Multi-Blockchain Based Data Trading Markets With Novel Pricing Mechanisms
Juanjuan Li ,,, Junqing Li, Xiao Wang , Senior,, Rui Qin ,,,Yong Yuan , Senior,, and Fei-Yue Wang ,,
Abstract—In the era of big data, there is an urgent need to establish data trading markets for effectively releasing the tremendous value of the drastically explosive data.Data security and data pricing, however, are still widely regarded as major challenges in this respect, which motivate this research on the novel multi-blockchain based framework for data trading markets and their associated pricing mechanisms.In this context, data recording and trading are conducted separately within two separate blockchains: the data blockchain (DChain) and the value blockchain (VChain).This enables the establishment of two-layer data trading markets to manage initial data trading in the primary market and subsequent data resales in the secondary market.Moreover, pricing mechanisms are then proposed to protect these markets against strategic trading behaviors and balance the payoffs of both suppliers and users.Specifically, in regular data trading on VChain-S2D, two auction models are employed according to the demand scale, for dealing with users’ strategic bidding.The incentive-compatible Vickrey-Clarke-Groves (VCG)model is deployed to the low-demand trading scenario, while the nearly incentive-compatible monopolistic price (MP) model is utilized for the high-demand trading scenario.With temporary data trading on VChain-D2S, a reverse auction mechanism namely two-stage obscure selection (TSOS) is designed to regulate both suppliers’ quoting and users’ valuation strategies.Furthermore,experiments are carried out to demonstrate the strength of this research in enhancing data security and trading efficiency.
I.INTRODUCTION
NOWADAYS, data has become a crucial resource in developing intelligent technologies and applications [1],[2].However, the integration of distributed data is challenging, leading to the emergence of “isolated data islands”.Additionally, the concentration of data in the hands of a few owners creates a significant hurdle for the smooth flow of data,known as the “data barrier”.These issues impede the full utilization and realization of enormous value inherent in data.Data trading has emerged as a viable solution to address these problems.
The primary challenge of data trading lies in ensuring data security, often regarded as the bottleneck in establishing effective data trading markets.As an emerging technology,blockchain can address this challenge by building a new trust system through a decentralized autonomous network.It enables non-tampering and traceability of data through a collectively maintained time-sequential chain structure [3], [4].Moreover, blockchain ensures information security by implementing authentication mechanisms, consensus algorithms,and encryption technologies [5], [6].By virtue of these technical features, blockchain is widely recognized as highly applicable to data trading and holds great potential in resolving its security issues [7]-[9].In recent years, significant research efforts have been dedicated to utilizing blockchain technology for constructing decentralized data trading markets [10],[11], with the primary goal to address security concerns such as privacy preservation, information leakage, and data tampering [12].Additionally, corresponding trading protocols, smart contracts, and signature algorithms have also been extensively studied in this context [13], [14].Although these works have contributed to improve the security of data trading, the commonly used single-blockchain structure has distinct deficiencies in segregating the security risks associated with data recording and trading, and also fails to guarantee the trading efficiency when confronted with high levels of concurrency across various trading modes and scenarios.Besides, they mainly focus on specific task-specific scenarios, rather than the broader context of general data trading scenarios.
Therefore, we are motivated to propose multi-blockchain based data trading markets that cater to a wider range of general scenarios.Different smart contracts are deployed in multiple blockchains, so as to form the function-oriented multiblockchain framework.Under this framework, there is no distinction between the main blockchain and side blockchain.Multiple blockchains operate in parallel, utilizing the same infrastructure.Each blockchain in the multi-blockchain based data trading markets operates independently with its own node network and consensus algorithms, thereby ensuring self-contained security.This framework separates data recording and trading across different blockchains, while conducting trading activities in distinct blockchains tailored to specific scenarios.This design not only enhances data privacy preservation but also prevents the transmission of trading risks to the data itself.Furthermore, in the designed data trading markets, data is treated as reusable goods, allowing for the reselling of data computing results.This enables traceability of data trading and usage, leading to enhanced data trading security.
Another challenge of data trading is to design a well-functioned data pricing mechanism to regulate all participants’trading behaviors, so as to enhance the supply and demand matching and improve trading efficiency [15], [16].Blockchain-based data trading differs fundamentally from traditional data trading as it eliminates the third-party intermediary and operates in a decentralized manner.Consequently, in trust-less trading markets, where comprehensive information for data may not be available, it is crucial to establish rational pricing mechanisms.Currently, the prevailing pricing mechanisms are query-based, game-based, and model-based[17]-[19].Among them, the approaches based on game theory and auction theory are widely employed for determining data prices [20], [21], since they prioritize the discovery of data prices for different trading characteristics and the evaluation of market dynamics rather than relying solely on calculations of cost and profit metrics.However, the majority of existing research on game-based data pricing mechanisms primarily focuses on distributed computing and shared service application scenarios, with limited work on designing pricing mechanisms specifically for direct data trading.Additionally,in trust-less data trading markets based on blockchain, there is the notable absence of analysis on the truthfulness of data pricing mechanisms, for incentivizing both the supply and demand sides to honestly report true valuations of data while discouraging strategic trading behaviors.
