Reputation-Based Cooperative Spectrum Sensing Algorithm for Mobile Cognitive Radio Networks
Xinyu Wang, Min Jia, Qing Guo*, Xuemai Gu, Guangyu Zhang
1 Communication Research Center, Harbin Institute of Technology, Harbin 150080, China
2 Research Center of Satellite, Harbin Institute of Technology, Harbin 150080, China
* The corresponding author, email: qguo@hit.edu.cn
I.INTRODUCTION
Cognitive radio (CR) is able to mitigate the spectrum scarcity problem by using opportunistically licensed spectrum bands in dynamic spectrum access networks [1].Thus, spectrum sensing is the essential to CR [2].Spectrum sensing has attracted considerable attentions and a variety of sensing schemes have been proposed [3-6].Spectrum sensing consists of single-node sensing and multi-node cooperative sensing.But the detection performance of the former is largely affected by hidden terminal problem, channel fading effects and multipath effects [7].Thus, studies on the latter are more significant.However the latter is easily attacked by malicious users (MUs).
Final decisions made by the fusion center(FC) can be significantly affected by the fake detected results uploaded by malicious users.In view of this, existing solutions aiming to remove malicious users were introduced in [8-10].Basically speaking, the core idea of those algorithms was to introduce a variable called trust value.A secondary user’s trust value was decreased if its local detected results deviated from common readings beyond a certain threshold.And it would cause the consequence that it was identified as a malicious user.Then its negative effects on the final decision would be weaken.Conventional trust-value-based algorithms (CTAs) in this paper represent a type of algorithms with characteristics described above.However, those CTAs had the following limitation.They failed to consider the mobility of secondary users.Nevertheless, mobility was an essential feature of mobile communications networks.To be specific, those CTAs failed to consider the location diversity of the cognitive radio network (CRN) and thus always overly punished those minority reliable users(RUs) in extremely bad or good locations and even when they moved out of those locations later on, its contribution to the final decision was still limited because of its low trust value,causing the detection performances to decrease greatly.Thus, the CTAs were not able to be directly applied to mobile CRNs.So far, studies on malicious attacks in mobile CRNs are rather limited.We find the following several relevant papers.The algorithm in [11] must detect many times to achieve the requested accuracy causing interference to the primary user.Reference[12] assumed that the primary user’s (PU’s)communication range was limited within a sub-region of the CRN.Thus, its application scenarios were different from our algorithm.And it was lacking for theoretical derivations,which meant it did not theoretically prove their algorithm’s effectiveness.A trusted collaborative spectrum sensing for mobile CRNs(TCSS) was proposed in [13] aiming at mobile secondary users (SUs).In TCSS, trust value was computed based on Dempster-Shafer (DS) Theory.However, because of the limitation of the particular D-S iteration formula those authors had selected, trust values were not accurate enough to remove malicious users according to our analysis and simulated results in Section IV.
In this paper, the authors proposed a reputation-based cooperative spectrum sensing algorithm for mobile CRNs to resist malicious attacks.
In this paper, a reputation-based cooperative spectrum sensing algorithm (RCSS) is proposed to identify and remove malicious attacks in mobile CRNs, which consists of two main parts, updating reputation scores to remove malicious users and data fusion in the fusion center to improve detection performance further.Also, we propose the idea of “slide window” to enhance the stability of our algorithm.When calculating the common reading of each cell, the average of detected results in it needs to be computed.Thus the bigger the total number of results involved, the more accurate the obtained common reading will reflect the true channel conditions of this cell.The idea of “slide window” means during each spectrum sensing, we not just process detected data in the current sensing slot, but all data of the latest several slots to increase the amount of data involved and thus enhance the accuracy and reliability of our algorithm.Then, we verify the effectiveness of our malicious user removing method and the superiority of the data fusion rule at a theoretical derivation level.Finally, the simulation results are presented to verify that the detection performance of RCSS is significantly better than that of CTA and TCSS.
The major contributions of this paper are:
? Taking into consideration both the mobility of secondary users and local channel differences, we propose a reputation-based cooperative spectrum sensing algorithm consisting of two main parts, identifying malicious users and data fusion.
? We propose an idea of “slide window” to increase the number of detected results during each iteration to enhance our algorithm’s stability and accuracy.
? We study the detection performance of our proposed algorithm and verify its effectiveness at a theoretical derivation level.
? We conduct simulations to evaluate our algorithm and compare its detection performance with other algorithms, finding that in CRNs with 60 mobile SUs, among which, 18 are MUs, our solution has an improvement of detection probability by 0.97-dB and 3.57-dB when false alarm probability is 0.1, compared with CTA and TCSS, respectively.
II.SYSTEM MODEL
2.1 Cognitive radio network model
In real-world scenarios, some areas have better channel conditions, i.e.larger signal-to-noise ratios (SNRs), and others have worse because of shadow fading, path loss and multi-path effects in the entire large-sized area of interest.CTAs tend to overly punish those minority RUs who move into locations with extremely good or bad channel conditions and even mistakenly remove them.Thus conventional trustvalue-based algorithms can no longer apply in mobile CRNs.Aiming this challenge, we adequately consider location channel differences.We divide the whole large-sized area of interest into several cells.Then as to SUs moving into the same cell, they are close geographically and thus close path-loss.Meanwhile,their surroundings are similar and thus shadow fading and multi-path effects are alike.So compared with SUs in different cells, SUs in the same cell have much more similar channel conditions and much closer detected results.Then it is reasonable to say in our considered scenario, the channel condition differences in one cell are little while those in different cells are large.Since the location diversity of the CRN is considered in our algorithm, the SNR cannot be too low.Then our algorithm identifies MUs by finding detected results in each cell which are relatively far from most results in the particular cell and then decreasing their reputation scores.Even if an SU move into a cell with extremely good or bad channel conditions, only if that SU is reliable, its detected results would still be consistent with other detected results of SUs in that specific cell.This is the reason why we divide the whole area into cells and also how we overcome the mentioned drawback of CTAs.
