An Evolution, Present, and Future Changes of Cloud Computing Services
Wen-Lung Shiau
1. Introduction
Cloud computing represents high computing capacity on the Internet with low cost computers and storage devices,the widespread adoption of virtualization, service-oriented architecture, and utility computing[1],[2]. Cloud computing is a service rather than a product, and shares resources,software, information, and computing power among users on the Internet. Users do not need to know any details of the computing infrastructure. Cloud computing services have swept aside technology services around the world.According to a Gartner Executive Programs worldwide survey[1], more than 2000 CIOs (Chief Information Officers)identified cloud computing as the top technology priority in 2011. To fulfill the need for cloud computing services,software service providers offer many solutions to customers. For example, Amazon Web Services (AWS)delivers a set of services that form a reliable, scalable, and inexpensive computing platform “in the cloud”. These services include Amazon Elastic Compute Cloud (EC2) and Amazon Simple Storage Service (S3). Other well-known cloud computing services and applications include IBM's Rational Software Delivery Services, IBM SmartCloud Application Services, IBM SmartCloud Managed Backup,Microsoft Windows Azure Services Platform,VMforce.com (Salesforce.com's PaaS), CRM(Salesforce.com), Oracle CRM On Demand, Cloud ERP(Epicor Express Edition), and Jive Social Business Software (SBS)[3]. Although there are many well-known applications of cloud computing services, there is still confusion about how it has evolved and what it is[4]. Further,few studies offer a clear roadmap and key applications to cloud computing services[5]. Thus, the purpose of this study is to describe the evolution of cloud computing services and provide a roadmap to its development and key applications.Further, with today’s rapid changes in the information technology environment, this study also discusses new challenges in cloud computing services and provides insightful perspectives for future cloud computing services.
2. Past: Evolutionary Cloud Computing Service
The concept of cloud computing came from an American computer scientist and cognitive scientist, John McCarthy, who suggested that “computation may someday be organized as a public utility”[6]. This idea of public computer utility was very popular during the late 1960s and lasted for many years. Cloud computing has evolved through a number of phases, including distributed computing, grid computing, and utility computing.Distributed computing generally operates on distributed systems, which are groups of networked computers working together. In distributed computing, each processor has its own private memory and computing power.Processors exchange information by passing messages.These processors are coordinated to share resources and provide computing services to users. In the 1990s, grid computing evolved from distributed computing and coordinated networks of computers, allowing computationally intensive tasks. Grids evolved from distributed computing with many networked loosely coupled computers acting together to perform computationally intensive scientific, mathematical, and academic problems through volunteer computing. Grid computing was also used in many applications, such as economic forecasting, weather analysis, e-commerce, and Web services for individuals and organizations. Utility computing is a form of open grid utility computing. This type of software application uses a grid infrastructure.Users plug into a grid-enabled application and use metered utility services. Thus, cloud computing evolved from distributed computing, grid computing, and utility computing.
The applications of cloud computing services are various and classified into three categories: infrastructure as a service (IaaS), platform as a service (PaaS), and software as a service (SaaS)[4],[7]. In the beginning, Ramnath Chellappa introduced the first academic use of the term“Cloud Computing” as a concept of computing paradigm in 1997. In this concept, computing boundaries are determined by economic rationale rather than technical limits alone. In 1999, Salesforce.com delivered customer relationship management (CRM) as a pioneering concept of cloud computing in enterprise applications over the Internet. In the same year, VMware used cloud computing to develop virtualization technology for the x86 system. Virtualization transformed x86 systems into a general purpose and shared hardware infrastructure that enabled a low-cost, fully isolated, and flexible operating system for application environments. Amazon.com began offering a suite of cloud-based services, called Amazon Web Services (AWS),including storage and computation in 2002. Amazon developed the next version of cloud-based services, called Elastic Compute cloud (EC2), as a commercial web service in 2006. They used EC2 to run their own computer applications and used S3 for pay-per-use, which became a standard for cloud computing pricing model. Also in 2006,Google launched browser-based enterprise applications and an office suite as SaaS. In 2007, Salesforce launched Force.com as their platform as a service (PaaS). In 2008,Google offered their App Engine as a PaaS, providing low cost computing and storage services. Microsoft launched a commercial PaaS version of Azure in 2010. This PaaS provided a virtual Windows environment for executing programs and storing data. Fig. 1 summarizes the evolution and key applications of cloud computing services.
