Multi-Candidate Voting Model Based on Blockchain
Dongliang Xu,Wei Shi,Wensheng Zhai,and Zhihong Tian
Abstract—Electronic voting has partially solved the problems of poor anonymity and low efficiency associated with traditional voting.However,the difficulties it introduces into the supervision of the vote counting,as well as its need for a concurrent guaranteed trusted third party,should not be overlooked.With the advent of blockchain technology in recent years,its features such as decentralization,anonymity,and non-tampering have made it a good candidate in solving the problems that electronic voting faces.In this study,we propose a multi-candidate voting model based on the blockchain technology.With the introduction of an asymmetric encryption and an anonymity-preserving voting algorithm,votes can be counted without relying on a third party,and the voting results can be displayed in real time in a manner that satisfies various levels of voting security and privacy requirements.Experimental results show that the proposed model solves the aforementioned problems of electronic voting without significant negative impact from an increasing number of voters or candidates.
I.INTRODUCTION
A.Motivation and Significance
ELECTRONIC voting is an online voting method based on cryptography technology.Voters can vote conveniently online through mobile phones,computers,and other terminals[1].This method will automatically count the votes and display the voting results.However,existing electronic voting models are frequently disputed by the public due to their opacity and vulnerability to loss of voting data,breach of personal privacy,and hackers’ attacks stemming from the centralization of data storage and the generated voting results.
Since the birth of Bitcoin [2]in 2008,digital currency has steadily gained attention.From 2014 onwards,researchers have intensively focused on its underlining technology,namely,blockchain.Its decentralization,anonymity,and nontampering characteristics have led to research on its applicability to credit investigation,trade,finance,Internet of vehicles [3],smart campus virtualization platform [4],and other fields.
The application of blockchain technology to electronic voting can significantly improve its anonymity,eligibility,and impartiality through data decentralization,anonymity,nontampering,and other features,as well as its functions such as automatic vote counting and examination with a smart contract.Szabo [5]defined smart contracts as a set of commitments in a digital form,including agreements on which contract participants can enforce these commitments.An agreement is a set of rules that both parties must abide by,and commitments include contract terms for implementing business logic and rules-based operations that define the nature and purpose of the contract.The digital form indicates that the contract will be composed of codes whose output can be predicted and executed automatically.Developing an efficient and effective smart contract that adapts to necessary security levels remains a problem to be tackled.On the basis of blockchain and smart contracts,this study uses an elliptic curve encryption algorithm for signature and verification.This study proposes a general electronic voting model based on blockchain,which is implemented and tested in Hyperledger Fabric.Furthermore,this study compares the security objectives and application scope with existing models.It leaves the investigation of a new secure blockchain-based solution for electronic voting to the future work.
B.State of the Art
With the development of Internet technology [6]and cryptography,online electronic voting has become a new voting solution that can effectively solve the disadvantages of traditional paper voting such as high cost,tedious steps,and numerous errors.Existing electronic voting models mainly include ring and blind signature-based,anonymous channelbased [7],homomorphic encryption-based,and hybrid network-based electronic voting models.Generally,ring and blind signatures require anonymous channel and a trusted third party (TTP) as signatories,whereas homomorphic encryption and hybrid network have high computational complexity,making them difficult to put into practice.

Fig.1.Blockchain schematic.
Chaum [8]proposed the first electronic voting model,which adopted the public key cryptosystem,and used digital false name voting to hide the identity of the voter; thus,any party concerned could verify whether the ballot was fully counted by using digital false name voting,thereby realizing the integrity of votes counting.In 1985,Cohen and Fisher [9]suggested an electronic voting model based on homomorphic encryption,which required the entire voting process to be kept synchronous.Benaloh and Tuinstra [10],Sako and Kilian[11],and Iverson [12]presented their own electronic voting models based on homomorphic encryption,but each model has advantages and disadvantages and is impractical with large-scale transmission and high-intensity calculation,thereby making them unsuitable for large-scale voting.
