A Non-Cooperative Differential Game-Based Security Model in Fog Computing
Zhi Li, Xianwei Zhou, Yanzhu Liu, Haitao Xu*, Li Miao
1 School of Computer and Communication Engineering, University of Science and Technology Beijing (USTB), Beijing, 100083, China
2 Great Wall Computer Software and Systems Inc., Beijing, 100190, China
* The corresponding author, email: alex_xuht@hotmail.com
I.INTRODUCTION
Cloud computing is not an independent phenomenon in the IT industry, but it has impacted the software and hardware industry.According to IDC’s latest report, public IT cloud services spending will grow to more than $141 billion in 2019, representing a compound annual growth rate (CAGR) of 19.4%[1].However, as more and more devices are connected to the network, this bliss becomes a problem for latency-sensitive and high overhead applications.Some requirements, such as mobility support, location awareness and low latency, can hardly be satisfied by cloud computing paradigm.To solve aforementioned problem, a new platform called fog computing was proposed by Cisco in 2012 [2].
Based on the perspective of Cisco, cloud computing paradigm is extended, but not exclusively, by fog computing to the edge of the network [3].Fog computing is a highly virtualized platform providing network services such as computing, storage between the end devices and cloud [4].If cloud computing is considered as a new generation of centralized computing, the fog computing is a new generation of distributed computing which targets the applications and services with widely distributed deployments.There are a number of characteristics that make the fog computing a non-trivial extension of the cloud computing,such as edge location, location awareness, low latency, geographical distribution, very large number of nodes, supporting for mobility, real-time interactions, heterogeneity, interoperability and federation [5].
The authors proposed a non-cooperative differential game theoretic framework for security of fog computing, in which the dynamics of malicious fog nodes propagation – recovery are modeled.
While fog computing makes these advantages more appealing than ever, it also brings new and challenging security threats towards its users.Since smart devices are deployed in the places where is out of strict monitoring and protection, fog nodes, as a platform close to the end users, might encounter a variety of system security challenges.On the other hand,fog computing supports distributed virtual environment, multi-user and multi-domain platform, from a security perspective, it is more prone to security threats and vulnerabilities,which attract malicious users to attack it.Some traditional attacks such as eavesdropping, data hijacking etc., may successfully threat to the fog devices for its malicious purpose.Unfortunately, it is hard to lay out the security strategy and constitute all the dynamic behavior in design and execution time, which causes a loss of security control over fog service resource.
Differential game derives from optimal control theory and game theory, which belongs to one most practical and complex branch of game theory, proposed by Isaacs [6].In fact, differential game has already been used to study the relationship between resource and energy consumption in different network environments, such as the Internet of Things[7], deep space [8].According to the profit functions and the relationships (cooperative or non-cooperative) between the players, it can solve those dynamic strategies which evolves over time [9].In this case, differential game theory can provide a mathematical framework for modeling and analyzing fog computing network security issues.
In this paper, by introducing the differential game theory, a fog security model based on non-cooperative differential game was proposed.The behavior of malicious fog nodes propagation - recovery was evaluated.The interactions and the optimal strategy of energy consumption with QoS guarantee were also analyzed.Our main contributions in this paper can be summarized as follows: (1).Based on the traditional epidemic theory, we model the dynamics of malicious nodes propagation -recovery in fog computing, in which dynamics of each state is attained.(2).We model the fog security strategy based on non-cooperative differential game.In this model, we analyze the dynamic interactions between rational players (vulnerable fog nodes and malicious fog nodes) with conflicting interests during the malicious nodes propagation- recovery process, which takes place in continuous time.(3).By solving the feedback Nash equilibrium solution, we quantify costs corresponding security risks, which provide a basis for future analysis of the process of malicious fog nodes propagation- recovery.(4).We analyze the optimal strategy of energy consumption with QoS guarantee.Through simulations, we show the change of optimal strategy which is impacted by the malicious nodes propagating or recovery.
The rest of this paper is organized as follows.The related work is explained in Section II.The differential game is constructed and its solution to the proposed game is derived in Section III and Section IV.Simulation results are presented in Section V.Conclusions of the work are brought in Section VI.
II.RELATED WORKS
The concept of fog computing was firstly proposed by Cisco in 2012 [10].The research on fog computing still remains at a very early stage.However, similar system known as edge computing such as Cyber Foraging [11] and Cloudlet [12] can data back to 2000.Cisco introduced this new term to make the data transfer easy in distributed environment [13].Bonomi et al.[14] identify that fog is nothing but cloud that is closer to the ground.Hence this kind cloud computing which is closer to the end users’ networks is thus named as fog computing.Fog computing can provide better QoS (Quality of Service) in term of delay, energy consumption etc.