To be specific, in this paper we divide the whole area of interest intoLequal-sized square cells as shown in Fig.1 and each cell is assigned with a unique cell number.Assume that all cells have similar noise level.The CRN consists of a static PU, an FC andNmobile SUs includingMMUs andRRUs.Assume thatsamples are used to perform energy detection (ED) in one detection period at each SU.Detected energy values by the SUs are forwarded to the FC along with the cell numbers of the cells they currently belong to.Then the sensing problem can be formulated as a binary hypothesis test to detect the presenceor absenceof PU, which means, the FC decodes and combines the detected results from all SUs to firstly removes MUs, then assigns each SU with an appropriate weighting coefficient, makes a final decision between the two hypotheses, and finally broadcasts it to all SUs.
Here we take Fig.1 as an example, but actually our algorithm can apply when it is divided into cells in any size or with any number according to required accuracy.The whole area can be divided according to field detection results to put areas with similar channel conditions into one common cell; or divided by experience and for example, dense building areas in CNRs should constitute a cell.
2.2 Signal propagation
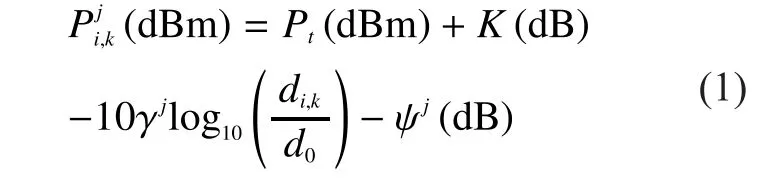
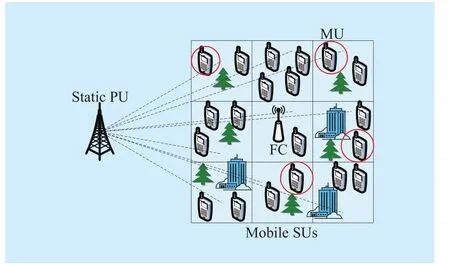
Fig.1 The CRN model with a static PU and several mobile SUs
2.3 Sensing model
We assume SUs sense the spectrum periodically slot by slot through performing ED since its simple design and efficiency.And assume that the PU’s state remains unchanged within one detection interval.Then the received signalat theith SUwhich is in cellduring thekth detection under the two hypotheses is given by
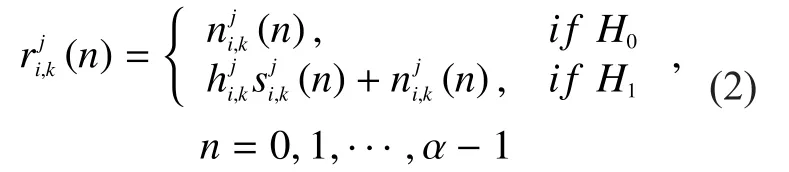
wherenrepresents the sampling index; the channel responseis closely related with the location ofwhile moving but is considered to be constant within each detection interval;denotes the transmitted signal of the PU;is additive white Gaussian noise with zero-mean and varianceThen, the detected signal power,by is

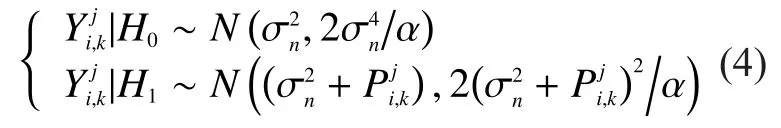
In an ideal world, single-node spectrum sensing is able to meet requirements of CR.However in a real sensing environment, there are lots of problems, such as hidden terminal problem, channel fading effects and multi-path effects [7], causing bad detection performance of single-node sensing.Multi-node cooperative sensing can reduce those limitations of single-node sensing.We choose soft-decision cooperative sensing for it having better detection performance than hard-decision.In soft-decision cooperative sensing system,firstly SUs send their own local energy detection resultsto the FC.Then, the FC decides proper weighting coefficientsaccording to a certain soft-decision data fusion rule, such as equal gain combining (EGC), maximal ratio combining (MRC) and so on.Finally, the FC calculates the following weighted objective function [16]
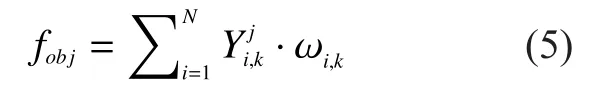
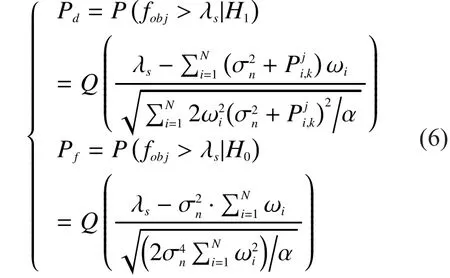
2.4 Malicious attack model
Here we choose the following malicious attack model.All MUs send random cell numbers to the FC no matter which cells they belong to during current sensing slots.And they send detected results after doubling them underor halving them under.