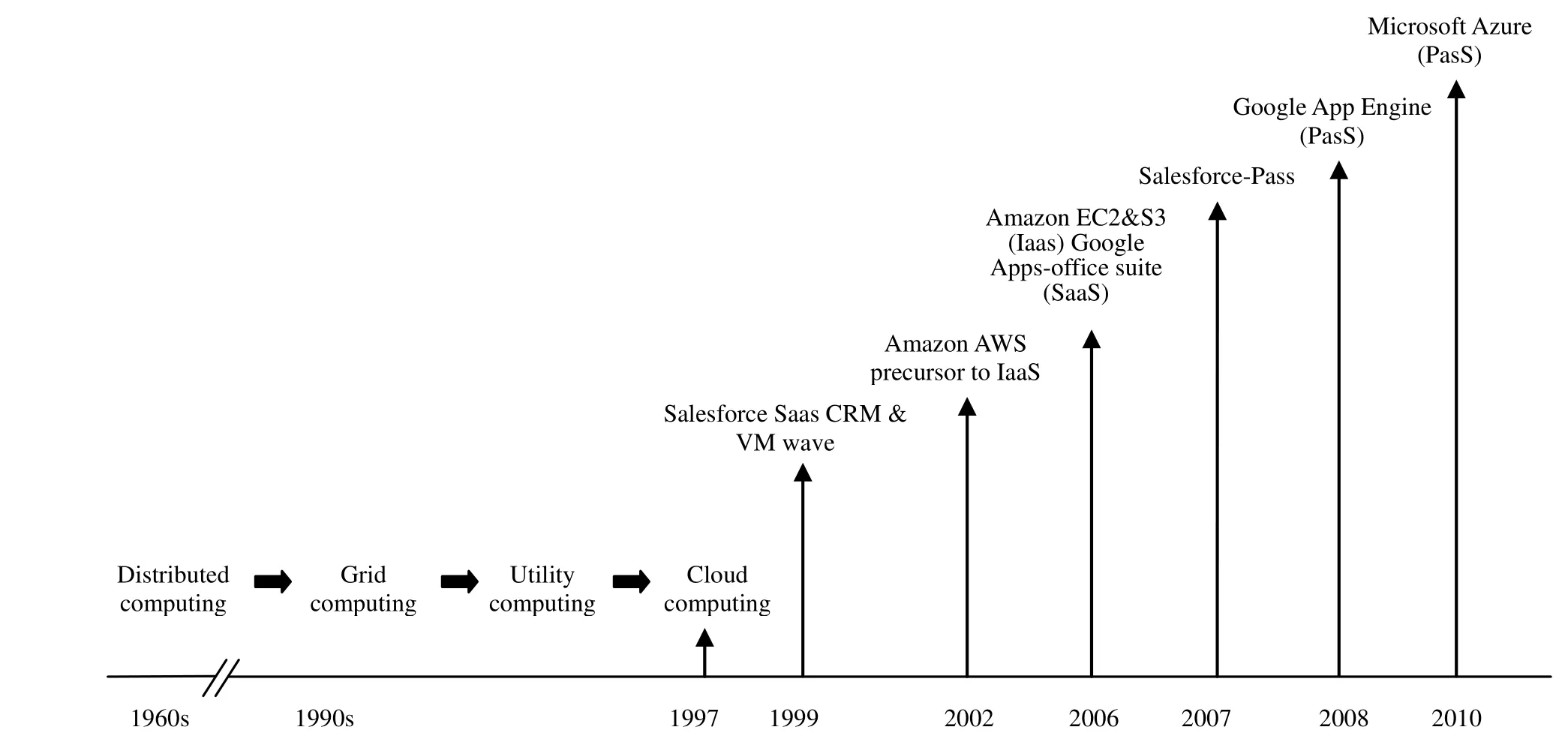
Fig. 1. Evolution and key applications of cloud computing services.