In recent years, several research works that propose concept and application for fog computing have been proposed.K.Hong et al.proposed mobile fog in [15].This high level programming model is for large–scale, latency–sensitive applications in the Internet of Things.It allowed applications to scale based on their workload using on-demand resources.According to the logical structure of this paper, low-latency processing occurs near the edge, while latency tolerant large-scope aggregation is performed on powerful resources in the cloud.In this way, it has reduced the delay and network traffic in the networks.Stantchev V et al.[16] presented a three-level architecture for a healthcare infrastructure which was based on a service-oriented architecture.The proposed architecture can be used as a basic design for future high quality smart healthcare services.J.Zhu et al.[17] used web page optimization methods in fog computing architectures.These methods can have the information of the fog nodes to optimize the network performance.With network edge specific knowledge, users’ webpage rendering performance is improved.Ottenw?lder B et al.[18] presented a placement and migration method for fog and cloud resource.This method ensures application-defined end-to-end latency restrictions.By planning the migration ahead of time, it also reduces the network utilization.In paper[19], a Steiner tree based caching scheme was proposed to analyze the resources sharing or caching in the Fog cluster.By producing a Steiner tree to minimize the total path weight,the cost of resource caching using this tree could be minimized.
More and more attention has been paid to the importance of the fog computing security.Several potential security and privacy problems in fog computing, such as Man-in-the-middle Attack and Intrusion Detection, are presented in [20].Stojmenovic I et al.[21] discussed the system security in fog computing by studying man-in-the-middle attack.In their research, the stealthy features of the attacks were investigated by monitoring CPU and memory consumption on Fog devices.In addition, the authentication and authorization techniques that can be used in fog computing were also discussed.Lee K et al.[22] explored the components and the several unique security threats of IoT fog.As one of the potential threats, malicious fog node problem was proposed.In their research,the heavy workloads in fog computing will be divided into several jobs and processed by fog nodes.If some of these fog nodes were compounded by malicious users, it is hard to ensure the security of the data.However, the paper does not give a detailed solution to solve these security problems.In this paper, we will focus on the propagation of malicious nodes in fog computing.A non-cooperative differential game-based security model in fog computing and its optimal strategy will be introduced in the following sections.
II.SYSTEM MODEL AND PROBLEM STATEMENT
Firstly, a three-level hierarchy of fog computing is given in Fig.1.In this framework, there are three main elements in the fog computing:(a) smart devices, (b) fog nodes and (c) cloud.Each smart device is attached to one of the fog nodes.Each of fog nodes is linked to the cloud,and fog nodes could be interconnected.Smart devices have a large variety of sensors and local data.However, it is very expensive and time-consuming to send all of data from terminal smart devices to the cloud through the high latency network.In fog computing, smart devices will connect to fog nodes through a shortrange communication, such as WiFi, Bluetooth.Compared with the smart devices, the fog nodes have more memory or storage ability for computing, which make it be possible to process a significant amount of data from smart devices.On the other hand, those processes which need more computing power will be sent to the cloud from fog nodes through high-speed wireless or wire communication.
We assume that the number of fog nodes in fog computing at time isThe states of fog nodes, due to their own characteristics, can be classified into the following two classes:
Vulnerable nodes (V): Fog nodes in Class V are those nodes which are working and vulnerable to be attacked by malicious nodes.
Malicious nodes (M): Fog nodes in Class M are those nodes which have been contaminated by malicious attacks and may infect Class V nodes nearby.
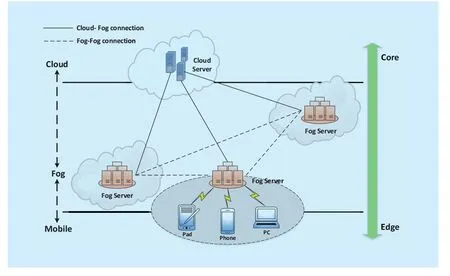
Fig.1 The fog computing architecture
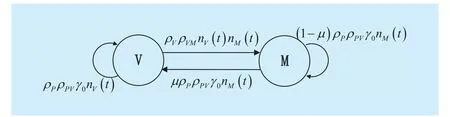
Fig.2 Dynamics of two states
Now we consider the change of fog computing network while transmitting the security patches.The total number of security patches isThe number of security patches for Class V and Class M fog nodes is respectively denoted byandwhereLet the nodes fetch security patches at an overall ratewhere parameterdepends on fog node density, transmission rates etc.is a control parameter which is used to regulate the network resource consumption,andIt is also a function ofThe higher value ofthe higher is theLetwhereis the represents a linear relationship between the energy consumption with QoS and
If a fog node in Class V gets the security patch, this node will be safe for some specific malicious attacks.However, since the patch can only define certain kinds of malicious attacks, this fog node is still vulnerable.If a fog node in Class M gets the security patch, this node will be healed or not, since the malicious attack may prevent it.The above possible could be captured by introducing a coefficientwhereWhenthe security patch is unable to heal the malicious nodes by removing the malicious process.Whereasmeans that patch is able to fully heal the malicious nodes.