III.ALGORITHM DESCRIPTIONS
3.1 Malicious user identifying process
Our idea of identifying MUs is to calculate each cell’s common reading first, namely the average of detected results in that cell, and then consider results with larger disparities from the average value to be unreliable.Next, we decrease those unreliable results’corresponding SUs’ reputation scores and finally regard SUs with less reputation scores than the preset thresholdas MUs and remove them.Two functions need to be defined: the distance functionto describe the disparity between the detected result of userduring thekth sensing slot and the common reading of(the cellbelonging to during thekth slot); the reputation score increment functionto update’s reputation score.
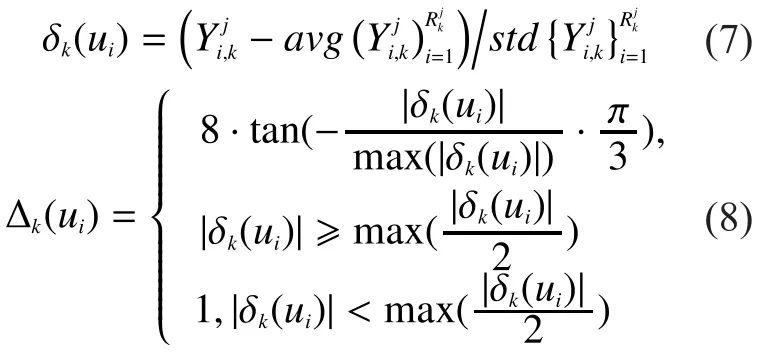
whereavgandstdmean computing the average value and the standard deviation, respectively.There are two requirements for reputation score increment functionin our algorithm: whenis relatively small,its correspondingshould be a positive number to ensure RUs’ reputation scores would increase; whenis large,should be negative to make sure that reputation scores of MUs would decrease until removed.And largermeans that the corresponding detected results are less reliable, so the absolute value of the negativeshould be larger to punish them to a larger extent.In fact, there are more than one functions meeting these requirements.Generally speaking, we choose increment functions by experience in our assumed scenario.And the function shown in (8) is suited to our system.We compute each SU’s reputation score incrementaccording to(7) and (8) and then update its reputation score according toon the condition of the assumption of its maximum valueand minimum valueNext, we shall present the foundation and principle of removing MUs in our algorithm from the perspective of statistics.
According to section 2.3, under the hypothesis ofthe mathematical expectation of the detected results of an RU isAnd the mathematical expectation of an MU isUnder the hypothesis ofthe expectations of an RU and an MU are respectivelyandis the probability density function(PDF) ofIn the same cell,is the same to RUs and MUs, so we only need to compare their numerators, i.e.
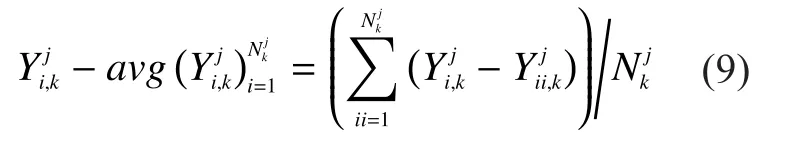
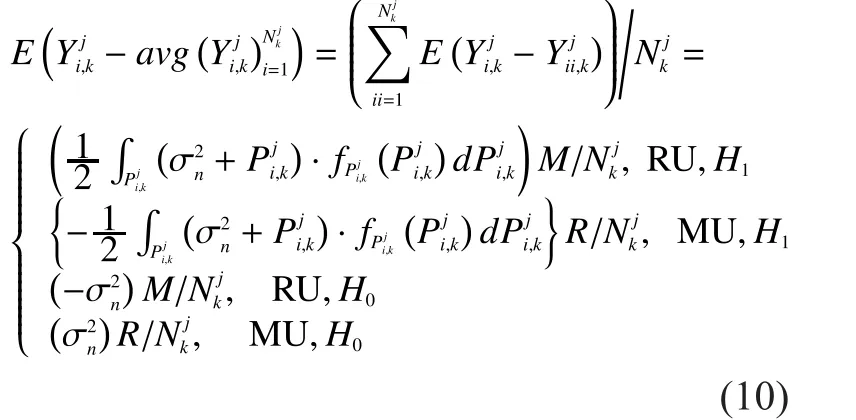
Normally, there are more RUs than MUs in CRNs.Thus according to (10), the absolute differences between the common readings,and detected results of an RU are smaller than those of an MU in the same cell.So distance functions of RUs are smaller and thus their increment functions calculated from(8) are positive, which means their reputation scores will increase; distance functions of MUs are larger and their increment functions are negative, which means their reputation scores will decrease.Whenis less than the preset thresholdwill be removed.
If the total number of SUs is small or the CRN is divided into too many cells, there will be limited detected data in each cell.In our algorithm,is used to describe the common reading of cellso the less involved detected data when calculatingeach time, the more inaccurately the computed common reading will reflect the real channel conditions of that particular cell.To cope with this problem, we propose an idea of “slide window”.We regardllatest detected results of all SUs as a whole as shown in Fig.2.Each grid represents all detected results sent to the FC during the corresponding sensing slot.Consider all detected results of latestlslots as a whole during each data processing.According to all data in the “slide window”, the FC updates SUs’ reputation scores, removes MUs and calculates weighting coefficients during data fusion.Introducinglis to increase the total number of detected data used when computingeach time, to raise the statistical sample number, and to finally enhance our algorithm’s accuracy and reliability.
We next will introduce the concrete steps of our MUs removing process based on the idea of “slide window”.After thekth sensing slot,we get the detected result setY, which consists of data sent to the FC during thekth sensing slot and detected results transmitted during the former (l-1) sensing slots:Consider thoseenergy values fromNSUs afterlslots inYas energy values fromSUs after one slot and then substitute them into (7) and (8) to computedistance functions andreputation score increment functions corresponding to each element inY, respectively.Theincrement functions make up the set:
Then calculateui’s reputation score incrementaccording to (11) and (12).