3. Present: Current Development of Cloud Computing Service
Cloud computing provides huge computation power and storage capacity which enable users to deploy and use applications. Further, the cloud computing technology has become more and more utilized in methodology (model) or applications. For examples, Coria et al.[8]proposed a novel model (or methodology) for automatic construction of business processes to facilitate the semi-automatic reuse of web services on a cloud computing environment. The model is based on the web service technology, including: (a)automatic discovery of web services; (b) semantics description of web services; (c) automatic composition of existing web services to generate new ones; (d) automatic invocation of web services. After implementing on a real case study, their results show a good reliability of intelligent business processes composition based on multi-agent systems, semantics, and cloud integration.Alsoghayer and Djemame[9]proposed a mathematical model to predict the risk of failure of resources in distributed environments, such as grids and clouds, using a discrete-time analytical model. Their results show the model can accurately predict the resources risk of failure and allow a service provider to selectively choose which service level agreements (SLA) request to accept. Gao et al.[10]proposed a multi-objective ant colony system algorithm for the virtual machine placement problem in cloud computing. Their goal is to efficiently obtain a set of non-dominated solutions that simultaneously minimize total resource wastage and power consumption. Their proposed algorithm is tested and compared to that of an existing multi-objective genetic algorithm and two single-objective algorithms. Their results show that the proposed algorithm is more efficient and effective than the methods compared.Tung and Tseng[11]proposed a novel approach to collaborative testing in a crowd sourcing environment.They used a greedy approach with four heuristic strategies to solve computational complexity and large-scale problems. Their results show that the proposed heuristic algorithms produce good quality approximate solutions in an acceptable timeframe. Li et al.[12]studied a semantic-based transaction model for web service, defined the component as corresponding state transitions that should be decomposed further into sub-transactions and semantic transactions, and implemented a project to assess overall efficiency. Their results show that the proposed semantic model can indeed improve the throughput and,consequently, decrease the delay time for concurrent transactions.
Yu et al.[13]presented a comprehensive framework for managing continuously changing data objects (CCDOs),such as data streams from sensors and tracking devices,with insights into the spatiotemporal uncertainty problem.They also presented an original parallel-processing solution for efficiently managing the uncertainty using the map-reduce platform of cloud computing. Further, a cloud software engineering involves problems of optimization:performance, efficiency, allocation, assignment, and the dynamic balancing of resources. For example, Harman et al.[14]developed the theme of search based software engineering (SBSE) for the cloud to achieve pragmatic trade-offs between many competing technical and business objectives. Moreover, Zhang et al.[15]proposed an efficient quasi-identifier index based approach for privacy preservation over incremental data sets on cloud. Their results show the efficiency of privacy preservation on large-volume incremental data sets can be improved significantly over existing approaches.