The first practical large-scale scenario of an electronic voting model (i.e.,FOO) was proposed by Fujiokaet al.in 1992 [13].In this model,the roles of voting participants are voting initiator,voter,and vote-counting persons,who use blind signature and bit-promise technology to encrypt the voting information and send it to a TTP to count the votes.Evidently,the model can neither abandon the vote nor completely guarantee whether the TTP is credible.However,the model still attracts considerable attention,and many universities and research institutions have improved and developed the corresponding electronic voting software system.However,any of the above-mentioned electronic voting models,including the FOO,must be based on a TTP,a credible counting body,to count the votes.Such centralization is a huge risk to voters’ privacy and will lead to data tampering and loss.Given that these protocols have a TTP and require voters to trust the TTP,users are unable to detect and defend against collusion attacks by counting agencies and regulators.The existence of these problems will lead to the distrust of users and thus restrict the promotion of electronic voting.
In 2002,Kiayias and Yung [14]proposed the first electronic voting model that was capable of self-counting and used open third-party voting procedures to count votes; moreover,these researchers introduced a fault-tolerant mechanism,which is applicable to small-scale scene voting,to correct “faults” in the voting process.Haoet al.[15]presented a two-round anonymous voting model with a self-counting function in 2010,thereby significantly improving the efficiency,calculation cost,and number of rounds because this model did not require anonymous channels.Such electronic voting models with self-counting capability weaken the TTP,convert the counting process into a publicly verifiable process,and allow any party concerned to perform and verify the counting process after all votes have been cast,thus weakening the unique status of counting institutions and enhancing the credibility of electronic voting.
In recent years,with the popularity of Bitcoin,the underlying blockchain technology has also gained the attention of many researchers.As shown in Fig.1,blockchain[16]is involved in any number of nodes in the system.A ll information is stored over a period of time through the calculation of cryptography algorithm and records in data blocks.In addition,the generated data “password” is used to verify the validity of the information and links to the next block and jointly by all participating node systems to decide whether the record is authentic.In the blockchain,to maintain the same data in the whole chain and ensure the fairness of each participant,all participants must have a unified protocol;that is,the consensus mechanism solves the problem of unifying data [17]in the blockchain and the problem of trust caused by proceeding to the center [18].
Blockchain is essentially an open,transparent,nontamperable distributed database ledger technology [19]that records all transaction information.In the absence of thirdparty intermediaries,blockchain has the characteristics of decentralization and non-tampering,which is conducive to solving problems such as difficult verification,privacy disclosure,and tampering with votes.Moreover,a smart contract can complete the self-counting function and realize the automatic vote counting process.
Recently,researchers developed many applications in accordance with these characteristics.Leeet al.[20]proposed a blockchain-based voting platform in 2016 to conduct national-level elections.The paper only gives a description of the process of the model and requires a TTP to conduct hidden user votes and vote counting.Yan and You [21]used the distributed ElGamal encryption system and zero-know ledge proof protocol; they also designed and developed a blockchain voting platform based on Ethereum and adopted the digital signature identity access mechanism to ensure the identity legitimacy of voters.In this paper,we propose a secure electronic voting model for additional candidates,and a smart contract,which was implemented in the TTP.The proposed model is designed to replace the traditional voting protocol in order to decrease the cost of the trust system.Using a digital signature (i.e.,the identity of the access mechanism to ensure the legitimacy of voters’ identity),a voting blockchain platform is designed and developed on the basis of the etheric fang platform.
Crameret al.[22]first proposed the problem of multicandidate voting in 1996 and suggested a “1-out-of-m” multicandidate voting model (i.e.,selecting one candidate among multiple candidates).However,considering that the model uses the ElGamal homomorphic encryption system,the calculation is complex.Thus,the model cannot be extended from 1-out-of-mtok-out-of-m(i.e.,multiple candidates are selected from multiple candidates) type voting.In 2006,Zhonget al.[23]proposed ak-out-of-mmulti-candidate voting protocol that combined secure multi-party and multiprecision computation without central trusted institutions.This model satisfies the characteristics of anonymity,fairness,and non-repeatable voting of electronic voting and is a favorable solution.
C.Elliptic Curve Cryptography Algorithm
The encryption algorithm and key distribution [24]and management mechanisms [25]used in this study are mainly based on elliptic curve cryptography (ECC).ECC is used to establish public key encryption [26]based on elliptic curve mathematics.The use of the elliptic curve mathematics in cryptography was introduced in 1987 by Koblitz [27]and M iller [28].
