A Quantitative Security Metric Model for Security Controls: Secure Virtual Machine Migration Protocol as Target of Assessment
Tayyaba Zeb, Muhammad Yousaf, Humaira Afzal, Muhammad Rafiq Mufti*
1 School of Electrical Engineering and Computer Science (SEECS), National University of Sciences and Technology, Islamabad, Pakistan
2 Riphah Institute of Systems Engineering (RISE), Riphah International University, Islamabad, Pakistan
3 Institute of Computing, Department of Computer Science, Bahauddin Zakariya University, Multan, Pakistan
4 Department of Computer Sciences, COMSATS Institute of Information Technology, Vehari, Pakistan
Abstract: Quantitative security metrics are desirable for measuring the performance of information security controls. Security metrics help to make functional and business decisions for improving the performance and cost of the security controls. However, defining enterprise-level security metrics has already been listed as one of the hard problems in the InfoSec Research Council’s hard problems list.Almost all the efforts in defining absolute security metrics for the enterprise security have not been proved fruitful. At the same time,with the maturity of the security industry,there has been a continuous emphasis from the regulatory bodies on establishing measurable security metrics. This paper addresses this need and proposes a relative security metric model that derives three quantitative security metrics named Attack Resiliency Measure(ARM), Performance Improvement Factor(PIF), and Cost/Benefit Measure (CBM) for measuring the performance of the security controls. For the effectiveness evaluation of the proposed security metrics, we took the secure virtual machine (VM) migration protocol as the target of assessment. The virtualization technologies are rapidly changing the landscape of the computing world. Devising security metrics for virtualized environment is even more challenging. As secure virtual machine migration is an evolving area and no standard protocol is available specifically for secure VM migration. This paper took the secure virtual machine migration protocol as the target of assessment and applied the proposed relative security metric model for measuring the Attack Resiliency Measure, Performance Improvement Factor, and Cost/Benefit Measure of the secure VM migration protocol.
Keywords: attack resiliency measure;cost-benefit measure; performance improvement factor; security assessment; formal verification, security controls; security metrics;virtual machine migration protocol
I. INTRODUCTION
Investments in thefield of information security have increased significantly since last decade,however, it has been a matter of concern that still there exists no way that exactly measures the performance of the security controls or mechanisms that are put to protect the information systems. A widely accepted principle states that if you cannot measure it then you cannot manage it. NIST IR 7564 “Directions in Security Metrics Research” provides the recommendations for designing the security metrics for measuring the performance of the information security mechanisms [1].
A system is considered secure if no actual adversary can exploit it [2]. Generally, a system is made secure by deploying some security mechanisms that protect the system.Organizations in general and security designers often remain concerned about how much effective their security mechanisms are? Information security performance measurement is also gaining interest due to several regulatory requirements e.g. Government Performance and Results Act (GPRA) and Federal Information Security Management Act (FISMA)require measuring information security performance [3]. These factors are pushing security designers to develop metrics for assessing the security of the system. However, developing enterprise-level security metrics is a complex task and is listed as one of the hard problems in the Infosec Research Council’s Hard Problem List. So far, the efforts for developing enterprise level meaningful absolute security metrics have not been proved fruitful. However, some security metrics have been developed to measure the security of the specific attributes of the components of the security mechanisms [4].
This paper presents a quantitative security metric model for measuring the performance of security controls. A security control is an arrangement that provides some security service. For example, encryption is a security control that provides the confidentiality service, digital signature is a security control that provides the authentication service, firewall is a security control that prevents unintended traffic from entering or exiting the network,and an antivirus tool is a security control that prevents malicious software to execute on the computer system. Sometimes the terminologies of the security controls and the security mechanisms are used interchangeably. This paper takes the security control as a set of one or more security mechanisms that collectively provides the desired security services. For example, networking security protocol TLS(Transport Layer Security) can be taken as a security control that uses the mechanisms of symmetric key encryption, digital certificates and secure hash functions for providing the services of confidentiality, authentication and integrity respectively.