Cloud computing applications are related to survey on reliability, a tool, users’ switching toward cloud computing,learning, experience, knowledge, risk, and adoption. For examples, Ahmed and Wu[16]did a survey on reliability in distributed systems. They described some pragmatic requirements for highly reliable systems and highlighted significance and various issues of reliability indifferent computing environment such as cloud computing, grid computing, and service oriented architecture. They explained factors and various challenges that are nontrivial for highly reliable distributed systems, including fault detection, recovery and removal through testing or various replication techniques. They also examined various research models which synthesize significant solutions to tackle factors and challenges in predicting as well as measuring reliability of software applications in distributed systems. Caballer et al.[17]introduced the elastic cloud computing cluster (EC3), a tool that creates elastic virtual clusters on top of Infrastructure as a service (IaaS) clouds.They presented two different case studies to assess the effectiveness of an elastic virtual cluster. Their results show that the usage of self-managed elastic clusters has an important economic saving when compared both with physical clusters and static virtual clusters deployed on an IaaS Cloud. Park and Ryoo[18]used a longitudinal design to get survey data from undergraduate students to investigated end-users’ switching toward cloud computing, Google Apps settings. Their results show that users’ switching intention to cloud services is not only positively influenced by expected switching benefits whose antecedents are omnipresence of cloud services and collaboration support,but also negatively influenced by expected switching costs whose antecedents are satisfaction with incumbent IT and breath use of inclement IT. End-users’ personal innovativeness moderates the impacts of switching benefits and costs on switching intention. Mousannif et al.[19]studied collaborative learning in the clouds, explored the actual internal working of cloud computing, and demonstrated its viability for organizations, more specifically educational establishments. Their results show the impact and potential benefits of cloud computing on teaching and learning in educational institutions. They also described building a private cloud inside educational institution and highlighting its offerings for students, staff,and lecturers. Sultan[20]investigated the knowledge management in the age of cloud computing and Web 2.0.From experiencing the power of disruptive innovations, the results of this study show that the knowledge management is entering an era where ordinary people and employees are expected to make significant contribution to knowledge creation and management. To take advantages of organizational knowledge management, organizations will need to encourage as many of their staffs as possible to engage and contribute to content creation. They also will need to employ different management methods to achieve this objective. Brender and Markov[21]investigated risk perception and risk management in cloud computing. They elaborate on the most important risks inherent to the cloud such as information security, regulatory compliance, data location, investigative support, provider lock-in, and disaster recovery. Their results show a sufficient degree of risk awareness with a focus on those risks that are relevant to the IT function to be migrated to the cloud. The adoption of cloud services depends on the company’s size with larger and more technologically advanced companies which are better prepared for the cloud. Lian et al.[22]investigated the critical factors that would affect the decision to adopt cloud computing technology in hospital industry. Their results show that the five most critical factors are data security,perceived technical competence, cost, top manager support,and complexity. They also identify the most important dimension is the technology followed by human,organizational, and environmental factors. Moreover, Gupta et al.[23]investigated the usage and adoption of cloud computing by small and medium businesses. Their results show that five factors influence the cloud usage by this business community. Ease of use and convenience are the favorable factors followed by security and privacy and then the cost reduction comes. SMEs (small and medium-sized enterprises) do not consider cloud as a reliable service, do not want to use cloud for sharing and collaboration, and favor their old conventional methods for sharing and collaborating with their stakeholders.
4. Future: New Challenge of Cloud Computing Service
Previous research has discussed the challenges involved in cloud computing services, including trust, security[24],[25],privacy[24], data integrity[24], adoption[4],[26], growth[4],policy and business obstacles[4], online commerce[25],personalized knowledge service[27], and dynamic resource management[28]. New challenges in cloud computing services have emerged because of rapid changes in information technology, such as the next generation of the Internet, data synchronization, cloud security, and competitive advantage of an organization.
4.1 Next Generation of the Internet
The Internet is currently running on the Internet Protocol version 4 (IPv4) address standard designed in 1960s. Unfortunately, the Internet has run out of IPv4 addresses. In 2011, the Internet Corporation for Assigned Names and Numbers (ICANN) joined the Number Resources Organization (NRO), the Internet Architecture Board (IAB), and the Internet Society in announcing that the pool of first-generation Internet addresses has been completely exhausted[29]. Therefore, it is time to accelerate the transition to the next generation of the Internet, IPv6.While the transition from IPv4 to IPv6 is taking place, the transition to the next generation of the Internet (IPv6) and discussion on cloud computing services have become scarce. Fig. 2 shows that clouds move toward the next generation of the Internet. Every cloud service provider must offer IPv6 services. Every cloud client, including PCs,notebooks, tablets, and smart phones, must have a unique IPv6 address and access to cloud service provider through a web browser or a program interface running on the client.To date, no cloud service providers have announced next-generation Internet services.