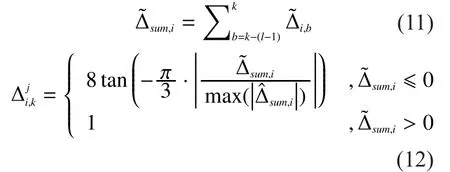
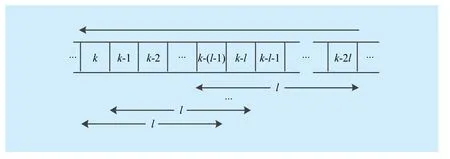
Fig.2 Slide window
3.2 Data fusion rule
Currently, an overwhelming majority of soft decision data fusion rules need some prior information during calculate weighting coefficients.However, prior information,such like SNR, is not easy to obtain in mobile CRNs since it changes all the time as SUs move.Thus, conventional data fusion rules which require the values of SNRs are no longer able to apply in mobile CRNs in our algorithm.Thus we adopt a soft decision data fusion rule aiming at mobile SUs.It is also the second part of our algorithm.It calculates the weighting coefficients with detected results sent to the FC within the “slide window”.We assign cells with better channel conditions with larger weighting coefficientsas shown in (13), since detected results from those cells with better channel conditions, i.e.larger SNRs, tend to be larger in our scenario.Weighting coefficients for detected results of RUs within the “slide window”,are obtained according to weighting coefficients of cells,which are worked out by (13).Then weighting coefficientsneed to be normalized as in (14) to adapt to the fixed preset thresholdwhich means the sum of the squares of them is 1.So weighting coefficients of arbitrary SUs won’t be so large, leading to play an decisive role in final decisions.Equation (15) shows how to calculate the weighted objective functionof our method.The FC considers PU to be active ifis larger than thresholdor otherwise, to be idle.