In order to address these research gaps in existing data pricing mechanisms and enhance data trading efficiency, we consider different data trading scenarios and propose the tailored pricing mechanisms for the multi-blockchain based data trading markets.For a regular data supply recorded in blockchain,we introduce auction-based pricing mechanisms to sell it to multiple users.For a temporary data supply not recorded in blockchain, we design a reverse-auction-based pricing mechanism to match it with specific demands.Both pricing mechanisms are designed to discourage strategic trading behaviors in their respective data trading scenarios.
In summary, this paper contributes in studying data trading by providing a multi-blockchain framework, tailored pricing mechanisms, and empirical evidence of their benefits in terms of data security and trading efficiency.
The remainder of this paper is organized as follows: Section II formulates the two-layer data trading markets within multiblockchain framework, and outlines the data recording and trading process; Section III introduces different data pricing mechanisms for the formulated markets; Section IV provides experimental verification and analysis; Section V summarizes this paper and discusses future work.
II.DATA TRADING MARkETS BASED ON MULTI-BLOCkCHAIN
The framework of multi-blockchain based data trading markets is illustrated in Fig.1.It includes a multi-blockchain infrastructure and two-layer markets constructed on top of it.
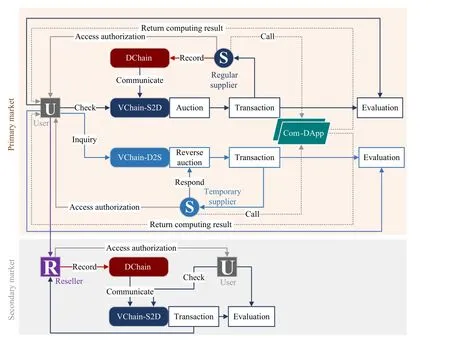
Fig.1.Data trading markets based on multi-blockchain.
The underlying infrastructure consists of two types of blockchains: The data blockchain (DChain) responsible for data recording, and the value blockchain (VChain) managing data trading.In particular, two distinct VChains are established to accommodate different data trading scenarios.Specifically, VChain-S2D is designed for trading regular data supplies that have already been recorded in DChain.This scenario involves demand being increased for existing data supply.Besides, VChain-D2S is intended to be used for trading temporary data supplies that have not been recorded in DChain.This scenario pertains to reverse trading where the supply responds to the proposed data demand.Multiple blockchains within the framework can be customized with different permission controls.Access to DChain is restricted to data owners and authorized users with valid purchasing records.This design not only ensures data security but also enhances efficiency by leveraging the scalability of the multiblockchain framework, which mitigates potential efficiency reductions resulting from high concurrency arising in various data trading functions.
On the basis of the multi-blockchain framework, the twolayer data trading markets are established with the primary market for initial data trading and the secondary market for resales of data computing results.In the primary market, once the data is recorded in DChain, its descriptive information will be updated in VChain-S2D through cross-chain protocols and smart contracts [22], [23].Users can access VChain-S2D to check for matching data supplies.If a matching supply exists,users can submit their purchase requests to VChain-S2D.If no matching supply is found, users can submit their demand offers in VChain-D2S and await responses.In the secondary market, users are allowed to resell the computing results of the purchased data through VChain-S2D.
A. Initial Data Trading in the Primary Market
1)The Data Blockchain: DChain is constructed as a consortium blockchain.Both data owners from the consortium organizations and ordinary data owners endorsed by enough positive data trading evaluation have authority to submit data to DChain.Only after data owners obtain the legal data records in DChain with the help of validators, they officially become the regular suppliers.
Suppliers independently decide to store data locally or on DChain.In general, data with privacy preservation requirements will be stored locally.If the data is stored locally,DChain only records its hash value and descriptive information including data ID, address, name, size, type, granularity,update frequency, time, etc.If the data is stored on DChain,the encryption algorithm is used to ensure data security throughout the whole lifespan of data recording and trading.
When a piece of data (the whole data set or only its descriptive information) is submitted to DChain, data validators are randomly selected to validate its authenticity and validity.Although the number of validators is fixed, the validator sets vary for different data.The selected validators will join in an exclusive channel of this data which cannot be accessed by other validators.Besides of the hash value and descriptive information, a sample of very small fragment is drawn randomly for each validator to assist data confirmation.Each validator gets a different data sample that cannot be viewed by others.Only when the proportion of validators confirming the data reaches the preset threshold, can it be recorded to DChain.After the confirmation results are returned, the samples will be hidden and can not be viewed by the validators any more.However, if there is a dispute over the confirmation results, these samples can be checked by the arbitration tribunal.When the data is recorded into DChain, its descriptive information will be updated to VChain-S2D immediately and users in need can purchase it through VChain-S2D.