The approach presented in this paper has two dimensions. Initially, a security metric model is proposed which is used to devise three security metrics. These metrics have been named as i) attack resiliency measure, ii)performance improvement factor, and iii) cost/benefit measure. Although these measures are not new, how quantitatively measuring these metrics have been a challenging task. This paper quantitatively model and evaluate these metrics for the given security control. These metrics are generic in nature and can be used to measure security performance of different networking security protocol. A security protocol is a collection of one or more security controls intended for providing protection to the system. However, aggregation of multiple security controls in the name of security may result in the inherently less secure system,therefore, measuring the extent to which security controls are meeting their security objectives is a crucial factor. The proposed metrics provide efficiency of security controls in term of their resilience against several attempted attacks. Secondly, the absence of proper performance improvement metrics makes it hard to compare multiple security alternatives.The performance improvement metric provides the measure of the effectiveness of new security controls by comparing their current performance and previous performance of old security controls thus providing acomparative measure that whether the proposed security controls have increased/decreased the security performance or indicate if they had put no effect on the security performance of the security subsystem. Moreover, the cost-benefit measure (CBM) helps to identify that what cost is incurred for implementing the security control. These three metrics have been evaluated against two adversary models i.e. Dolev-Yao (DY) Attack Model and Key Compromise Impersonation (KCI) Attack model [5] [6].
The second dimension of this paper elaborates the target of assessment for proposed security metric model. The security protocol taken as the target of assessment for the proposed security metric model is secure VM migration protocol [7]. Area of Virtual Machine (VM)migration has captured wide scale attention.The process includes the complete transfer of operating system and applications running on one physical machine to another physical machine. Many of the hypervisors that support this process do not include a comprehensive solution for securing this process [8] [9]. As VM migration involves sending critical infrastructural information over the network,therefore, VM migration involves many security challenges. For example, unencrypted traffic may result in exposing machine states,secret keys and passphrases [9]. In literature,a few protocols have been devised for secure VM migration, however, it still lacks any standardization. In this regard, we have designed a lightweight protocol for secure VM migration and performed its performance modeling in our previous work [7]. This paper first proposes a quantitative security metric model and then evaluates this model using a secure VM migration protocol. In literature, majority of the work either performed the performance measurements of VM migration or identified the security problems and devised their solutions to handle those security problems. To the best of our knowledge, no work has been done on evaluation of the effectiveness of the security controls for the secure VM migration protocols.
Rest of the paper is structured as follows:Section 2 discusses the related work and their limitations. Section 3 discusses the need for security metrics. Section 4 presents the proposed relative security metric model. Section 5 describes the formal verification setup used to obtain the measurements for security metrics and section 6 discusses the results acquired from this setup. Finally, section 7 concludes the paper.
II. RELATED WORK
This section explores the work done in two dimensions. One is the area of developing quantitative security metrics in general and the other is the quantitative security assessment of secure virtual machine migration protocols.
2.1 Quantitative security metrics for security evaluation
Developing security metrics for the evaluation of security subsystems is an emerging domain and research community is putting emphasis on it. In literature, work has been done on qualitative metrics [10], however, they tend to be less precise as they only assign a ranking of bad, good or average to the system which can be misleading sometimes [11]. A lot of emphases has been put by standards and regulatory bodies to develop quantitative security metrics for the measurement of the security performance of security subsystems. For example,NIST Direction in Security Metrics Research[1] [3] recommends devising quantitative security metrics for measuring the efficiency and effectiveness of security controls.
Several approaches are proposed for measuring the security in thefield of network security [12], application security [13], control systems [14] and code safety inspection [15][16] using quantitative metrics. However, to the best of our knowledge, so far no metrics are devised that quantitatively measure the security performance of the security protocols and specifically secure VM migration protocols. A well-understood classification, taxonomy, and nomenclature are presented in the literature for security metrics [17] [18] such as technical vs. management level metrics,component vs. enterprise level, efficiency and effectiveness metrics. For example, Vaughn et al. [17] provided a classification of different information assurance and security metrics.Metrics that measure that how much a technical security control (referred as Technical Target of Assessment) is capable of detection,protection and response to attacks are termed as TTOA metrics. Authors further categorized TTOA metrics into metrics for strength assessment and metrics for weakness assessment.The former metrics consider two scenarios where security is assessed with and without the presence of an adversary.