The mathematical basis of ECC is the in solubility of elliptic curve discrete logarithm problem (ECDLP).Discrete logarithm problem on elliptic curve: known elliptic curveEp(a,b)on finite fieldFp,and the pointG(x,y),X(X=xG,x A fter studying the existing electronic voting models and the characteristics of blockchain,we introduce the following requirements that a blockchain-based secure [29]electronic voting model must satisfy: 1) Legitimacy:The voting activity initiated by the poll sponsor shall be reviewed to ensure that the content of the poll is presented in accordance with the requirements of the law.Moreover,voters must satisfy the voting requirements and thus,unqualified voters are prohibited from voting. 2) Anonymity:The identity of the voter is hidden.The content of the ballot will be encrypted to prevent the ballot information from being stolen maliciously and then leaked to affect the voting process. 3) “Unforgeability”:The attacker cannot forge the voting information,and the recorded legal voting information cannot be tampered with.Voters can verify whether their votes are correct and valid through the model to ensure that the voting results cannot be forged. 4) Self-Counting:Third-party or manual vote counting is no longer necessary when the final result of a voting is counted by the model and the vote results are automatically updated.The voting process shows when a vote is cast,and the voting result changes accordingly without revealing the voters’specific voting content. In this paper,we propose an electronic voting model ofkout-of-m(i.e.,voters can selectk,k∈[0,m]frommcandidates) based on the blockchain technology.The model uses the characteristics of blockchain to decrypt every ballot under the premise of guaranteeing the anonymity of voters,namely,the model can perform complex transmission of voting information without compromising voters’ identities.Most importantly,the model is not limited to a specific implementation of a certain blockchain.The voting model can be realized provided that the blockchain platform uses ECC asymmetric encryption and has access to mechanism and as mart contract. In this model,the main participants are the counting nodeV0,the verified voters (V1,V2,...,Vn),the candidates(C0,C1,...,Cm?1),voting initiatorI,andKcandidates (Kis a variable).Among them,the voting initiatorImust ensure that the content of the voting is in compliance with relevant laws and regulations,and voters must be verified to have the right to vote to enter the blockchain network (such as uploading some certification materials).Given that the two requirements mentioned above have different verification standards in various situations,this model assumes that the two requirements have been established. 1) Counting Node and Votes:The counting nodeV0in the model is automatically generated by the smart contract afterIsuccessfully initiates the voting and is deployed on the node provided by the initiator.This node becomes the counting nodeV0and cannot be logged into by any user.It only serves as the communication object of each voter and is responsible for recording and displaying the voting situation.Counting nodes can be considered as special contract accounts in the existing Ethereum and Hyperledger Fabric platforms. whereG(x,y) is a point in the elliptic curveEp(a,b),in which,in the given finite fieldFp,nis the order ofG;XV0is the public key ofV0;andxV0is the private key ofV0.The votecounting nodeV0generatesXV0andxV0using formula (1) and broadcasts itsXV0to all nodes before the voting start timeTstart. Voters in the model (V1,V2,...,Vn) are the user nodes that can be logged into and constitute the main body of the voting activity.A fter legitimacy verification,the user can access the blockchain network and become the new voter.Voters select candidates and vote.Voters as nodes are part of the blockchain and keep accounts in accordance with the consensus mechanism to ensure the authenticity and credibility of information on the chain. whereG(x,y)is a point in the elliptic curveEp(a,b),in which,in the given finite fieldFp,nis the order ofG;XV1···Vnare the public keys of (V1···Vn);andxV1···Vnare the private keys of(V1···Vn).The vote-counting nodes (V1···Vn) generateXV1···VnandxV1···Vnusing formula (2) and broadcast theirXV1···Vnto all nodes before the voting start timeTstart. 2) Voting Information:The model supportsk-out-of-mtype voting,and the voting informationmesencoding mode is ambit binary number converted into a decimal number as shown in Table I. 3) Voting Anonymity Confusion Algorithm:The use of blockchain for electronic voting also raises new questions.In the case of voting,e.g.,the encrypted information transmitted during a vote and the time will be recorded on the blockchain.Among them,mesis invisible through encryption.However,in accordance with the voting time of different voters recorded on the chain and the number of votes changing in real time displayed byV0,the voters’mesis completely infeasible to infer.Given this situation,we propose an anonymitypreserving voting (APV) algorithm for voting to ensure the anonymity of the model. A lgorithm 1 APV A lgorithm Require: P//Maximum number of mixed voters mes1···mesC( )//Votes information r1,r2,...,rmEnsure: R( )//The number of votes startp=1 restC=Cwhile do//The number of remaining voters restC>P+1//The number of remaining voters is greater than the maximum number of mixed voters plus one 2,Pp∈[2,P]p=Rand( )//Generating a random number messtartp···messtartp+p?1) V0 mes g=( )// received pof and divided them into group g? ∈for rgdo Wait(p)//Wait for a multiple of p(ms)Update(R,r)//Update the total number of votes Rbased on r restCrestC?p==startp startp+p p=restC g=( )// received the last pof and divided them into group g mesC?p···mesCV0 mes? ∈for rgdo Wait(p)//Wait for a multiple of p(ms)Update(R,r)//Update the total number of votes Rbased on r 1) Voting Information Transmission:As shown in Fig.2,the voting informationmsgis transmitted after encryption in the blockchain.The following information is an example of the voting data transmission of the voting nodeV1to illustrate the information encryption transmission and verification method of the model. a)V1generatesmesV1:V1selectskcandidates to vote for.The selected candidates code is 10···01,and voting information ismsgV1=2m?1+1. TABLE IENCODING b)V1generatesDV1: whereis a random integer selected byV1(ris not necessarily equal tor′),andx(1) is the abscissa of.The encryptedEIV1is generated byV1usingXV0in accordance with Formula (1). c)V0decryptsCIV1:V0receivedCIV1=(c1,c2) fromV1. wherenis the order ofG. If this is true,thenmesV1is confirmed to be sent byV1and is thus not a forgery. 2) Voting Process:After the voting is successfully initiated,Isets the voting start timeTstartand the voting end timeTend.BeforeTstart,V0generatesXV0andxV0,and broadcastsXV0;nqualified voters (V1,V2,...,Vn) access the blockchain network and generate {XV1,XV2,...,XVn},{xV1,xV2,...,xVn},and broadcast {XV1,XV2,...,XVn}.BetweenTstartandTend,each voter selectskcandidates and sends the encrypted information to the counting nodeV0.V0is responsible for identifying the voter,counting the qualified votes,and displaying the current voting result.As shown in Fig.3,the following is an example of the voting process of the voting nodeV1to illustrate the voting process of this model: V1selectskcandidates,so the selected candidate code is 10···01,form informationmesV1=2m?1+1.DV1is signed usingmesV1andxV1in accordance with the above-mentioned signature method.EIV1is encrypted usingDV1andXV1in accordance with the above-mentioned encryption method,andEIV1is sent toV0. A fter receivingEIV1fromV1,V0decryptsEIV1to determineDV1under the control of the smart contract and then verifies the signature inDV1usingXV1;if successful,thenmesV1is sent byV1and is not faked.Then,XV1is used as a mark to verify that this voter is a first-time voter.A fterward,mesV1is counted,andV1is marked as having voted.The voting informationEIV1is written into the blockchain. V0automatically counts the qualified votes received and shows the voting result by using Algorithm 1 under the control of the smart contract. When the time reachesTend,all users who have not voted will automatically generate voting informationmes=00···00.Then,it will be sent toV0.AfterV0has received the information of all voters,the final voting result is calculated. 3) Decentralized:In the previous sections,we the use the concept of a counting node in the proposed model.It generates voting information and stores it in the blockchain network during interactions with the voters.However,the counting node is not a centralized database or a TTP in the traditional sense.Instead,it is essentially a node deployed by one or a group of smart contracts in the blockchain.The difference between the counting node and a voting node is that certain smart contracts must be executed on the counting node in order to complete the counting function.A ll the encrypted information generated by a voting activity will be recorded in the block,and the block is confirmed to be valid through the consensus mechanism,then stored in each participating node.Furthermore,the ballot can be modified solely by the counting function,which avoids the centralization risk of traditional electronic voting strategies. We have proposed ak-out-of-mvoting model based on blockchain.In this section,the Hyperledger Fabric implementation model is adopted,and Hyperledger Caliper is used for the performance test to evaluate the accuracy and security properties of the model and compare it with other models.The Hyperledger Fabric [30]is a blockchain framework implementation by the Linux foundation,which leverages container technology to host smart contracts called“chaincode” that comprise the application logic of the system.The node deployed by chaincode can be considered our voting node. Docker Compose [31]is a tool for defining and running multi-container Docker applications.We can use an Ain’t markup language (YAML) file to configure the application’s services with it.Then,with a single command,we implement and start all the services from our configuration in the YAML file.Therefore,we use Docker Compose to start multiple node containers on a single machine with the Hyperledger Fabric,rather than multiple physical