The data validators will be rewarded with data confirmation fees paid by the data suppliers.For simplicity, we assume that each regular supplier only has one data record (i.e., data supply).To prevent validators from arbitrarily recording data into DChain stimulated by the over-high associated fees, we calculate the data confirmation fee according to data scale and granularity.
Here,fidenotes the confirmation fee of dataipaid by its supplier, which is determined by the data scalesiand the data granularityli.For example, we can establish a linear functionto calculate data confirmation fees, where γsand γlare the fee coefficients of data scale and granularity,respectively.
2)The Value Blockchains: Different from DChain, VChains can be either consortium blockchains or public blockchains.Regular suppliers sell their data via VChain-S2D, while temporary suppliers sell their data via VChain-D2S.There is no selection mechanism of transaction validators in VChains, and all of them can actively participate in confirming data trading.To prevent collusion, data validators in DChain are prohibited from confirming data trading in VChains.However, there are no exclusive obligations for trading validators, and they have the freedom to join both VChains.We view all trading validators as a whole to discuss their confirmation fees from confirming and recording data trading for users.
a)VChain-S2D: In VChain-S2D, the pricing mechanism is determined by suppliers to maximize their payoffs from matching the data supplies reasonably with users’ demands.Since data is a special type of goods that can generate different values for different users with various uses, suppliers know the costs of producing and managing data but cannot precisely get users’ valuations on data.Taking these into consideration, we adopt the auction-based mechanism to price the data in VChain-S2D.
There are multiple built-in auction models in VChain-S2D for suppliers to select, and the ranking rule and payment rule of each auction model are public knowledge of all suppliers and users.All auction models can be automatically executed by predefined smart contracts without human intervention.Suppliers have rights to select the auction mechanisms for their data and change them dynamically, but they must be determined before each round of data trading auction and kept unchanged at least until the end of this round.

Meanwhile, the winning users with a trading recordwill get computing results of the data after providing their models in two ways.If the data is stored locally, the winning users will be authorized to access the computing results provided by the supplier.If the data is stored on DChain, the supplier can also call the computation decentralized application(Com-DApp) to execute data computing, and the computing results will be returned to all winning users via the encrypted on-chain transmission.Here, Com-DApp integrates a series of smart contracts, and can provide data computing capability for all participants in the blockchain-based data trading markets.
After regular data trading is confirmed and recorded, the data trading validators will receive confirmation feespaid by the winning user.We adopt the fee model of mandatory basic fees plus voluntary extra tips, that is
The basic fee rate is represented byθ, which is combined with users’ payments to jointly affect the data trading validators’ revenues.In addition, users can also provide extra tips to encourage validators to confirm their trades in priority, which is denoted by.Since the data trading volumes and prices are not precisely known when validators are initially involved in data trading to provide confirmation service, they have no idea about total basic fees and extra tips generated from the final data trading.As such, it is very difficult for them to filter out low-value data trading intentionally.However, since the revenue-maximized validators will carefully predict data trading and make confirmation strategies accordingly, this fee model will also encourage earlier confirmation of high-quality, high-value and high-volume data trading.
Finally, the ex-post evaluation mechanism is applied to guarantee reliable data trading and safeguard interests of all participants, under which all winning users are requested to score the data supply after trading is completed.To prevent users’ malicious evaluations from damaging suppliers’ interests as well as weakening their enthusiasm to provide data,some measures are taken as follows.First, the median of all user-submitted scores is used as the final scoreei.Second,users are encouraged to provide evidence of their evaluations especially for the overly-high or overly-low scores, e.g., the model performance enhanced by the data.Third, users are allowed to resell the purchased data computing results at the price they are willing to accept, but the gains need to be shared with data suppliers, which will be elaborated in Section II-B.As a result, if users maliciously undervalue their purchased data, their own gains will also be damaged.
b)VChain-D2S: In VChain-D2S, the pricing mechanism is determined by users to make their data demands receive proper responses.Usually, users have the pre-valuation of their required data, but have no exact information of its quality and supply cost to precisely evaluate its value.In addition,the complete demand response in VChain-D2S may be comprised of multiple data supplies, and users cannot price them independently under this case.However, these multiple supplies are not complementary to each other as that in the distributed computing tasks, because values they bring to users are independent.As such, the pricing method based on calculating the marginal contribution is not applicable.Taking these into consideration, the reverse auction model is used to realize data pricing for the reverse trading of temporary data supplies.