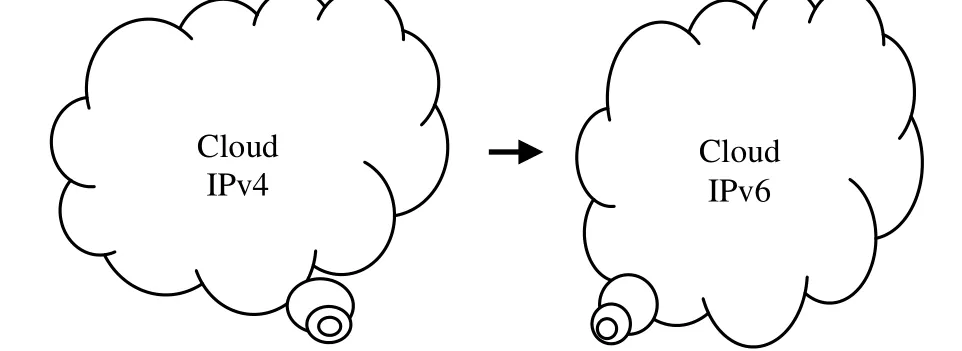
Fig. 2. Clouds move toward the next generation of the Internet.
4.2 Data Synchronization
In an ideal situation, users can store all data in the cloud and access that data at any time, from anywhere. In reality,users store data on PCs, notebooks, FTP servers, and other forms of storage. While the transition from the Web era to cloud era is taking place, users may still store data on many storage devices or many clouds. Thus, the need for data synchronization is increasing. However, crossing boundaries of many clouds are a problem because every cloud has security measures. Thus, data synchronization in many clouds remains a challenging issue.
4.3 Cloud Security
In computer security, a de-militarized (DMZ) provides an organization’s external services, such as e-mail,web,anddomain name system(DNS) servers, to protect the rest of the network from the Internet. For cloud computing services, there are three kinds of deployment models:private cloud, public cloud, and hybrid cloud[4],[9]. These models are similar to the Intranet, Extranet, and Internet.Fig. 3 shows a DMZ cloud in cloud security. Hosts in the DMZ provide services to both the internal (Intranet) and external (Extranet) network, while a firewall controls the traffic between DMZ servers and internal network clients.To accommodate the concept of cloud security, managers should take a DMZ cloud into consideration to provide an additional layer of security to an organization’s cloud.
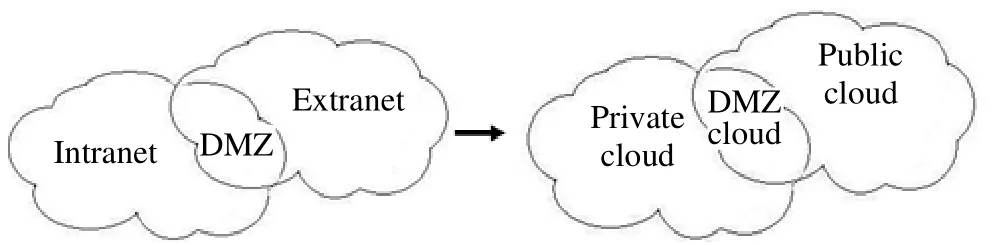
Fig. 3. DMZ cloud in cloud security.
4.4 Competitive Advantage
The main concept of cloud computing services is to organize computing as a public utility. Like electricity industry, users pay for use of public, private, government,and community services, such as per user per month for SaaS, or per unit of storage per month for IaaS. While cloud computing services are ubiquitously available, there will be no difference at all for individuals and organizations.Enterprises that use information technology (IT) as strategic weapon to enhance their competitive advantage will no longer have that advantage. How to increase value added in this scenario is an important factor for enterprises using cloud computing.