Regarding the formulation of security metrics for network security, M. S. Ahmed et al. [12] made use of three measures such as existing vulnerabilities measure, historic vulnerabilities from National Vulnerability Database (NVD) and probabilistic vulnerability measure to evaluate the network security.An attack-propagation metric is devised using vulnerabilities measure to assess that how an attacker can cause an attack to propagate through the network by exploiting services vulnerabilities. However, the approach assigns a protection level of one to firewalls and between 0-1 to IDS (Intrusion Detection System)qualitatively as opposed to claimed quantitative metrics.
Lemay et al. [19] provided a model-based approach for the generation of security metrics. The approach takes adversary information, system information and desired security metrics as input. The proposed model assumes that a system is already aware of types of adversaries and their capabilities. Moreover, H.Wang et al. [13] has proposed security metrics for software systems. The measures for formulated metrics are taken from CVE (Common vulnerability Exposures) and CVSS (Common Vulnerability Score System). The results are taken against three different web browser applications. The author concluded that more the number of vulnerabilities, a software application has the lesser security it provides.Similarly, Wayne Boyer et al. [14] presented technical security metrics for control systems using ideal based approach.
Although most the work regarding security metrics emphasized on defining quantitative security metrics, however, comparatively little work is done on formulating the security metrics, performing experimentation and relating the outcomes with the objectives of the security metrics. The contribution of this paper is that it formulates the security metrics of attack resiliency measure for measuring the efficiency of the security control, performance improvement factor for measuring the effectiveness of new security controls and cost/benefit measure of security control.
2.2 Existing security metrics for secure vm migration protocols
This paper takes the secure VM migration protocol as the technical target of assessment(TTOA).In literature, a few approaches are proposed for secure VM migration but only performance evaluations have been performed in terms of migration delay, response time,downtime, etc. No work has been done on measuring the security performance of security controls adopted for secure VM migration.For example, William et al. [20] evaluated the cost of virtual machine migration in the cloud.A cost-benefit analysis using cloud computing along with the local datacenter is performed in [21]. Authors performed the assessment of performance gain of using cloud infrastructure by considering many of parameters including Job Slowdown time, Average Weighted Response Time, Average Number of Virtual Machines required by a task, Number of deadline violations, Performance Cost, etc.
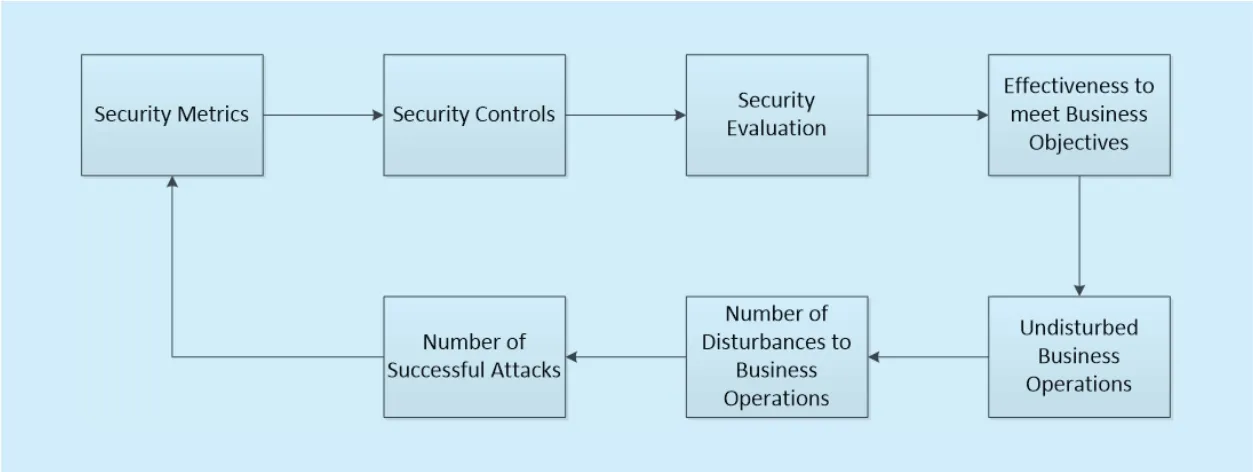
Fig. 1. Security controls, effectiveness, and relationship with business objectives.