machines,for experiments.Fig.4 illustrates the system architecture for model validation based on the Hyperledger Fabric. In Fig.4,voters use voting peers,which can be seen as voting nodes by the voting system,to access the blockchain network.The Certificate Authority node guarantees the access of voting nodes is legitimate; the orderer node guarantees the consistency of the voting information of each voter,the endorser node takes charge of verifying signatures,and the smart contract node takes charge of implementing smart contracts.The endorser node and the smart contract node can together be regarded as the counting node. We used Hyperledger Caliper [32]for performance testing[33].This tool is used for a blockchain performance benchmark for Hyperledger Burrow,Fabric,Iroha,and Saw tooth.Currently,the supported performance indicators are success rate,transaction,read throughput transaction,read latency,and resource consumption.Moreover,the system uses a consensus mechanism based on Kafka [34]. Fig.4.System architecture diagram for model validation. 1) Relationship Between Number of Voters and Model Performance:The relationship between the number of voters and the performance of the model was tested.In the fabric network we implemented,the number of voters is the same as that of peer nodes,and the number of candidates is 10.When the performance of the model,the limit on the number of votes is temporarily removed,that is,each node can vote without limit.This is because if the number of votes is limited,the number of pieces of valid voting information will never exceed the number of nodes,and the performance cannot be tested in the case of a small number of nodes.In our experiment,each node votes or queries 1000 times at a specific frequency,referred to as the Send Rate.The experimental results are presented as follows. In Figs.5 and 6,vote refers to the voting operation,query refers to the operation of searching the voting result,Send Rate refers to the number of operation requests per second,Avg Latency refers to the average time delay of each operation,and Throughput refers to the number of completed operation requests per second.The delay of query illustrated in Fig.5 is approximately 0.02 s,and the throughput rate depicted in Fig.6 is close to the Send Rate.That is,every operation request can be processed in time,and the number of voters has no impact on the performance of query operation.In Fig.5,a vote’s delay increases rapidly with the Send Rate and slightly with the number of nodes.In Fig.6,the increase in the Send Rate of a vote’s time-dependent throughput rate rises slightly.Furthermore,the throughput rate decreases slightly with the increase in the number of nodes.Moreover,in actual conditions,each node will conduct a qualified vote once,and the delay and throughput rate of the voting operation are acceptable.As illustrated by the experimental results,the throughput rate and time delay of the voting operation as well as the viewing of voting results in the smallscale voting scenario satisfy the requirements of the model. 2) Relationship Between the Number of Candidates and Performance:The model we designed is suitable for the “kout-of-m”-type voting because the size of the voting information depends onm.Thus,we must test the impact of different numbers of candidates on the performance of the model.The following experiment uses 4peers-1order(i.e.,the number of voters is 4),and the voting quantity limit is temporarily removed.Each node votes or queries by 1000 times in accordance with the different frequencies.The experimental results are presented as follows. Fig.5.Avg Latency with different numbers of voters. Fig.6.Throughput with different numbers of voters. In Figs.7 and 8,vote refers to the voting operation,query refers to the operation of searching the voting result,Send Rate refers to the number of operation requests per second,Avg Latency refers to the average time delay of each operation,and Throughput refers to the number of operation requests that can be completed per second.In Fig.7,when the number of candidates is not too large,it slightly influences the voting delay.The delay is too increased only when the number of candidates is very large.The number of candidates has a very minor influence on the delay of the query.In Fig.8,when the number of candidates is relatively small,it slightly influences the throughput of the voting.The throughput declines significantly only when the number of candidates is significantly large,whereas the number of candidates only slightly influences the throughput of a query.The number of candidates affects only the binary digits of the voting information.Thus,the influence the number of candidates has on the vote count hasO(n2) complexity.However,given that the counting process is simple,it only slightly influences the performance.The effect of the number of candidates on Algorithm 1 isO(n) complexity,with minimal impact on the performance. Fig.7.Avg Latency with different number of voters. Fig.8.Throughput with different number of voters. We tested the accuracy of self-counting by comparing the real results with the self-counting results.The