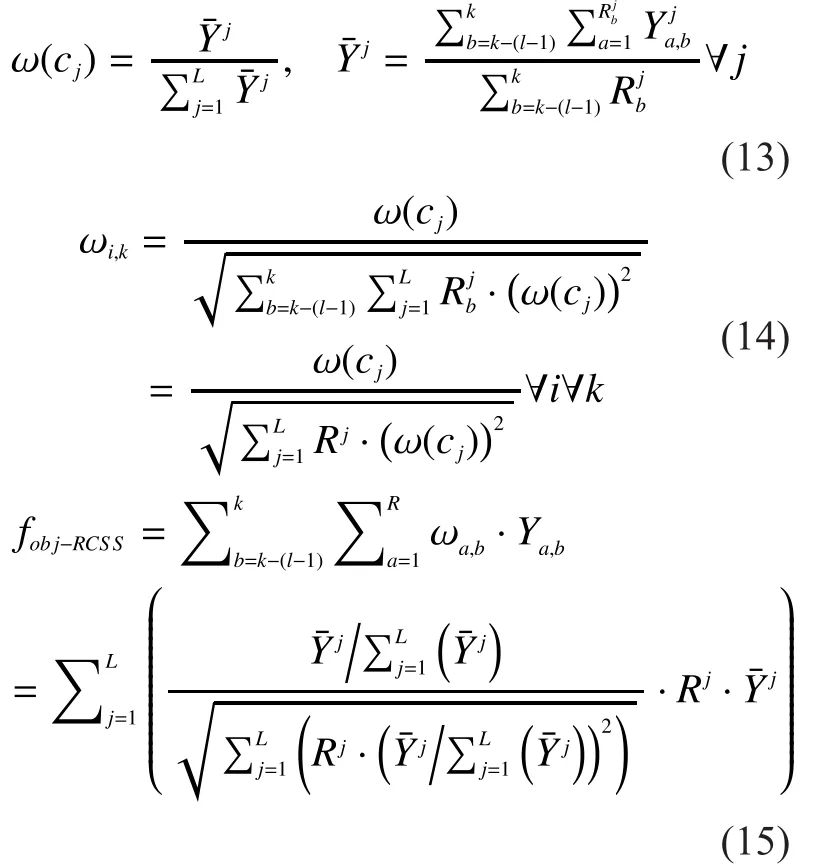
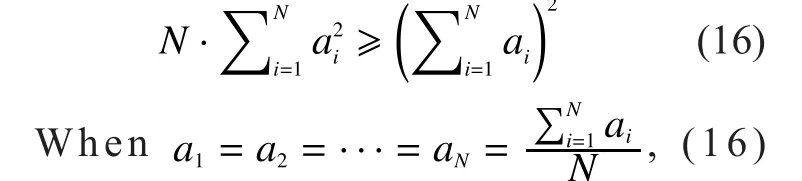
becomes an equation.So

which means
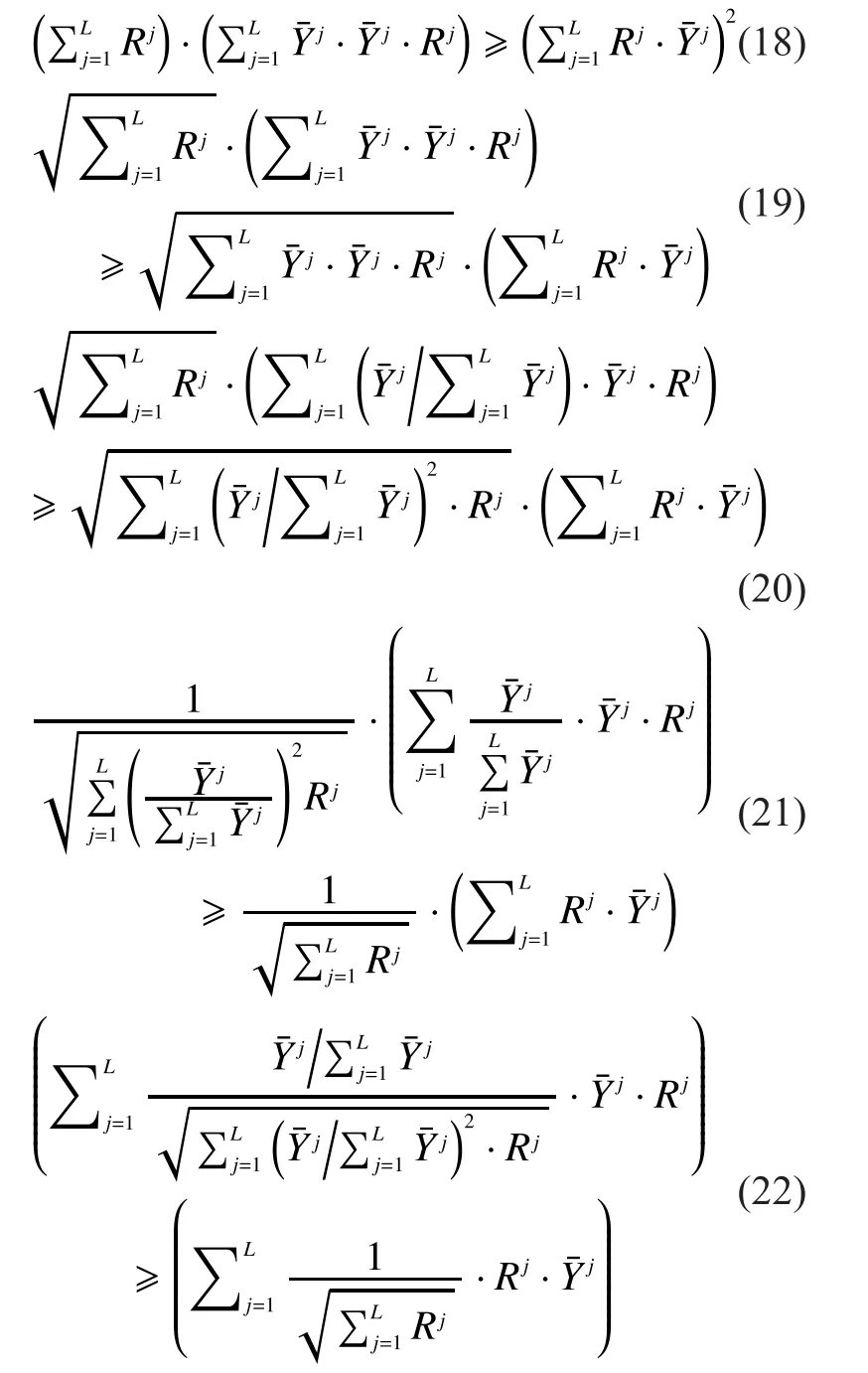
According to (22), the weighted objective function of our data fusion method is no less than that of EGC, i.e.
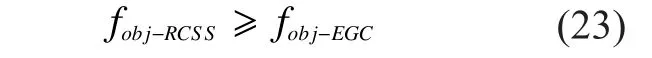
In mobile CRNs, the detection probabilityand the false alarm probabilityof RCSS are:
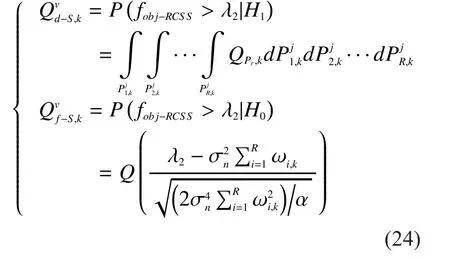
where
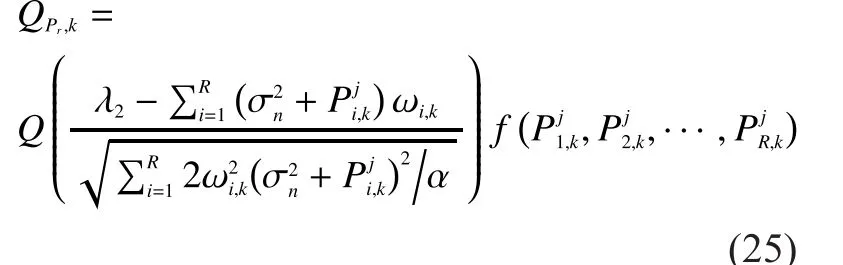
3.3 Algorithm descriptions
In order to make this algorithm easy to understand, the notations in this paper are as follows.
Above all, we conclude RCSS as Table II.
IV.SIMULATION RESULTS
We use MATLAB to simulate the system.In this section, the detection performance of RCSS is compared with CTA and TCSS.Here CTA specifically refers to the algorithm same with RCSS except that it does not divide the entire area into cells to ensure the comparability.It also has the characteristics described in Section I.In this way, the comparison will demonstrate strongly that dividing the entire area into cells is an effective method to overcome the above-mentioned drawback of conventional algorithms.Assume that the whole area is asquare area, whose closest location is 2000m away from the PU.The noise signal power is 300mW and the PU transmitted signal power is 1W.andare respectively from 0 to 2 and 2dB to 6dB.We assumeandby experience.