Similarly, the parameter of performance degradation during cold virtual machine migration for CPU and memory intensive applications was evaluated in [22]. Authors studied the effect of migrating multiple virtual ma-chines at the same time. Performance parameters of downtime and total migration delay for live migration was quantitatively measured in[23]. Application downtime during virtual machine migrations over WAN with 1Gbps dedicated link was evaluated in [24]. Also, application slowdown time and downtime for live migrations within datacenterwere quantitatively measured in [20]. Authors considered the application response time during the migration process for measuring the performance. Virtual machine migration delay with respect to increasing bandwidth and propagation delay over WAN link is modeled in [7]. Authors also modeled the initial response time of migration protocol with respect to several handshake messages over WAN and compared the initial response time of proposed protocol with IPsec Internet Key Exchange (IKEv2) and Transport Layer Security (TLSv1.2).
A set of interfaces has been defined in [30]for the secure migration of virtual machines.Two computing nodes use public key cryptographic techniques to establish a secure session and then symmetric key cryptographic techniques are used to encrypt the virtual machine data. A descriptive analysis of the secure virtual machine migration on the basis of X.509 was presented in [31]. Different issues of live virtual machine migration have been presented in [32, 33, and 35]. In [32], authors also attempted to model the migration delay,service disruption time and the number of memory pages transferred. Also, authors presented some security requirements for the VM migration; however, security effectiveness has not been modelled. Similarly, in [35], authors modelled and evaluated the migration time and the throughput at the source node the migrating machine. In [36], the authors introduced a new metric called the eviction time which is used to model the migration delay of the VMs.The eviction time is still a performance metric and not the security metric.
These studies emphasized on the performance metrics of the virtual machine migration process and evaluation of security metrics for the migration process is largely neglected.This paper bridges this gap by presenting the security metrics and performs experimentation for assigning the quantitative values to the proposed security metrics.
III. SECURITY METRICS
This section briefly describes the basic concepts related to the security metrics, their requirements, benefits and fundamental types.It also describes that why absolute security metrics are hard to develop and why this paper proposes the relative security metric model.
3.1 Requirement of security metrics
With the significantly increased rate of security breaches, organizations in general and security designers often remain concerned about how much their system is secure. Information security performance measurement is also gaining attention due to several regulatory requirements e.g. Government Performance and Results Act (GPRA) and Federal Information Security Management Act (FISMA) require measuring information security performance[3]. Potential benefits of using security metrics are i) increased accountability, ii) fulfillment of compliance requirements, iii) improved the effectiveness of security subsystem, iv) quantitative values for resource allocation decision making, etc. These factors are pushing security designers to develop metrics for assessing the security of the system. However, developing enterprise-level security metrics is a complex process and meaningful security measures for this level could not get maturity. However,some security metrics have been defined to measure the security of the specific attributes of security subsystem [4].
Information security measures help to monitor the accomplishment of goals and objectives by quantifying the implementation,efficiency and performance improvement of security controls and identify possible improvements. Figure 1 shows the relationship of security metrics with business objectives.Security metrics are defined for the security evaluation of the security controls. These eval-uations help to determine the effectiveness of security controls and justify the investment in the security controls. Security controls are the safeguards to business operations. If there are attackers out there that may or have been attacking the business assets, then there arises the need to invest in the security controls so that the business operations may proceed smoothly. Measuring effectiveness of the security controls contributes towards determining the Return on Investment in the security controls.
3.2 Measurements and metrics
Measurement is referred to the process of data collection, analysis and reporting [3]. Information security measures must yield quantifiable information for comparison purposes.Although absolute metrics are often useful and desirable, however, in practice, relative measures such as percentages or averages are effective and achievable [3].
