sequence according to message

where M2(i)∈{0,1}. If M2(i)= 0,she measures particle Aiwith the basisOtherwise,she measures under the basisThe measurement results can be denoted asM′2 =whereand Alice transforms the measurement results into classical binary sequencewhereThe measuring and encoding rules for quantum states are shown in Table 1.Now,message M2(n bit)could be blinded as M′′2(2n bit).
Step 2Alice gets the secret message M by encrypting M′′2 with one-time pad and key KAC,we have M=EKAC(M′′2).Alice sends M to Charlie.

Table 1 The measuring and encoding rules for quantum states.
3.3 Authorizing and Signing Phase
Step 1In order to distinguish every proxy signers,Alice generates a unique serial SN,and transforms it to a quantum state sequence|SN?in the basisThen she encryptswith key KAUj,and sends the secret state to Ujvia a quantum channel.
Step 2Alice encrypts her partial message M1 with key KAUjto get M′1 and sends it to Uj.She informs Ujthat she wants to pay the certain amount in bank Bob1 to Charlie’s account in bank Bob2.
Step 3After Ujhas receivedand M′1,he decrypts it to gainand M1.Ujperforms Bell state measurement on particles Biand 1,he gains βUj=by combining the measurement result β(i)Bi1andnow βUjis Uj’s proxy signature of the blinded message M′′2.Then Ujencrypts M1 and βUjwith the key KB1Ujto respectively get the message M′′1=EKB1Uj(M1)and SUj=EKB1Uj(βUj),he sends them to Bob1.
Step 4After receiving SUjand M′′1,Bob1 can gain Uj’s proxy request βUjand M1,he will help Ujand Charlie complete their teleportation if he agrees Ujto sign the message.Bob1 operates Bell state measurement on particles(2,3)and he combines the measurement result β(i)23withto getwhereThen he encrypts βB1jwith key KB1B2to get the message SB1j=EKB1B2(βUj,βB1j),he sends it to Bob2.If Bob1 does not agree Ujto sign the message,he terminates this teleportation.
Step 5After receiving SB1jfrom Bob1,the bank Bob2 decrypts it to gain Bob1’s proxy certificate β(i)23,βUjandBob2 operates Bell state measurement on particles(5,6)and he combines the measurement result β(i)56withto getwhereThen he encrypts βUj, βB1jand βB2jwith key KB2Cto get the message SB2j=EKB2C(βUj,βB1j,βB2j),he sends it to Charlie.
3.4 Verifying Phase
Step 1Charlie receives the secret message M from Alice,he decrypts it with his key KACto get the blinded message M′′2.
Step 2Charlie gets βUj, βB1jand βB2jby using KB2Cto decrypt SB2j.Then Charlie performs a proper unitary operator on particle 4 to rebuild the unknown state.
Step 3Based on the real message the businessman Charlie has obtained,Charlie encodes particle 4 to get a two bits classical string c(j)by using the similar strategy as shown in Subsec.3.2.If c(j)=M′′2,this signature is valid,otherwise,he rejects it.
Step 4Charlie collects

Then according to Subsec.3.2,he gets the message{c(j),j=1,2,...,t}.If c(j)=M′′2(j=1,2,...,t),Charlie will ensure the signature,otherwise,he terminates the process.
Step 5If there is no dispute,Charlie could receive the proper amount from Alice’s account and deposit it in bank Bob2 while the same amount money will be deducted from Alice’s account in bank Bob1.At the same time,Charlie should send the corresponding goods to Alice.The transaction is finished.
4 Security Analysis and Discussion
In this section,we will prove that this scheme satisfies the properties of blindness,unforgeability,undeniability,and unconditionally security.
4.1 Message’s Blindness
In the whole transaction,the message M2 has been transformed intowhereIf Ujattempts to get the message M′2,the only way is to perform measurements.However,he can not acquire M′2 and M2 because that he has no idea of Alice’s measurement basis of particle Ai.Therefore,each proxy signers can not know the content of the message M2 when he signs it.In addition,the bank Bob1 and Bob2 are kept blind from the message M2.That is,our scheme has the property of blindness.
4.2 Impossibility of Forgery
In our scheme,the bank Bob1 and Bob2 are trusty.In the following,we prove that it is impossible for anyone to forge signature.Suppose that Eve wants to forge Uj’s signature,he has to get the key KB1Uj.However,KB1Ujis distributed via QKD protocols,which have been proved unconditionally security.That is,Eve’s forgery can be avoided.Similarly,the original bank Bob1’s proxy certificate and Bob2’s signature can not be forged either.
4.3 Impossibility of Denial
In the following,we will show that our scheme is secure against the denial of both customer Alice and merchant Charlie.First of all,Alice has to encrypt her partial message M1 with the key KAUjand send it to Uj,Ujcould gain M1 to identify Alice in case of disputes.Thus,Alice can not deny her purchase message M1.In addition,according to Subsec.3.4,Charlie has to decrypt M by using his key KACto rebuild the original M2.Thus,Charlie can not deny the receipt of the payment message.
4.4 Unconditional Security
Our protocol’s unconditional security is ensured from the following aspects.First,we use the unconditionally secure QKD protocols for quantum key distribution.Second,we employ one-time pad to encrypt.Third,we arrange eavesdropping checks to achieve the secure quantum channel.
5 Conclusion
In this paper,we propose a practical E-payment protocol based on quantum multi-proxy blind signature.Compared with the previous works,[9?12]our scheme has some advantages.Firstly,our scheme could not only implement mobile E-payment but also realize the inter-bank payment.Secondly,our protocol has arranged eavesdropping checks to ensure a stronger security.Thirdly,our scheme only relies on Bell state measurement which is easy to implement with current technologies and experimental conditions.However,the received state’s fidelity may reduce because of the experimental environment,[19?20]with the development of the quantum information technique,our protocol can be applied successfully.
 Communications in Theoretical Physics2018年11期
Communications in Theoretical Physics2018年11期
- Communications in Theoretical Physics的其它文章
- Numerical Study of Unsteady MHD Flow and Entropy Generation in a Rotating Permeable Channel with Slip and Hall Effects?
- Hierarchical Human Action Recognition with Self-Selection Classifiers via Skeleton Data?
- Spin Thermoelectric Effects in a Three-Terminal Double-Dot Interferometer?
- Third-Order Magnetic Susceptibility of an Ideal Fermi Gas?
- Coherent Control of the Hartman Effect through a Photonic Crystal with Four-Level Defect Layer?
- Linear Analyses of Langmuir and EM Waves in Relativistic Hot Plasmas?