Fig.2 illustrates the transitions between vulnerable and malicious states of fog node.According to the above discussion, the rates of changes of Class V and Class M fog nodes can be written as following:
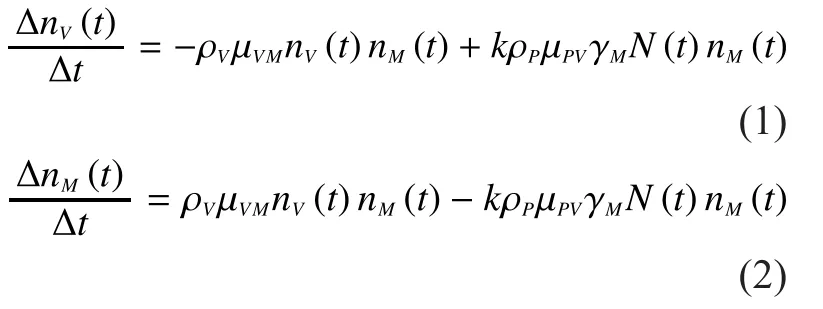
The rate of changes of Class V nodes after get security patches is
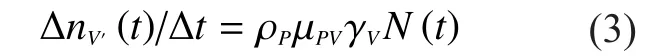
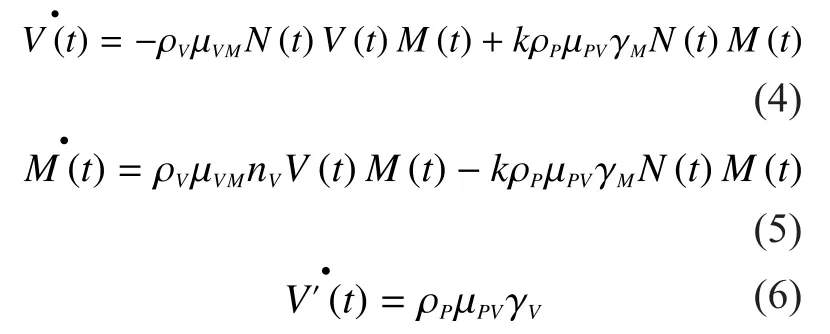
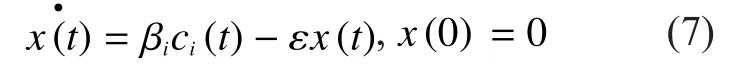
β, ε are positive parameters.βis the amount cost parameter created by energy consumption with QoS guarantee.The undesired cost is decreased in a rateεwith the change of system.
From the security perspective, the overall revenue of fog computing network is the sum of profits from the increase of Class V nodes and the enhancement of the security level of the original Class V nodes.And the cost is the sum of the consumption from security patches and the energy of transferring these security patches.Since the energy consumption with QoS are different, the instantaneous price of each fog node is also different.In general, the unit price function is a linear function ofand can be defined as
The differential game model of the profit function for Class V fog nodes is governed by the following equation
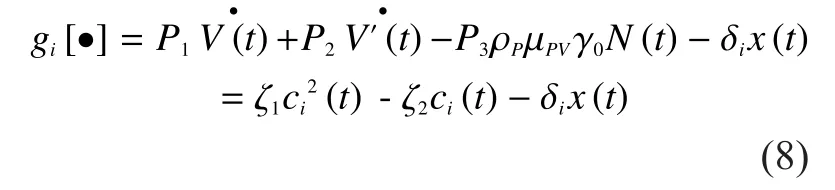
where
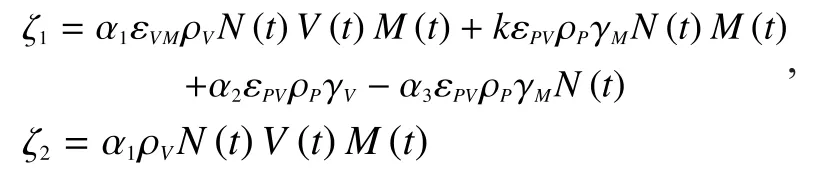
Using the method proposed in [6], according to the discussion above, the dynamic optimization and the differential equation are shown as
引致手足搐搦癥患者發(fā)病的主要原因,在于患者細(xì)胞外液環(huán)境中以離子形式存在的鈣元素?cái)?shù)量顯著減少,且在此基礎(chǔ)上誘導(dǎo)患者的神經(jīng)系統(tǒng)興奮程度顯著加劇,血液環(huán)境中的鎂元素?cái)?shù)量顯著降低,繼而出現(xiàn)病理性癥狀[5-6]。
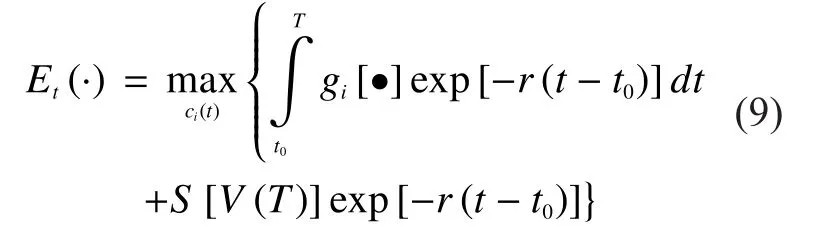
IV.FEEDBACK NASH EQUILIBRIUM SOLUTION
In this section, the feedback Nash equilibrium solution to the differential game is discussed.The game was solved by dynamic optimization program technique which has been developed by Bellman [6] and is given in Theorem 1.