Measurements provide a single point in time view of specific factors. An example of measurement is a number of high severity vulnerabilities detected on a server by some vulnerability scanning process [25]. Metrics are derived by comparing to a predetermined baseline of two or more measurements taken over time. An example of metric is the change in a number of high severity vulnerabilities detected on a server this year as compared to the previous year’s value [25]. Therefore, metrics is a term used to denote a measure based on a reference and involves, at least, two points:the measure and the reference. Security metrics should tell us about the state or degree of safety relative to a reference point [26].
Effective metrics are often referred to as SMART, i.e. specific, measurable, attainable,repeatable, and time-dependent. Metrics should also indicate the degree to which security goals are being met and should drive possible actions taken to improve the security program [25]. Security metrics can be obtained at different levels within an organization [18] i.e.i) Business Level Security Metrics, ii) Information Security Management Level Metrics,and iii) Systems and Services Level Security Metrics.
Security metrics can be quantitative or qualitative, absolute or relative, and direct or indirect in nature [17] [18]. Qualitative metrics are based on the quality of some attribute of the system. Quantitative metrics are the results that can be presented as numbers. Absolute metrics use numeric values to represent the value of the measure in an absolute sense. Information security domain is full of many unknown quantities. As unknown quantities cannot be measured deterministically, therefore,it is hard to develop absolute security metrics[2]. Making comparisons of different attributes of a system is a basic process for deriving relative metrics [27]. Relative metrics are normally represented in terms of percentages or comparisons. Direct metrics are based on the values that can be measured independent of the other parameters of the system. Indirect metrics are based on the values that cannot be measured directly. They depend on the values of other parameters.
3.3 System and security subsystem
Let a system ‘S’ having some security subsystem ‘C’. If we change or enhance the security subsystem to mitigate some weakness or to provide some new security services, then the changed security subsystem is presented by C’≠C. As C or C’ are an integral part of the system S so, with changed C’ the system in the new state will be termed as S’≠S. S’ is considered a completely new system with a new set of weaknesses. When we apply some security control C it mitigates some weaknesses. However, there would still be some weaknesses that may not have been mitigated by the control C [2]. From the point of view of some viewer, some of the weaknesses will be known to the viewer and some will be left unknown to the viewer. Examples of these viewers range from the system owner to the adversary.
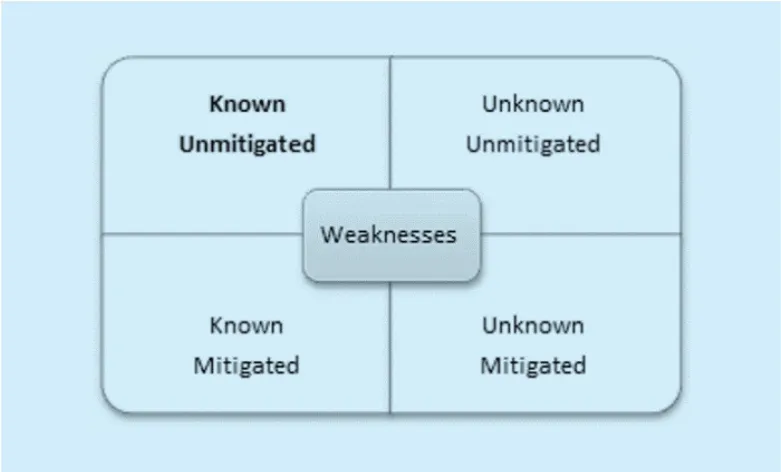
Fig. 2. Categories of weaknesses.
A realistic adversary is often modeled by considering its knowledge and resources with some realistic bound [2]. Set of exploitable weaknesses by an adversary is the intersection of the set of weaknesses known to that adversary and the set of unmitigated weaknesses as shown in figure 2. Weaknesses that are either unknown or mitigated are often of least concern. The fundamental goal of the security program is to reduce the set of exploitable weakness to zero. In absolute terms, this security goal is not achievable, because we don’t know the number of adversaries and their capabilities [2]. Therefore, this paper proposes a relative security metric model that can be used to quantitatively assess the relative attack resiliency, performance improvement and cost/benefit measure of the security subsystem.