actual voting time and the voting results were counted simultaneously to test the validity of Algorithm 1.In this experiment,the maximum number of mixed votes per node is 3.In addition,10peers-1order(i.e.,the number of voters is 10) is adopted,and the experiment is conducted in the case of 4 candidates.The experimental results are illustrated in Table II. TABLE IIMODEL SELF-COUNTING TEST The information presented in Table II is the voting information of the current voter,and the self-counting result is the real-time counting result displayed by the system when the current voter votes.Considering that the value ofpcannot be determined each time,the display delay of the voting results is completely random.In Table II,the voting information ofV3is 0010,and the difference between the self-counting result whenV3votes and the self-counting result whenV9votes are(0,1,1,1).Thus,the voting information ofV3cannot be inferred.Therefore,when the voting time and the selfcounting result time are known,the specific conditions of voters’ votes cannot be deduced regularly,but the current voting results can be displayed with a short delay,and the votes can be accurately counted after the voting ends.In addition,the entire vote counting process is conducted using a smart contract,and no artificial vote-counting drawbacks are observed.Given that the smart contracts are fully public,the voters can trust the results.Therefore,under the premise of guaranteeing anonymity,the model has the property of accurate self-counting. The legitimacy of voting is guaranteed by the access audit of blockchain.Given the different legitimacy standards of voting,legitimacy is not discussed in this study.However,some attackers that intend to falsify the voting results can still be qualified to access the blockchain network.For example,in scenarios with loose standards of legitimacy review,such as a referendum,the identity of attackers and eligible voters can overlap,that is,attackers may be part of the eligible voters.On this basis,we tested the security properties of the model. To facilitate the testing of the performance of the model,we must remove the limit on the number of votes,but the security test must limit each voter to one eligible vote.Subsequently,we used the node configuration of 10peers-1order,set the maximum number of mixed votes to 3,and conducted multiple experiments in the case of 4 candidates to test the security of the proposed voting model. The experimental results are provided in Table III,assuming the following scenario:VAis a qualified voter and an attacker in the voting link,andV1is a non-attacker voter,and decryption is a necessary step of the query.Results show thatV1decryptedEIV1successfully,butV1voting withXV1andVAdecryptingEIV1both fail.V1voting withXV1succeeded only once.The above-mentioned experiments confirm the two properties of the model.The analysis and proofs are presented as follows. TABLE IIIMODEL SECURITY TESTING 1) Property 1: Unforgeability:In Table III,the experiment ofV1voting withXV1only one time out of 100,thereby confirming thateach voter can vote only once in each voting activity,and the encoding of voting determines that each voter can vote at most once for each candidate.Therefore,a voter cannot forge a vote count. In Table III,VAfailed to vote multiple times withXV1,thoughVAhas the ability to send sending fake voting informationEIfV1(encrypted false voting information sent byV1)toV0with the public keyXV1,becauseVAhad determinedXV0,XV1,...,XVn.Then,V0receivedEIfV1and decrypted it withxV0under the control of the selected smart contract.Therefore,V0could determineD fV1,includingmesfV1andDfV1,and verify the signature forDfV1withXV1to obtainmes′fV1.becauseVAdid not havexV1.Finally,V0could determine that theEIfV1received is a forgery and would not write it to the blockchain.In summary,VAcould not vote asV1without a corresponding private key.That is,each voter cannot vote as another voter and falsify the result. Given that our proposed model is based on the blockchain implementation,and the information stored on the chain is the encrypted voting information,the qualified voting data that has been recorded could not be tampered.During all tests,no manual operation was performed during the counting process,and no random change in the votes was observed.In summary,the proposed model ensures the unforgeability of voting information and results. 2) Property 2: Anonymity:Anonymity is mainly reflected in separating voters from their voting information.In our model,anonymity is enabled by encrypting the transmission of voting information as well as performing Algorithm 1. Except for the time stamp,the parties pass the information and the fixed relevant information in the blockchain.All the information passed and written to the block in the blockchain network isEI.Thus,all voters can provide allEI.As shown in Table III,all instances ofV1decryptingEIV1were clearly successful,but all instances ofVAdecryptingEIV1failed.In fact,ifVAaims to observe the voting informationmes1,then it mustobtainxV0,which can be converted from the solution of ECDLP[27].However,in 2017,Kusakaet al.