According to IEEE 802.22 [17], the sensing duration (1ms-10ms) is quite small, and thus we assume the locations of SUs keep unchanged during each sensing.Spectrum evacuation should be within 2 seconds by the SUs when the PU becomes active.Therefore,time between two adjacent sensing slot is small(<=2s), it would be unrealistic if we consider a mobility model with sudden and uncorrelated changes in speed and direction during each sensing slot.In our model, their values are correlated to the previous one to avoid unrealistic patterns.To be specific, we assume that the initial velocityand acceleration of all SUs isThe speed and direction change every 5s.To be specific, the direction changes randomly every time.We assume that the SUs never pause and they sense after every 1s.
Figs.3, 4 and 5 compare the detection performances of RCSS, TCSS and CTA in terms of receiver operating characteristics (ROC),respectively (N=60,M=15 or 18,l=12;N=48,M=12 or 15,l=15;N=52 or 60,M=14,l=14).The values ofls are assumed by experience.From those three figures, we get the following conclusions.(1) For constantN, largerMbrings worse detection performance for all three algorithms according to Figs.3 and 4.As to RCSS, the largerMis, the more fake detected results will be sent to the FC during every sensing slot.Then the computed common reading in each cell,would no longer reflect the real channel conditions,causingandinaccurate.Thus, the FC cannot remove MUs thoroughly and even remove some reliable ones mistakenly.So the largerMis, the poorer the performance will be.(2) According to Figs.3 and 4, as to the three algorithms, keeping the percentage ofconstant, asNincreases, the performance improves, since larger space diversity gains are obtained.As to RCSS, that’s because whenNis small, the statistical computedgenerally can’t reflect real conditions as accurately as largerN, since simple size for statistics is smaller, and thus MUs cannot be distinguished accurately causing the performance poor.(3) According to Fig.5, for constantM, largerNbrings better detection performance for all three algorithms since largerNbrings larger.