Theorem 1A set of strategiesprovides a Nash equilibrium solution to the differential game (10) if there exist continuously differentiable functionsdefined onand satisfying the following Bellman equation (11)
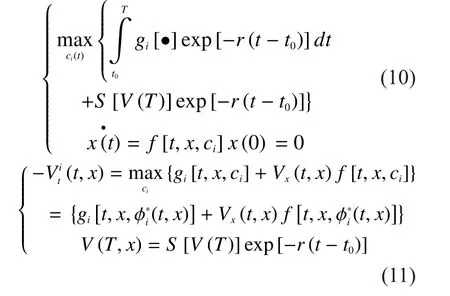
In this case,xandtdenote the state and time respectively.is the value function of fog nodeiin time intervalThe value functionis represented as follows.
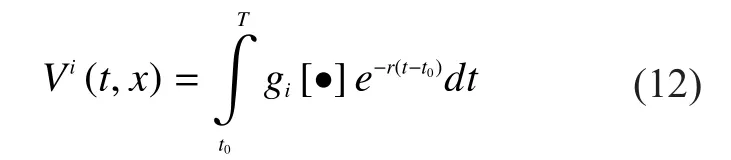
According to Theorem 1, we have
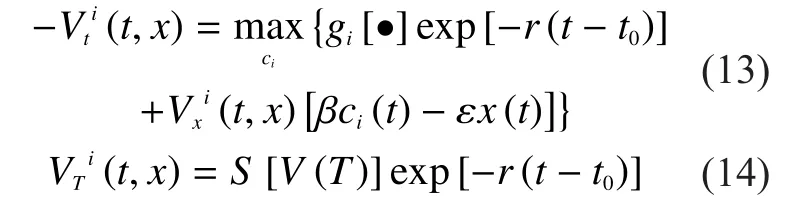
Calculate the partial derivative forin the formula (11) and make it equal to 0, then we can obtain
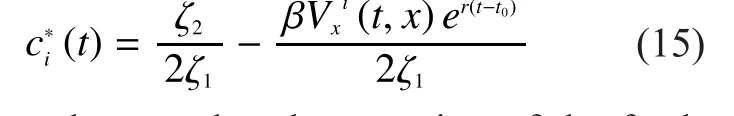
In order to solve the equation of the feedback Nash equilibrium solution, we assumecould be expressed as
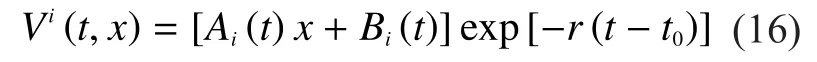
By taking the derivative ofwith respect to t, we obtain
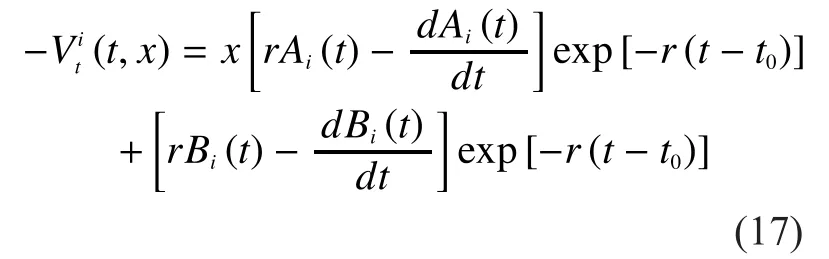
Then, by taking the derivative ofwith respect to x, we obtain
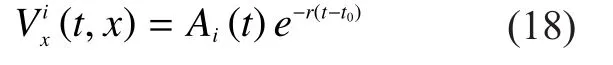
We substitute (18) into (12),
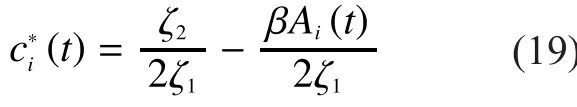
Then we substitute (19) to (13) to get
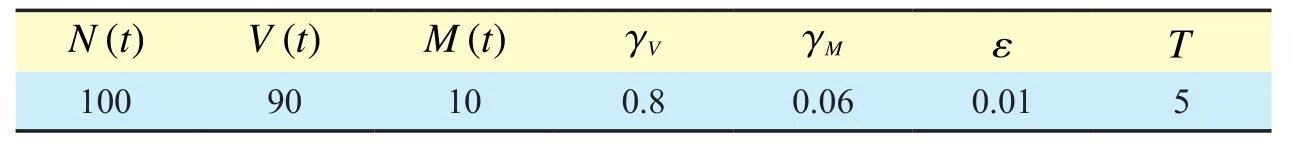
Table 1.a The setting of simulation parameter
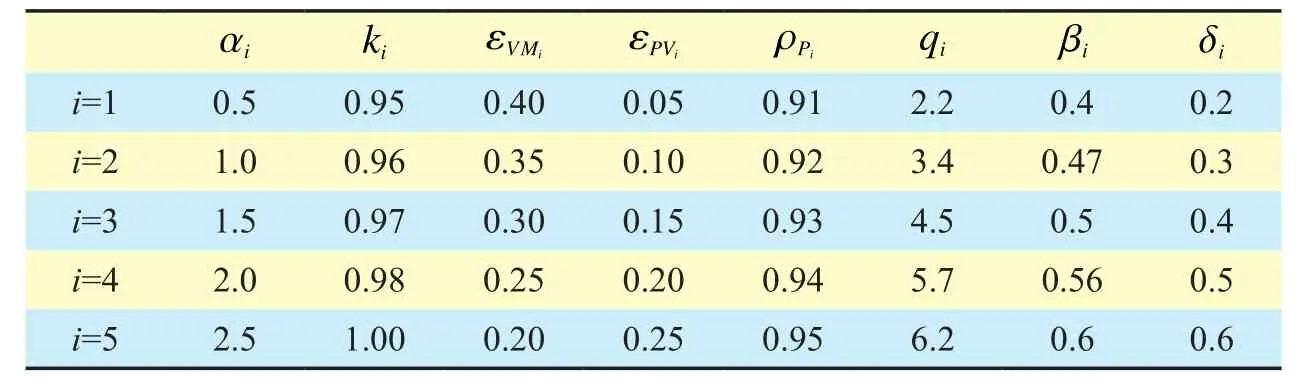
Table 1.b The setting of simulation parameter
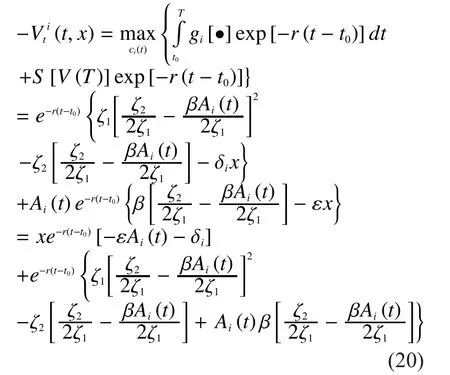
According to (17), we obtain
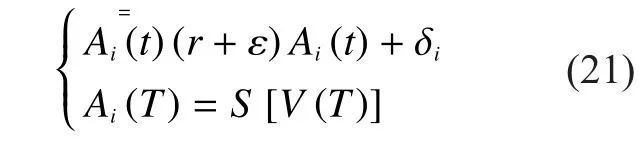
Solving (21), we have that