First, the userjproposes a data demand with precise requirements and pre-valuationvjto VChain-D2S.Suppose each user only submits one data demand, and his/her pre-valuation is only publicized to data trading validators and unknown by suppliers.Furthermore, the reverse auction modelcis publicized and the response time deadlinetˉjis set by the user.
Once the demand is recorded in VChain-D2S at time, the data ownerk∈Kj={1,...,mj} who possesses the matching dataandacceptsthepricingmodel can submithis/her responsewith thelowestquotethat theyare willingto accept.The data owner who has a legal response record is referred to as a temporary supplier.
At timetˉj, the reverse auction model is powered by smart contract to select winners from the temporary suppliers.Only when the reverse auction process and results are confirmed to be legal by data trading validators, they can be recorded into VChain-D2S.The winning suppliers will have legal data trading records, while other suppliers only have the quote records.Then, the winning supplierk∈Kj?which has a legal trading record will be paid at the priceby the userj.Meanwhile,the user will get data computing results from the winning suppliers or Com-DApp after providing his/her computing model.The trading prices will be discussed in the following three cases.
i)If thedemand is respondedtobyonesupplier,whenthe quoteislessthan the user’svaluationvj,the onlytemporarysupplierwillbe thewinner,and willgetpaid atthe pricecalculatedaccordingtothe reverse auctionmodel.
ii) If the demand is responded to by multiple temporary suppliers but satisfied by only one data supply, the user determines the final winnerk∈Kj?as well as his/her payoff.
iii) If the demand is satisfied by multiple suppliers, the user not only needs to determine the winner setbut also assign a proper priceto each winning supplier.
Accordingly, the user’s total payments are
After reverse data trading is confirmed and recorded, the data trading validators will also get confirmation feesgjpaid by the user.Similarly, the fee model based on mandatory basic fees plus voluntary extra tips is used.That is,
whereδjis the extra tip per winning data supply
Finally, the user is asked to submit the evaluation scoreekfor the temporary data supply he/she purchased.From the above analysis, the temporary suppliers can only passively wait for users’ demands and respond to them in VChain-D2S;while the regular suppliers can actively submit data to DChain, and allow for it be purchased by more users in VChain-S2D.To encourage more supply of high-quality data,the temporary supplier can be upgraded to be the regular supplier and access DChain, when the evaluation scores accumulated from the successful data trading exceed the specified threshold.
B. Data Resales in the Secondary Market
In the secondary market, users can become the reseller and get paid by reselling the purchased data computing results.Because the data computing results are essentially processed data, it is very hard to provide new values to them via further computation.Also, they are faced with fierce competitions from not only the data supplies in the primary market but also the substitute computing results in the secondary market,which result in a relatively narrow audience.Moreover, their purchase costs are publicly known.Hence, the fixed price model is used in the secondary market.Considering the variations in data computing models as well as resellers’ preferences and costs, the resale price is determined from the individual perspective to maximize their payoffs in the secondary market.
The complexity of the computing model provided by the reseller is defined by μi,j(t).
Then, users can purchasewi,j(t)through VChain-S2D at the price set by the reseller.The resale price of the data supplywi,j(t)is a fixed priceri,j(t)calculated as
The competitive prices ofwi,j(t)are defined byand the resale volume is defined byxi,j(t).Besides, the value added to the data by the computing models μi,j(t)is also viewed as one of the key parameters of the demand functionxi,j(t).The resale payoffri,j(t)xi,j(t)will be further allocated between the resellerj(t)iand the initial data supplieriwith a predetermined weightβ.When the reseller optimizes their own payoff,it simultaneously optimizes the initial data supplier’s payoff in the secondary market.This compensation helps offset the potential negative impact of data resale on the initial data supplier’s revenues from the primary market.
The data trading validators will also get confirmation feesgi,j(t).Because the resale price is fixed in the secondary market, using the pricing model described by (3) will cause fees to be known before validators make their choices on data trading confirmation.Consequently, data trading with higher fees will be confirmed faster, while those with lower fees will be detained for a longer time.To avoid this situation and consider that the data has been confirmed previously in the primary market, the following fee model is used to determine the data trading confirmation fees in the secondary market:
Here, the confirmation fee for each data trading is fixed asgˉ.
Following the aforementioned process, the user can also resellthedatacomputingresultpurchasedfromthetemporarysupplierk∈Kj?.Withthe helpof datavalidators, it will be recorded into DChain and assigned a new ID aswk,j.Similarly, the data validators will get confirmation feesfk,jcalculated by the following fee model backed by the data scalethe data granularityand the complexity of computing modelμk,j.
Then, users can purchasewk,jthrough VChain-S2D at a fixed pricerk,jgiven by the revenue-maximizing userj.