5. Conclusions
There are many profiles in the history of cloud computing services. Many people are confused about the evolution and critical applications of cloud computing services. The purpose of this study is to provide a clear evolution of cloud computing services and discuss their key applications. Results provide a clear road map to cloud computing services, highlighting the distributed, grid, and utility methods of computing and key applications of Salesforce, Amazon, Google, and Microsoft. Previous researches have discussed many challenging issues in cloud computing, including security, data privacy, adoption,growth, policy, and business obstacles in private, public,and hybrid clouds. Based on rapid changes in the current information technology environment, this study also describes new challenges to cloud computing services.Results show four new challenges including the next generation of the Internet, cloud security, data synchronization, and the competitive advantage changes produced by cloud computing services.
Many of today’s applications are moving towards a cloud model as cloud computing services have become more pervasively available through the Internet. It is clear that cloud computing will ultimately transform today’s computing landscape and generate enormous benefits for IT users and enterprises. Managers must learn to manage their computing environments, including securing, managing,and monitoring the resources available in the cloud. Only then can cloud computing services enable an enterprise to expand its infrastructure, add capacity on demand, achieve greater flexibility, and realize significant cost savings.
[1] Gartner (2011). Gartner Executive Programs Worldwide Survey of More than 2,000 CIOs Identifies Cloud Computing as Top Technology Priority for CIOs in 2011.[Online]. Available: http://www.gartner.com/it/page.jsp?id=1526414
[2] P. Liang, W. Jiang, B. Gong, M. Davies, and L. Tian, “A new nehavior measurement for cloud computing,” Int. Journal of Advancements in Computing Technology, vol. 4, no. 14, pp.9–16, 2012.
[3] OpenCrowd, Cloudtaxonomy (2010). [Online]. Available:http://cloudtaxonomy.opencrowd.com/taxonomy/
[4] M. Armbrust,A. Fox,R. Griffith,A. D. Joseph,R. Katz,A.Konwinski,G. Lee,D. Patterson,A. Rabkin,I. Stoica, andM.Zaharia, “A view of cloud computing,” Commun. of the ACM, vol. 53, no. 4, pp. 50–58, 2010.
[5]S. Marston,Z. Li,S. Bandyopadhyay,J. Zhang, andA.Ghalsasi, “Cloud computing—The business perspective,”Decision Support Systems, vol.51, no. 1, pp. 176–189, 2011.
[6] Wikipedia, Cloud computing (2012). [Online]. Available:http://en.wikipedia.org/wiki/ Cloud_computing
[7] F. Doelitzscher,A. Sulistio,C. Reich, H. Kuijs, and D. Wolf,“Private cloud for collaboration and e-Learning services:from IaaS to SaaS,” Computing, vol.91, no. 1, pp. 23–42,2011.
[8] J. A. G. Coria, J. A. Castellanos-Garzón, and J. M. Corchado,“Intelligent business processes composition based on multi-agent systems,” Expert Systems with Applications, vol.41, no. 4, pp. 1189–1205, 2014.
[9] R. Alsoghayer and K. Djemame, “Resource failures risk assessment modelling in distributed environments,” Journal of Systems and Software, vol. 88, no. 2, pp. 42–53, 2014.
[10] Y. Gao, H. Guan, Z. Qi, Y. Hou, and L. Liu, “A multi-objective ant colony system algorithm for virtual machine placement in cloud computing,” Journal of Computer and System Sciences, vol. 79, no. 8, pp.1230–1242, 2013.
[11] Y. H. Tung and S. S. Tseng, “A novel approach to collaborative testing in a crowd sourcing environment,”Journal of Systems and Software, vol. 86, no. 8, pp.2143–2153, 2013.
[12] S. H. Li, S. M. Huang, D. Yen, and J. C. Sun,“Semantic-based transaction model for web service,”Information Systems Frontiers, vol. 15, no. 2, pp. 249–268,2013.
[13] B. Yu, R. Sen, and D. H. Jeong, “An integrated framework for managing sensor data uncertainty using cloud computing,” Information Systems, vol. 38, no. 8, pp.1252–1268, 2013.
[14] M. Harman, K. Lakhotia, J. Singer, D. R. White, and S. Yoo,“Cloud engineering is search based software engineering too,” Journal of Systems and Software, vol. 86, no. 9, pp.2225–2241, 2013.