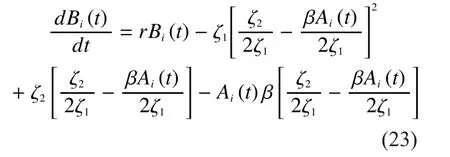
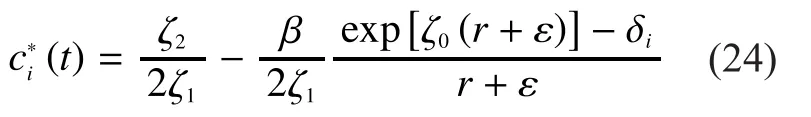
Where

V.NUMERICAL SIMULATION AND ANALYSIS
In this section, a numerical analysis is presented to help understand the concepts of proposed differential game security model.We consider a scenario with 100 fog nodes.The number of Class V nodes and Class M nodes are 90 and 10, respectively.We choose 5 Class V nodes to simulate the security game model with different values of parameter, which are shown in Table 1.The parameters set are shown in Table 2.
In the first example, we simulate the parameterwhich will impact the optimal strategydirectly.Fig 3 displays the variation ofvarying with timeof five fog nodes with different states.It can be found thatis increased with time varying from 0 to 5.The different parameters, such asand so on, have significant effect on the variation of
Fig.5 shows the relationship between optimal strategyand the time t.Fig.6 depicts the relationship between optimal strategyand the different discount rate.It can be seen that the optimal QoS guarantee resources for security of fog computing network cloud decrease with time varying and be less affected by discount rate.
In fog computing network, with the transmission of security patches, the malicious fog nodes are constantly healed.The potential risk of vulnerable fog nodes will be reduced, the corresponding QoS resources can also be appropriately reduced.