Here,rk,j-is the competitive prices andxk,jis the resale volume.Afterwk,jis successfully resold, the payoffrk,jxk,jwill be allocated between the resellerjand the initial supplierkwith a preset weightβ.During this process, the data trading validators will get confirmation feesgk,j,
Similar to the primary market, users in the secondary market are required to provide evaluation scores for the purchased data computing results.To prevent abusive data resale from harming data suppliers’ profits, the resold data computing resultswi,jandwk,jare prohibited from reselling again.
III.THE PRICING MECHANISMS
In multi-blockchain based data trading markets, it is necessary to motivate suppliers and users properly via well-functioned pricing mechanisms that are aimed at reducing strategic bidding and quoting behaviors while encouraging honest data exchange.In what follows, we will discuss their payoffs and design the auction model and reverse auction model for data pricing in VChain-S2D and VChain-D2S, respectively.
A. Auction-Based Pricing Mechanism in VChain-S2D
The regular supplierican not only get paid by selling data through VChain-S2D in the primary market and also wins the payoff share from users’ resale of data computing results in the secondary market.Accordingly, his/her payoff function is
However, we can barely optimize the payoff from the secondary market by adjusting the pricing mechanism.Therefore,this section focuses on studying the auction-based pricing mechanism in the primary market.
The regular supplier first selects an auction model with the purpose of maximizing the total payments provided by winning users in the primary market.Then, each user individually determines the bid under the selected auction model aimed at optimizing the trading cost represented by the required payment.Consequently, the data trading game can be viewed as a sequential game, where the regular supplier is the first-mover taking a favorable position and benefiting from making his/her strategy of selecting the auction model as a hard constraint faced by users.To prevent the supplier from abusing this first-mover advantage and excessively squeezing users’ profits as well as prevent users from gaming the auction rule through adjusting the bids arbitrarily, rational auction mechanisms should be designed to balance the payoffs of both regular suppliers and users.As such, we attach importance to the incentive-compatibility of the auction-based pricing mechanism in data trading, under which users can simply set bids truthfully at their valuations and suppliers can stably extracts revenues from selling data.In light of the impact of data demand scale on auction results, different auction models are used for data trading under different demand scale (i.e.,the number of bids).
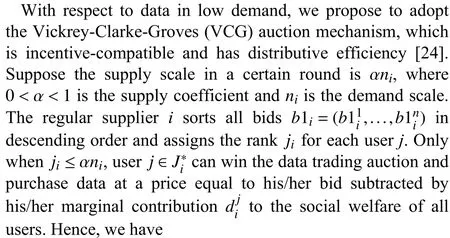
The user’s marginal contributionis calculated by
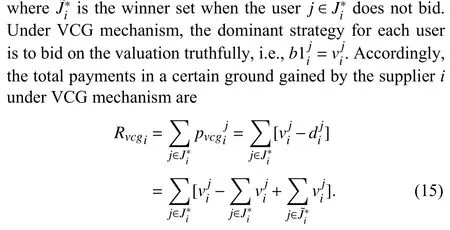
However, the VCG mechanism has a deficiency where its computational complexity will be elevated by the increasing demand scale [25], and thus may harm data trading efficiency in the multi-blockchain based markets.Consequently, we propose to use the monopolistic price (MP) mechanism for data in high demand, which is proven to be nearly incentive compatible when the demand scale is large enough [26].Under the MP mechanism, given all the bids ranked in the descending orderthe supplier needs to jointly determine the monopolistic pricepmpiand the corresponding supply scalejmpito maximize the monopolistic revenueRmpi.
All winning users pay the monopolistic price equal to the lowest bid offered by them.That is,pmpi=b1jmpi.Accordingly,
Then, the total payments gained by the supplieriunder the MP mechanism are
Different from the VCG mechanism, the MP mechanism is not strategy-proof, and users can benefit from shading their true valuations and submit lower bids under the MP mechanism.However, these strategic behaviors of users will gradually vanish with the increasing demand scale, because the benefits becomes very close to zero and the risk of losing the auction increases when the demand scale is large enough.
B. Reverse-Auction-Based Pricing Mechanism in VChain-D2S
The temporary supplierkearns payoffs from responding to the data demanddjthrough VChain-D2S in the primary market and gets the payoff share from reselling data computing results in the secondary market.His/her payoff function is
Given the dependence of the payoff share in the secondary market on resellers’ strategies, we mainly discuss the reverseauction-based pricing mechanism in the primary market.
The main objective of the reverse auction model in VChain-D2S is to ensure that the user can purchase data with high returns and the temporary suppliers can be properly rewarded in data trading with payment allocation.With this in mind, we design a reverse auction mechanism called the two-stage obscure selection (TSOS) mechanism, which consists of two stages: the potential supply selection based on the suppliers’quotes and the final winner selection based on the user’s evaluation on each potential data supply.