(4) The detection performance of RCSS is significantly better than that of TCSS and CTA in mobile CRNs with various number of SUs (N), which means on condition that the false alarm probability is constant, our algorithm has larger detection probability.For example, in Fig.3 when SUs are mobile, our algorithm has an improvement of primary user detection probability by 0.97-dB and 3.57-dB when false alarm probability is 0.1 (N=60,M=18), in comparison to CTA and TCSS, respectively.Next, we will analyze the reasons of (4) in details.

Fig.3 Comparison of ROC curves of three algorithms when N=60, M=15 or 18
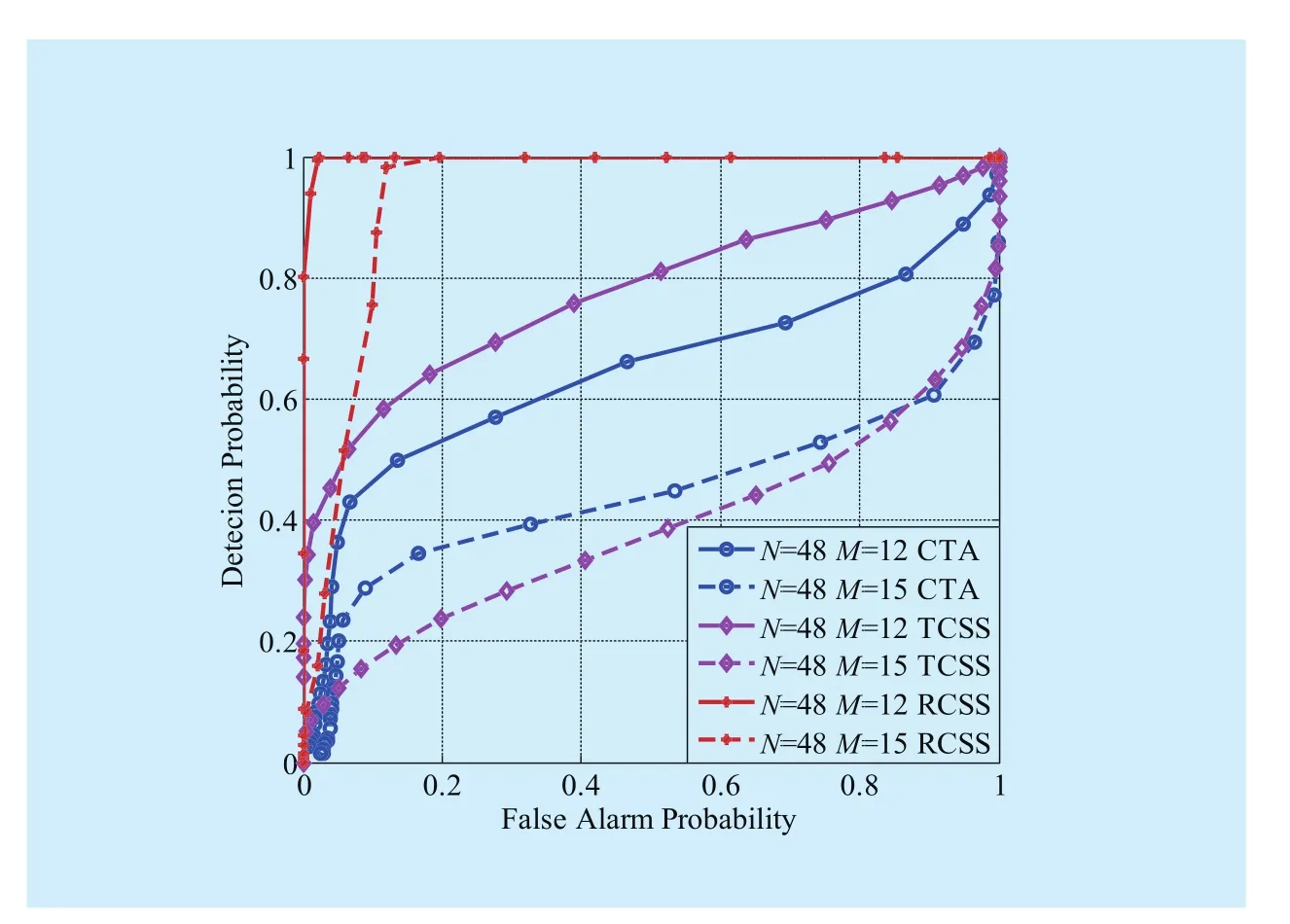
Fig.4 Comparison of ROC curves of three algorithms when N=48, M=12 or 15
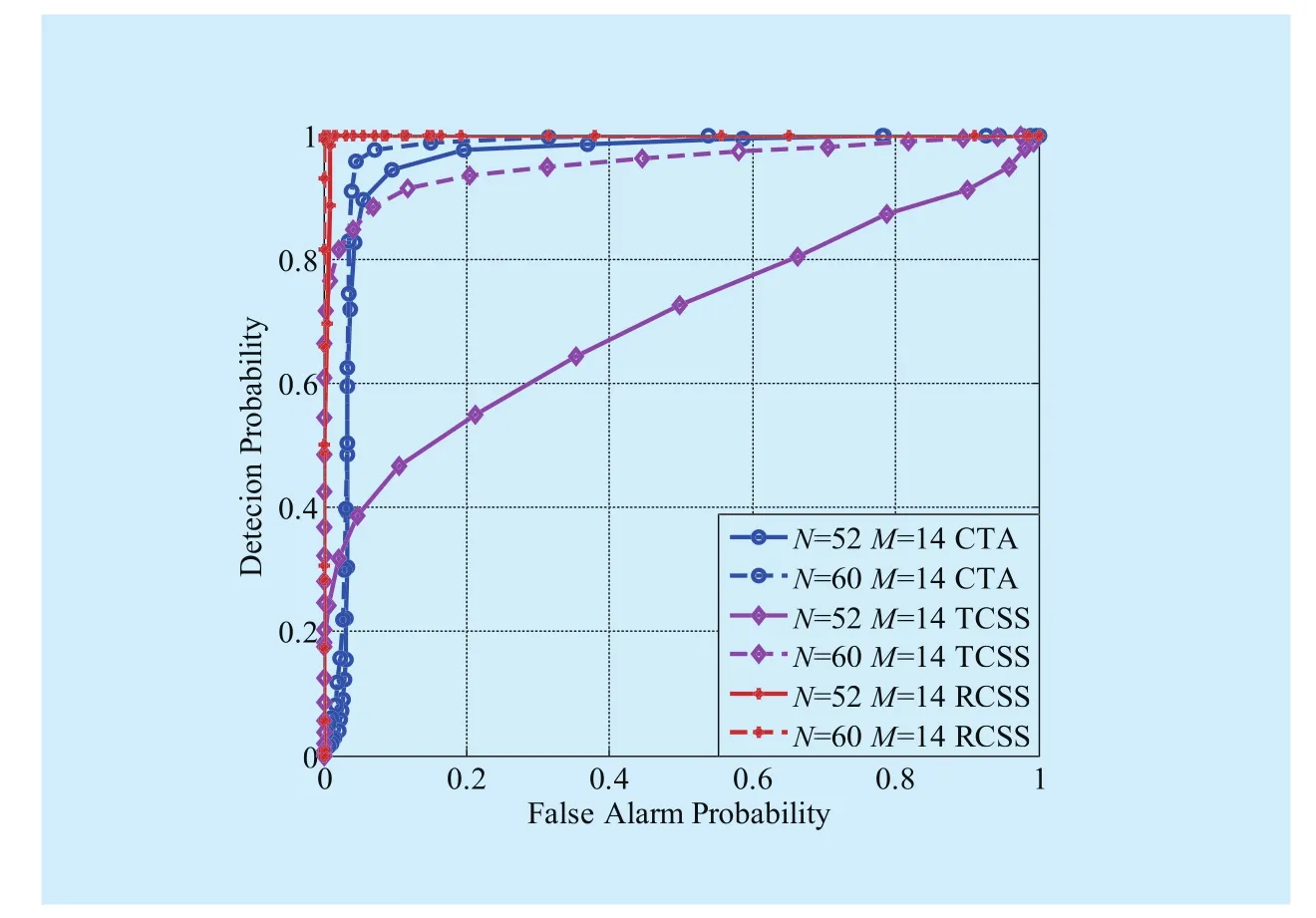
Fig.5 Comparison of ROC curves of three algorithms when N=52 or 60, M=14
Compare with RCSS, CTA does not have the two following processes: the usage of“slide window” and dividing the whole area into cells.The lack of “slide window” makes the number of statistical sample data involved in each calculation become less and thus CTA is not as accurate and reliable as RCSS.The lack of dividing into cells leads to the following drawback.In terms of data fusion, the absence of dividing is equivalent to executing cell dividing (L=1) but assigning cells with equal weighting coefficients.And the derivation in section 3.2 proves that CTA’s lack of dividing the entire area makes its detection probability smaller compared with RCSS on condition that the false alarm probability remains unchanged.Next, we explain why TCSS whose MU removing principle is based on D-S theory cannot identify MUs accurately.TCSS also assigns SUs with trust values.According to [13], the particular chosen D-S iteration formula leads to the fact that all trust values will finally increase until larger than the MU detection threshold no matter what the detected results actually are.Then no matter an SU is malicious or not, it would finally be identified to be reliable after a certain period of time.And that is why we argue that TCSS cannot distinguish MUs accurately.