[15] X. Zhang, C. Liu, S. Nepal, and J. Chen, “An efficient quasi-identifier index based approach for privacy preservation over incremental data sets on cloud,” Journal of Computer and System Sciences, vol. 79, no. 5, pp. 542–555,2013.
[16] W. Ahmed and Y. W. Wu, “A survey on reliability in distributed systems,” Journal of Computer and System Sciences, vol. 79, no. 8, pp. 1243–1255, 2013.
[17] M. Caballer, C. de Alfonso, F. Alvarruiz, and G. Moltó,“EC3: Elastic cloud computing cluster,” Journal of Computer and System Sciences, vol. 79, no. 8, pp.1341–1351, 2013.
[18] S. C. Park and S. Y. Ryoo, “An empirical investigation of end-users’ switching toward cloud computing: A two factor theory perspective,” Computers in Human Behavior, vol. 29,no. 1, pp. 160–170, 2013.
[19] H. Mousannif, I. Khalil, and G. Kotsis, “Collaborative learning in the clouds,” Information Systems Frontiers, vol.15, no. 2, pp. 159–165, 2013.
[20] N. Sultan, “Knowledge management in the age of cloud computing and Web 2.0: Experiencing the power of disruptive innovations,” Int. Journal of Information Management, vol. 33, no. 1, pp. 160–165, 2013.
[21] N. Brender and I. Markov, “Risk perception and risk management in cloud computing: Results from a case study of Swiss companies,” Int. Journal of Information Management, vol. 33, no. 5, pp. 726–733, 2013.
[22] J. W. Lian, D. C. Yen, and Y. T. Wang, “An exploratory study to understand the critical factors affecting the decision to adopt cloud computing in Taiwan hospital,” Int. Journal of Information Management, vol. 34, no. 1, pp. 28–36, 2014.[23] P. Gupta, A. Seetharaman, and J. R. Raj, “The usage and adoption of cloud computing by small and medium businesses,” Int. Journal of Information Management, vol.33, no. 5, pp. 861–874, 2013.
[24]K. Hwangand D. Li, “Trusted cloud computing with secure resources and data coloring,” Internet Computing, IEEE, vol.14, no.5, pp. 14–22, 2010.
[25] G. Lackermair, “Hybrid cloud architectures for the online commerce,” Procedia Computer Science, vol.3, pp.550–555, Feb. 2011.
[26]S. C. MisraandA. Mondal, “Identification of a company’s suitability for the adoption of cloud computing and modelling its corresponding return on investment,”Mathematical and Computer Modelling, vol.53, no. 3–4, pp.504–521, 2011.
[27] Y. Wu, Y. Ma, and F. Liu, “Personalized knowledge service platform for postgraduate: Based on Wiki system in cloud computing environment,”Advanced Science Letters, vol. 5,no. 1, pp. 350–356, 2012.
[28] M. Xiao and X. Song, “A survey of cloud computing dynamic resource management,” Int. Journal of Advancements in Computing Technology, vol. 4, no. 14, pp.498–506, 2012.
[29] B. White (2011). Available Pool of Unallocated IPv4 Internet Addresses Now Completely Emptied. [Online]Available: http://www.prweb.com/releases/ICANN/IPv6/prweb8107778.htm
 Journal of Electronic Science and Technology2015年1期
Journal of Electronic Science and Technology2015年1期
- Journal of Electronic Science and Technology的其它文章
- Non-Supervised Learning for Spread Spectrum Signal Pseudo-Noise Sequence Acquisition
- Face Detection under Complex Background and Illumination
- Transformation of Voltage Mode Filter Circuit Based on Op-Amp to Circuit Based on CCII
- Backlit Keyboard Inspection Using Machine Vision
- Efficient Slew-Rate Enhanced Operational Transconductance Amplifier
- Polarization-Dependent Optimization of Fiber-Coupled Terahertz Time-Domain Spectroscopy System