With respect to the potential supply selection, the quotes are accepted as long as they are lower than the user’s pre-valuationvjin view that it is very difficult for user to screen out the desirable data without exact information.Hence, the potential supply set is constructed as, the user needs to further determine the final winning suppliers as well as data prices for them.
Assume that honest users and suppliers agree on the ranking of these data in terms of their valuations; however, their valuations do not have to be completely identical.Under TSOS mechanism, the potential supplier will be asked to provide a data computing sample to VChain-D2S.However, The corresponding relation between the sample and the data will not be disclosed to the user at this stage.To avoid dishonest data sample provisions, the retrospective mechanism will be launched after data trading is realized, which mainly measures the deviation between the computing results from the data sample and the complete data supply.If it surpasses the allowable range, the supplier is considered to be fraudulent and will be severely punished.The user then checks these samples and submits his/her valuationunder anonymity.
After that, the corresponding relation of the data and its sample will be sent to the user so that he/she can calculate the returnon all potential supplies.We sort them in descending order to get
The demand scalem?is determined according to the user’s valuation constraint.
Ifm?=1, the data with the highest return will be the only supply and paid by its quote.
In the case where multiple data have the same highest return, the one with the highest valuation will become the final winner.
Ifm?>1, the user needs to allocate the payment among the winning suppliers.The one with the highest return is called the first winner and will be paid by his/her quote plus an extra reward; and the other winning suppliers are called ordinary winners and will be paid by their quotes.
The user’s payoff under TSOS mechanism is
From the perspective of data supply, we discuss whether suppliers honestly submit true valuations as their quotes.Usually, the supplier responds to the data demand with an optimal quote with the purpose of maximizing the payoff gained from the user.
Lemma 1: When the supply scale becomes sufficiently large, the rational suppliers under the TSOS mechanism get to be nearly truthful.

This implies that when there are a sufficient number of potential supplies, the supplier can barely increase the payoff by submitting a higher quote.

From the perspective of data demand, we discuss whether the user truthfully evaluates each data sample and determine final winners as well as their payoffs.
Definition 1(Demand-Side Incentive Compatible(DSIC)):The TSOS mechanism is DSIC, if the user maximizes the payoff by honestly submitting the true valuations on all potential data supplies.
Theorem 2: Whenm?=1, the TSOS mechanism for trading the temporary data in VChain-D2S is DSIC; while whenm?>1, it is not DSIC, but the user’s gain from strategic valuation is restricted.
Proof: The objective of the user in trading temporary data is to select the data supply with the highest return and pay as little as possible.On the basis of Lemma 1, it is easy to find that the user cannot increase his/her payoff by changing the winning supply set by giving strategic valuation on data supplies,i.e.,otherwise the data with higher return will be excluded while the data with lower return will be bought.Consequently, we will discuss whether the user can minimize the payment via strategic valuation on the premise that the most profitable data supplies are selected.

Based on the above analysis, TSOS mechanism is deemed DSIC whenm?=1 while not DSIC whenm?>1.■
IV.ExPERIMENTAL ANALYSIS
The main purpose of the experimental analysis is to evaluate the performance of the multi-blockchain data trading markets and the associated pricing mechanisms.Because these three blockchains have isolated data storage, individual permission control and different node networks, the data trading markets based on them can guarantee privacy preservation and data security by nature.As such, the emphasis will be on evaluating the proposed pricing mechanisms.
The experiments are conducted on a multi-blockchain platform by using the data trading within a famous power grid group in China as an example.The platform is developed on the hyper-ledger Fabric, and the operating system is Ubuntu 18.04.It consists of three independent consortium blockchains and they cooperate to fulfill the diverse data trading functions.All nodes run in the unified blockchain platform and use the same blockchain infrastructure, but we assign different roles and permissions to each node represented by departments from different branches.There are 2000 user nodes and95 supplier nodes in the multi-blockchain platform.
To realize cross-chain communication, we randomly select a fixed number of nodes from the validator set in DChain to form the anchor node set.The anchor nodes join both DChain and VChains, and can also play the role of verifying data in DChain.They are responsible for transmitting the descriptive information of data from DChain to VChain-S2D and also the data trading information and the suppliers’ evaluation scores from VChains to DChain.An entry-exit mechanism is set based on the evaluation scores, under which the regular suppliers receiving 5 negative evaluations will have their access permission of DChain invalidate and the temporary suppliers receiving 1 0 positive evaluations will be granted permission to join DChain.
Based on the above setting, the experimental verification of pricing mechanisms of multi-blockchain based data trading markets are carried out from the perspective of their equilibria.For simplicity, we do not consider validators’ confirmation fees in the following experiments.