VI.CONCLUSION
Fog computing extends cloud computing and services to the edge of the network.With the rich potential applications in both wireless network and Internet-of-things, the fog computing also opens broad research issues on network security, resource management, big data and novel service delivery.It gives new opportunities and challenges to network operators and users.The purpose of this article is to investigate on the design goals and main motivation of fog computing from the security perspective.By depicting three-level hierarchy, the architectureand the main components of fog computing are introduced.We have proposed a non-cooperative differential game theoretic framework for security of fog computing, in which the dynamics of malicious fog nodes propagation –recovery are modeled.By solving the feedback Nash equilibrium solution, we quantify costs corresponding security risks, and analyze the optimal strategy of energy consumption with QoS guarantee in fog computing.Experimental results have shown the effects of various parameters on the optimal strategy, which can help the fog make the optimal dynamic strategies when different types of nodes dynamically change their strategies.
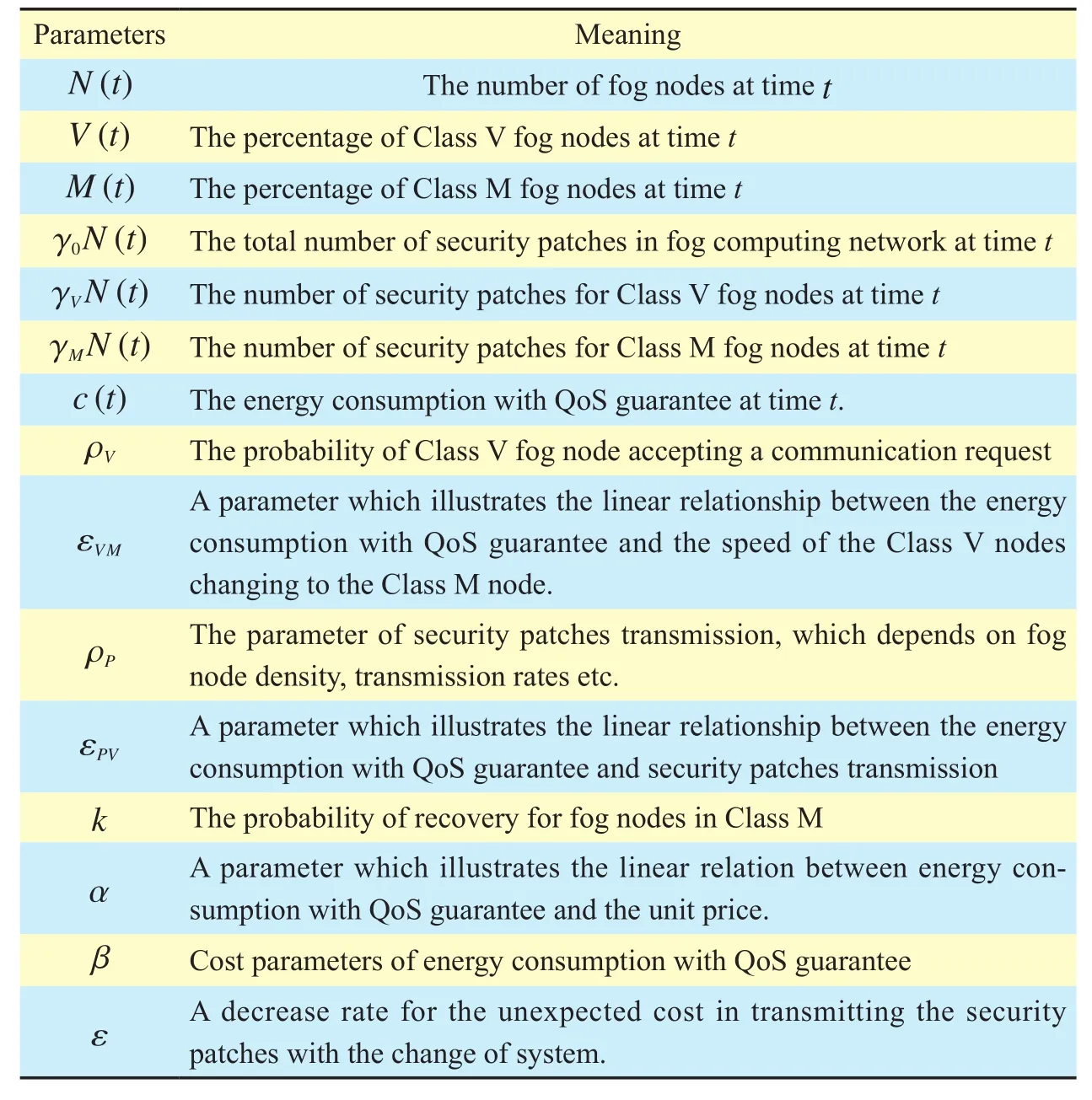
Table 2 Parameters table
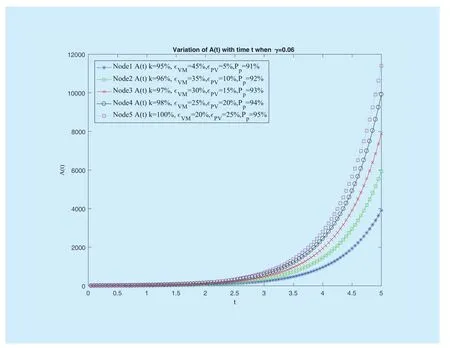
Fig.3 The variation of A(t) with t when γ=0.06
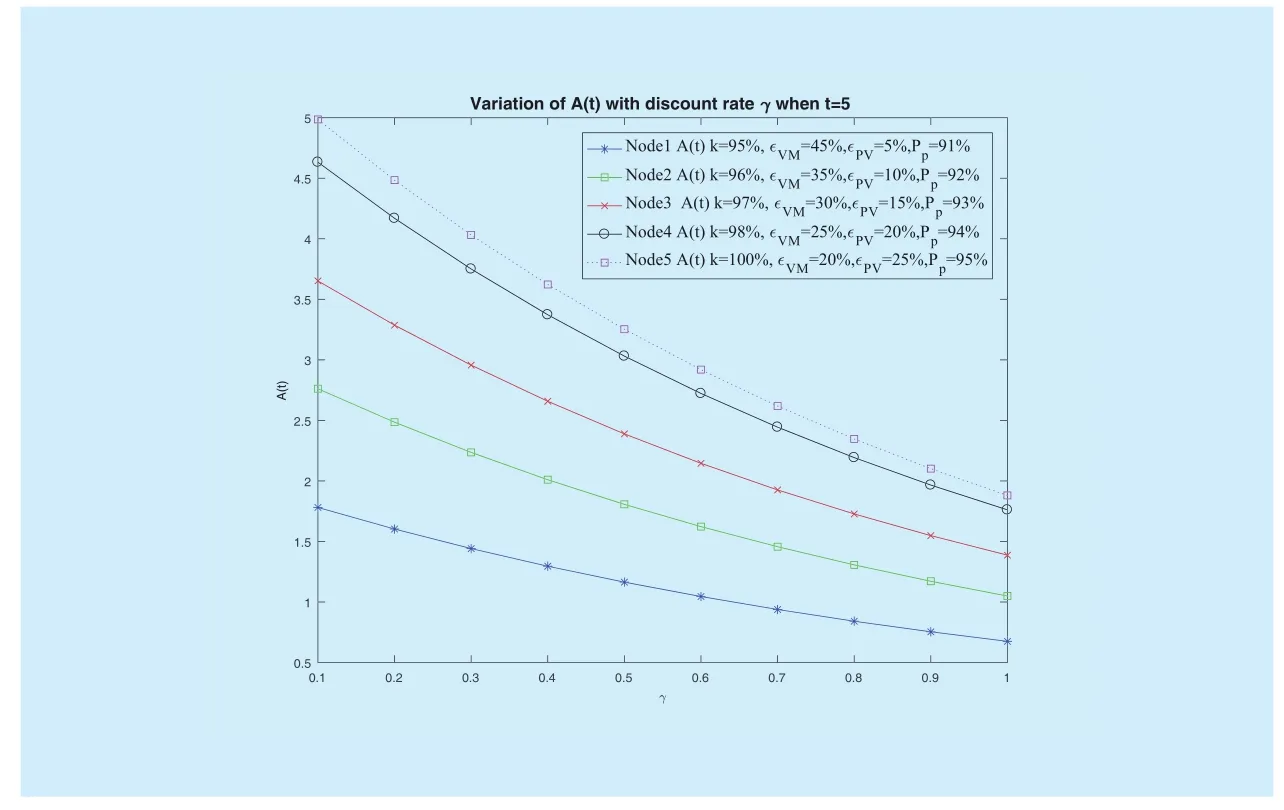
Fig.4 The variation of withwhen

Fig.5vary trends with time when
Fig.6vary trends with when
ACKNOWLEDGEMENTS
The authors would like to thank the reviewers for their detailed reviews and constructive comments, which have helped improve the quality of this paper.This paper is supported by the National Science Foundation Project of P.R.China (No.61501026,61572072), and Fundamental Research Funds for the Central Universities (No.FRF-TP-15-032A1).
[1] IDC Analyze the Future, “Worldwide Public Cloud Services Spending Forecast to Double by 2019, According to IDC”, January, 2016,https://www.idc.com/getdoc.jsp?container-Id=prUS40960516
[2] Luan T H, Gao L, Li Z, et al.Fog computing: Focusing on mobile users at the edge, arXiv preprint arXiv:1502.01815, February, 2015.