V.CONCLUSION
In this paper, we have proposed a reputation-based cooperative spectrum sensing algorithm for mobile CRNs to resist malicious attacks.By dividing the entire area of interest into cells, removing MUs based on their updated reputation scores and then providing larger weighting coefficients for detected results from cells with better channel conditions,our algorithm was able to accurately remove MUs in a mobile CRN and obtain great detection performance.The simulated results showed that in mobile scenarios, the detection performance of our algorithm was significantly better than that of CTA and TCSS no matter whether the number of SUs was more or less.
ACKNOWLEDGEMENT
This work was supported by National Natural Science Foundation of China under Grant No.61671183, the Open Research Fund of State Key Laboratory of Space-Ground Integrated Information Technology under Grant No.2015_SGIIT_KFJJ_TX_02, major consulting projects of Chinese Academy of Engineering under Grant No.2016-ZD-05-07.
[1] L.Berlemann, S.Mangold, “Cognitive Radio and Dynamic Spectrum Access”, Hoboken:John Wiley & Sons, Inc., pp.1-5, 2009.
[2] M.Song, C.Xin, Y.Zhao,et al, “Dynamic Spectrum Access: From Cognitive Radio to Network Radio”,IEEE Wireless Communications, vol.19,no.1, pp.23-29, February, 2012.
[3] M.Yang, Y.Li, X.Liu, et al, “Cyclostationary Feature Detection Based Spectrum Sensing Algorithm under Complicated Electromagnetic Environment in Cognitive Radio Networks”, China Communications, vol.12, no.9, pp.35-44,September, 2015.
[4] B.Mughal, S.Hussain, A.Ghafoor, “Cooperative Subcarrier Sensing Using Antenna Diversity Based Weighted Virtual Sub Clustering”, China Communications, vol.13, no.10, pp.44-57, October, 2016.
[5] X.Zhang, F.Gao, R.Chai, et al, “Matched Filter Based Spectrum Sensing When Primary User Has Multiple Power Levels”, China Communications, vol.12, no.2, pp.21-31, February, 2015.
[6] X.Wu, X.Han, F.Labeau, ”High Capacity Spectrum Sensing Framework Based on Relay Cooperation”, China Communications, vol.13, no.8,pp.117-126, August, 2016.
[7] F.F.Digham, M.-S.Alouini, M.K.Simon, “On the Energy Detection of Unknown Signals over Fading Channels”,IEEE Transactions on Communications, vol.55, no.1, pp.21-24, January, 2007.
[8] S.Bhattacharjee, S.Debroy, M.Chatterjee, “Trust Computation Through Anomaly Monitoring in Distributed Cognitive Radio Networks”,Proceedings of 2011 International Symposium on Personal Indoor and Mobile Radio Communications (PIMRC), pp.593-597, September 11-14,2011, Toronto, ON.
[9] A.G.Fragkiadakis, E.Z.Tragos, I.G.Askoxylakis,“A Survey on Security Threats and Detection Techniques in Cognitive Radio Networks”,IEEE Communications Surveys & Tutorials, vol.15,no.1, pp.428-445, January, 2012.
[10] M.Jia, X.Wang, Q.Guo,et al, “A Novel Multi-Bit Decision Adaptive Cooperative Spectrum Sensing Algorithm Based on Trust Valuations in Cognitive OFDM System”,Proceedings of 2014 Vehicular Technology Conference (VTC Fall), pp.1-5, September 14-17, 2014, Vancouver, Canada.
[11] K.Arshad, K.Moessner, “Mobility Driven Energy Detection Based Spectrum Sensing Framework of a Cognitive Radio”,Proceedings of 2010 Second UK-India-IDRC International Workshop on Cognitive Wireless Systems (UKIWCWS), pp.1-5,December 13-14, 2010, New Delhi, India.
[12] M.F.Amjad, B.Aslam, C.C.Zou, ”Reputation Aware Collaborative Spectrum Sensing for Mobile Cognitive Radio Networks”,Proceedings of the 2013 IEEE Military Communications Conference (MILCOM), pp.951-956, November 18-20,2013, San Diego, CA.
[13] S.Jana, K.Zeng, W.Cheng,et al, “Trusted Collaborative Spectrum Sensing for Mobile Cognitive Radio Networks”,IEEE Transactions On Information Forensics and Security, vol.8, no.9,pp.1497-1507, July, 2013.
[14] A.F.Molisch, “Wireless Communications (Second Edition)”, Hoboken:John Wiley & Sons, Inc.,2011.
[15] M.L.Benitez, F.Casadevall, “Improved Energy Detection Spectrum Sensing for Cognitive Radio”,IET Communications, vol.6, no.8, pp.785-796, July, 2012.
[16] H.Mu, J.K.Tugnait, “Joint Soft-Decision Cooperative Spectrum Sensing and Power Control in Multiband Cognitive Radios”,IEEE Transactions On Signal Processing, vol.60, no.10, pp.5334-5346, June, 2012.
[17] WRAN WG on Broadband Wireless Access Standards, IEEE 802.22.Available: www.ieee802.22.org/22.
- China Communications的其它文章
- A Non-Cooperative Differential Game-Based Security Model in Fog Computing
- Dynamic Weapon Target Assignment Based on Intuitionistic Fuzzy Entropy of Discrete Particle Swarm
- Directional Routing Algorithm for Deep Space Optical Network
- Offline Urdu Nastaleeq Optical Character Recognition Based on Stacked Denoising Autoencoder
- Identifying the Unknown Tags in a Large RFID System
- Toward a Scalable SDN Control Mechanism via Switch Migration