[35]used the parallel Pollard ρ algorithm to solve a 114-bit pairing-friendly Barreto-Naehrig curve by spending six months on 2000 CPUs.Because ECDLP is unsolvable when the data size scales up,which is why obtaining the voting information of other voters through the decryption ofEIis not feasible. The experimental results and arguments summarized in Table III confirm that the specific voting information of voters cannot be inferred with the public information provided when Algorithm 1 is used in the voting model.Voters can not determine the specific voting information of other voters;thus,we conclude that the proposed model has achieved anonymity. We compared all the voting models discussed in this paper in terms of their voting methods,voting types,TTPs,counting methods,and the presence or absence of the mixed voting mechanism.The models involved in the comparison are all relatively mature voting models,which basically satisfy the anonymity and non-forgery requirements. The comparison results (see Table III) show that in terms of voting methods,unlike the FOO model,our proposed model uses the blockchain technology,thereby avoiding,problems caused by traditional electronic voting methods,such as the requirement for a TTP and the inability to unify votes in real time avoided.However,given the limitation of the blockchain technology,the throughput rate is lower in our model than in traditional electronic voting when the number of candidates scales up.This situation means that our model is suitable for small-scale voting scenarios.In terms of voting types,our proposed model supports “k-out-of-m” voting,which includes the “1-out-of-m” voting type of Yan’s model [21]with strong voting applicability.This model does not require a TTP to guarantee the voting process and results.A comparing with the model in [20],third-party vote-counting fraud is not an issue for our proposed model.Furthermore,our proposed model uses smart contract automatic vote counting,which is simpler and more efficient than the whole vote counting proposed in the model in [23].The smart contract code is open; thus,vote counting results are trustworthy.The vote counting result accuracy obtained by our proposed algorithm is much higher than that of the automatic vote counting proposed in the model in [15].In particular,A lgorithm 1 proposed in this study solves the problem of inferring the specific voting information of a voter on the basis of the available voting time and real-time voting results in the blockchain voting model,as shown in Table IV,thus,the model can display the voting results in real time without compromising the voters’ anonymity.In general,this model has great advantages in terms of anonymity,non-forgery,and self-counting and has disadvantages in its throughput rate in large-sized voting scenarios.Our proposed model is more suitable for small-sized and medium-sized voting scenarios. In this paper,we propose a “k-out-of-m” multi-candidate voting model based on blockchain technology that ensures: 1)the preservation of anonymity during the voting process through ECC encryption and a signature mechanism and 2)the prevention of forgery of voting information by combining blockchain technology,automatic statistics,and display of voting results through a smart contract.Furthermore,this study introduces an APV algorithm to mitigate the drawbacks of the blockchain voting method.We use the Hyperledger Fabric framework to conduct experiments on the proposed model.Hyperledger Caliper is used to test the performance of the model.Experiments are designed and tested extensively with respect to the security requirements of the model and the effectiveness and efficiency of the proposed APV algorithm.Through these experiments,we confirm that the model is particularly well suited for small-scale voting situations and overcomes the disadvantages of traditional electronic voting pertaining to lack of anonymity,excessive centralization,and ease of forgery. TABLE IVCOMPARISON OF KNOw N VOTING MODELSD.Security Requirements for Blockchain-Based Electronic Voting Models
II.K-OUT-OF-M ELECTRONIC VOTING MODEL
A.Model Establishment

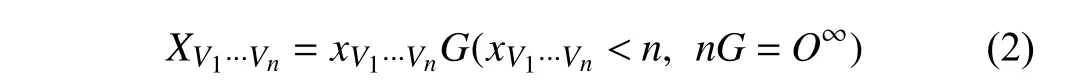

B.Model Specification




III.EXPERIMENT AND RESULT ANALYSIS
A.Experimental Environment and System Architecture for Model Validation
B.Model Performance Test





C.Self-Counting Accuracy Testing

D.Model Security Testing

E.Comparison with Existing Models
IV.CONCLUSIONS

 IEEE/CAA Journal of Automatica Sinica2021年12期
IEEE/CAA Journal of Automatica Sinica2021年12期
- IEEE/CAA Journal of Automatica Sinica的其它文章
- Toward Coordination Control of Multiple Fish-Like Robots: Real-Time Vision-Based Pose Estimation and Tracking via Deep Neural Networks
- Exact Controllability and Exact Observability of Descriptor Infinite Dimensional Systems
- Energy Control of Plug-In Hybrid Electric Vehicles Using Model Predictive Control With Route Preview
- An Optimal Control Strategy for Multi-UAVs Target Tracking and Cooperative Competition
- Adaptive Fuzzy Backstepping Tracking Control for Flexible Robotic Manipulator
- Blockchain-Based Secured IPFS-Enable Event Storage Technique With Authentication Protocol in VANET