In the experiments on the auction-based data pricing mechanism in VChain-S2D, one data supply is randomly chosen from more than 5 000 data sets.We are authorized to use these data sets to do scientific analysis and tests.According to real data trading, the bids it received have fallen into the interval of [10,100] (unit: thousand Yuan).We then randomly generate users’ bids under the case where the number of bids is 1 0,20, 50, 1 50 and 6 00, respectively.
To prove whether the MP mechanism and VCG mechanism are incentive compatible under different demand scales, we let each user’s bid be equal to his/her true valuation and then analyze whether the equilibrium under this setting is stable.The experimental results are shown in Figs.2 and 3.

Fig.2.The comparison of supplier’s payoff under VCG and MP mechanisms.
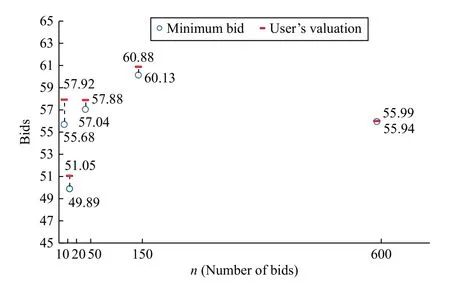
Fig.3.Strategic adjustment space of users’ bids under MP mechanism.
According to Fig.2, the regular supplier’s payoffs from data trading under the MP mechanism are distinctly higher than that under the VCG mechanism in the case of small demand scales.However, the truthful-telling strategy of bidding with users’ real valuations cannot converge to a stable equilibrium under the MP mechanism, since the user with the bid equal to the monopolistic price can revise the bid downward to reduce his/her own payment as well as that of other winning users.This will consequently reduce the supplier’s payoff under the MP mechanism.Fig.3 shows that the strategic adjustment space of users’ bids is eroded as the number of bids grows.When the number of bids increases to 600, the strategic adjustment space of the lowest ranked winner that restricted within the interval from the minimum bid to his true valuation is almost vanished; meanwhile the supplier’s payoffs under both auction mechanisms get to be nearly equal.Under these mechanisms, users can simply submit bids truthfully without the need for price estimation or adjustments as the demand scale grows, thus the data trading efficiency can be guaranteed.
We also compare the proposed auction-based pricing mechanism with most common ones, namely the generalized first price (GFP) auction mechanism and the generalized second price (GSP) auction mechanism [27], [28].Here, we take the case of 1 50 bids as the example to conduct comparative analysis, which is described by Fig.4.In multi-blockchain based data trading markets, the MP mechanism and VCG mechanism are essentially the uniform-price auction mechanism,while the GFP and GSP mechanisms are discriminatory-price auction mechanisms.Although the truth-telling strategy under the discriminatory-price auction mechanism seems to extract higher payoffs for suppliers, they are not stable and cannot reach equilibrium.Because users have motivations to submit lower bids for higher returns, this leads to drastic drop of the supplier’s payoffs.Their frequent adjustments on bids will reduce data trading efficiency.
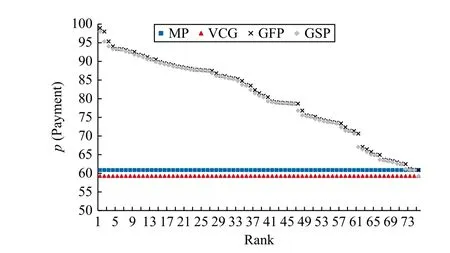
Fig.4.Users’ payments under MP, GFP, GSP, and VCG mechanisms for 150 bids.
In experiments on the reverse-auction-based data pricing mechanism in VChain-D2S, one data demand is produced with pre-valuation of 1 00 (unit: thousand Yuan).We then randomly generate the temporary suppliers’ quotes under the case where the number of quotes is 1 0, 20, 50, 1 50 and 6 00, respectively.The experimental results are shown in Figs.5-7.
When there is only one winning supply (i.e.,m?=1), we can see from Fig.5 that the strategic adjustment space of suppliers’ quotes under the TSOS mechanism is reduced by an increased supply scale.When the number of quotes reaches 600, it is reduced to less than 0.14%, and will keep shrinking to nearly zero with a rising number of quotes.As discussed in Section III-B, the user should rationally assess the value of data supplies and then determine winning ones.Here, we take t he case of 150 quotes as an example to verify whether the user will truthfully give a valuation on each data.From Fig.6,the highest return is 1.13, under which the user cannot improve his/her payoff by deviating from the true valuations.The experimental results confirm the properties of the TSOS mechanism discussed in Lemma 1 and Theorem 2.