[3] Firdhous M, Ghazali O, Hassan S.“Fog Computing: Will it be the Future of Cloud Computing?”//Third International Conference on Informatics& Applications, Kuala Terengganu, Malaysia, pp 8-15, October, 2014.
[4] Song F, Huang D, Zhou H, et al.An optimization-based scheme for effi cient virtual machine placement, International Journal of Parallel Programming, vol.42, no.5, pp 853-872, 2014.
[5] Kumar V A, Prasad E.“Fog Computing: Characteristics, Advantages and Security-Privacy”,International Journal of Computer Science and Management Research, vol.3, no.11, 2014.
[6] Isaacs R.“Differential Games I: Introduction”,RAND CORP SANTA MONICA CA, 1954.
[7] Lin F.H., Liu Q., Chen Y.Y., Zhou X.W., Huang D.C., “Cooperative Diff erential Game for Model Energy-Bandwidth Efficiency Tradeoff in the Internet of Things”, China Communications, vol.11, no.1, pp.92-102, 2014.
[8] Lin F.H., Liu Q., Zhou X.W., Xiong K., “Towards Green for Relay in InterPlaNetary Internet Based on Differential Game Model”, SCIENCE CHINA Information Sciences, vol.57, no.4, pp 1-9,2014.
[9] Yeung D W K.“Dynamically consistent cooperative solution in a differential game of transboundary industrial pollution”, Journal of optimization theory and applications, vol.134,pp 143-160, July, 2007.
[10] Saharan K P, Kumar A.“Fog in Comparison to Cloud: A Survey”, International Journal of Computer Applications, vol.122, no.3, pp 10-12,July, 2015.
[11] Balan R, Flinn J, Satyanarayanan M, et al.“The case for cyber foraging”//Proceedings of the 10th workshop on ACM SIGOPS European workshop, ACM, pp 87-92, July, 2002.
[12] Satyanarayanan M, Bahl P, Caceres R, et al.“The case for vm-based cloudlets in mobile computing”, Pervasive Computing, IEEE, vol.8, no.4,pp14-23, October, 2009.
[13] Zao J K, Gan T T, You C K, et al.“Pervasive brain monitoring and data sharing based on multi-tier distributed computing and linked data technology”, Frontiers in human neuroscience, vol.8, June, 2014.
[14] Bonomi F, Milito R, Zhu J, et al.“Fog computing and its role in the internet of things”//Proceedings of the first edition of the MCC workshop on Mobile cloud computing, ACM, pp.13-16, August, 2012.
[15] Hong K, Lillethun D, Ramachandran U, et al.“Mobile fog: A programming model for largescale applications on the internet of things”//Proceedings of the second ACM SIGCOMM workshop on Mobile cloud computing, ACM, pp 15-20, August, 2013.
[16] Stantchev V, Barnawi A, Ghulam S, et al.“Smart Items, Fog and Cloud Computing as Enablers of Servitization in Healthcare”, Sensors & Transducers, vol.185, no.2, pp 121-128, February,2015.
[17] Zhu J, Chan D S, Prabhu M S, et al.“Improving web sites performance using edge servers in fog computing architecture”//Service Oriented System Engineering (SOSE), 2013 IEEE 7th International Symposium on.IEEE, pp 320-323,March, 2013.
[18] Ottenw?lder B, Koldehofe B, Rothermel K, et al.“MigCEP: operator migration for mobility driven distributed complex event processing”//Proceedings of the 7th ACM international conference on Distributed event-based systems, ACM,pp 183-194, June, 2013.
[19] Su J, Lin F, Zhou X, et al.“Steiner tree based optimal resource caching scheme in fog computing”, Communications, China, vol.12, no.8,pp161-168, August, 2015.
[20] Mandlekar V G, Mahale V K, Sancheti S S, et al.“Survey on Fog Computing Mitigating Data Theft Attacks in Cloud”, International Journal of Innovative Research in Computer Science &Technology (IJIRCST), vol.2, no.6, November,2014.
[21] Stojmenovic I, Wen S, Huang X, et al.“An overview of Fog computing and its security issues”,Concurrency and Computation: Practice and Experience, vol.28, issue 10, April, 2015.
[22] Lee K, Kim D, Ha D, et al.“On security and privacy issues of fog computing supported Internet of Things environment”//Network of the Future(NOF), 2015 6th International Conference on the,IEEE, pp1-3, 2015.
- China Communications的其它文章
- Dynamic Weapon Target Assignment Based on Intuitionistic Fuzzy Entropy of Discrete Particle Swarm
- Directional Routing Algorithm for Deep Space Optical Network
- Offline Urdu Nastaleeq Optical Character Recognition Based on Stacked Denoising Autoencoder
- Identifying the Unknown Tags in a Large RFID System
- Reputation-Based Cooperative Spectrum Sensing Algorithm for Mobile Cognitive Radio Networks
- Toward a Scalable SDN Control Mechanism via Switch Migration