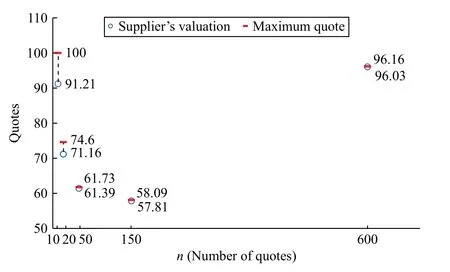
Fig.5.Strategic adjustment space of suppliers’ quotes under TSOS mechanism when m ?=1.
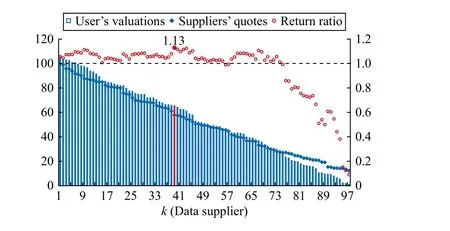
Fig.6.Equilibrium of TSOS mechanism when m ?=1 for 150 quotes.
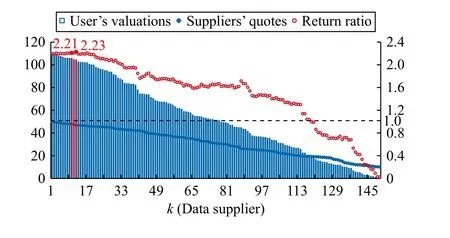
Fig.7.Equilibrium of TSOS mechanism whenm?>1 for 150 quotes.
When there are more than one supplier (i.e.,m?>1), we see from Fig.7 that there are two winning suppliers with return of 2.23 and 2.21 respectively, where the first winner can get paid by 87.12 and the ordinary winner can get paid by 47.79.For the first winner, a lower quote will make him/her keep the current position or be an ordinary winner, both of which will cut down the payoff.Especially, becoming the ordinary winner will make his/her payoff slump to 4 7.19.For the ordinary winner, elevating the quote by only 0.01% will make him/her lose the auction while a lower quote will result in the first winner reducing the quote, thus it would not be able to make his/her payoff any higher.Here, a similar trend of diminishing quoting strategy adjustment space by rising number of quotes is also revealed.However, the user can slightly reduce his/her valuation on the first winner by 0.87% so as to improve the payoff.The experimental results also validate the theoretical analysis of the TSOS mechanism described by Lemma 1 and Theorem 2.It has proven that TSOS mechanism can induce nearly truthful trading behaviors in reverse data trading scenarios, and the trading efficiency will not be harmed by the self-interested adjustment strategies and the resulting unbalanced payoffs.
V.CONCLUSIONS AND FUTURE WORk
With the aim to guarantee data security and enhance data trading efficiency, this paper is committed to establishing multi-blockchain based data trading markets and designing the pricing mechanisms tailored to different trading scenarios to regulate trading behaviors and strike a balance between the benefits of both suppliers and users.These markets use multiple blockchains not only to record and trade data separately but also to trade regular and temporary data independently.Furthermore, this paper introduces tailored pricing mechanisms to facilitate blockchain-based trading in the absence of precise data information.Different auction mechanisms are employed based on the scale of demand, promoting truthful bidding strategies in regular data trading.Additionally, a novel reverse auction model is designed to counter strategic quoting by suppliers and strategic valuation by users in the trading of temporary data supply.Experimental results validate the effectiveness of these pricing mechanisms in shaping trading behaviors and enhancing trading efficiency in multiblockchain based data trading markets.
In the future, there will be a focus on the inclusion of confirmation fees when designing pricing mechanisms for blockchain-based data trading, since they are integral to trading costs and economic systems of blockchains [29], [30].Additionally, the resale of data in the secondary market has a substitute effect on data supply in the primary market.Hence,its influence on the demand scale and bids of data supplies in the primary market should be considered in pricing data.Furthermore, another potential research direction is the exploration of decentralized data trading markets based on decentralized autonomous organizations and operations (DAOs)[31]-[34], to attract a larger number of individual data owners and facilitate fair collaboration for data supply.
 IEEE/CAA Journal of Automatica Sinica2023年12期
IEEE/CAA Journal of Automatica Sinica2023年12期
- IEEE/CAA Journal of Automatica Sinica的其它文章
- A Game Theoretic Approach for a Minimal Secure Dominating Set
- Knowledge Transfer Learning via Dual Density Sampling for Resource-Limited Domain Adaptation
- Subspace Identification for Closed-Loop Systems With Unknown Deterministic Disturbances
- Magnetic Field-Based Reward Shaping for Goal-Conditioned Reinforcement Learning
- GenAI4Sustainability: GPT and Its Potentials For Achieving UN’s Sustainable Development Goals
- Resilient Event-Triggered Control of Connected Automated Vehicles Under Cyber Attacks