IV. PROPOSED RELATIVE SECURITY METRIC MODEL
This paper presents a relative security metric model that is used to derive and formulate three security metrics i.e. i) Attack Resiliency Measure, ii) Performance Improvement Factor, and iii) Cost/Benefit Measure.
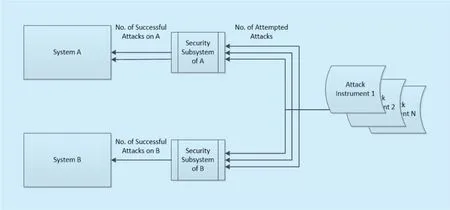
Fig. 3. Model for measuring attack resiliency measure and performance improvement factor of security controls.
4.1 security metric model
Proposed model depicted in figure 3, gives the relative security metric of attack resilience of the security subsystem against the attempted attacks. In order to state that how much system B is secure; we cannot give any absolute value. However, using the proposed model,relative security measure can be obtained to state that how much system B is secure as compared to the system A. To compare two systems, following conditions must be true:
? Two systems in comparison are of the same type
? Attack instrument is same
? Context is same
More often system A and B represent two different states of the same system i.e. system A may represent the previous state of the system with old security controls and system B may represent the new state of the same system with improved security controls and potentially may be less number of successful attacks.
Attack instrument is an instrument that is used to test the security strength of the security subsystem. Attack instrument does not enhance the security of the system rather; it is used to test and measure the resilience and performance improvement of the security control against attempted attacks. Different attack instruments can be used at different stages of the life cycle of the security controls i.e. at the design stage, the implementation stage, and the deployment stage. Attack instruments used at the design stage and the implementation stage represent the lab testing. An example of attack instrument that can be used at the design stage is formal adversary models and the example of the attack instrument that can be used at implementation stage is penetration-testing tools. Attack instruments used at the deployment stage represent thefield testing with some real-life adversaries.
4.2 Attack resiliency metric (ARM)
Attack Resiliency Metric measures the resilience or efficiency of the security control against the launched attacks. Efficiency generally describes the extent to which a factor is well used for the intended purpose. Let thenumber of all attempted attacks is the sum of the number of attacks blocked by the security subsystem and number of attacks successfully bypassing the security subsystem. Then attack resiliency measure of the security subsystem is the ratio of the number of blocked attacks by the number of all attempted attacks.
For number of attempted attacks > 0, following formula is used for calculating the attack resiliency measure of the security control:

Here, the impact of all successful attacks is taken as equal. However, the impact of different security attacks is not always equal.In most cases, it cannot be measured in an absolute sense. They are normally ranked with respect to their severity level i.e. low, medium, high. There is no consensus on how many numbers of low-impact attacks are equal to a medium or high impact attack. If such equivalence would have existed then a weighted average ARM formula would have been more appropriate and realistic.

As the total number of attempted attacks is relatively harder to calculate directly, therefore, it is estimated by the sum of the number of blocked attacks and number of successful attacks. Many of blocked attacks can be estimated from the alerts generated by the security subsystem such asfirewall, IDS, and antivirus programs. Similarly, many of attacks successfully bypassing the security controls can be estimated from the sum of anomalies detected by the systems, reported by the users and sometimes claimed by the attackers.
4.3 Performance improvement factor (PIF)
Performance Improvement Factor helps to quantitatively measure the improvement in the performance of new security control as compared to the old security control. Performance improvement factor allows comparing alternative security solutions by taking their efficiencies in terms of attack resiliency as input thus aids in decision making for the adoption of security control. The metric is calculated as:
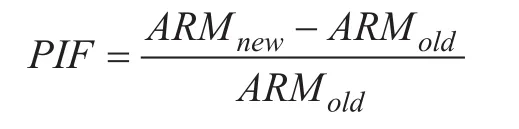
Here, ARMnew= Attack Resiliency Measure of security subsystem with new security control in place, and ARMold= Attack Resiliency Measure of the security subsystem with existing security controls.
In the case when ARMold=100%, there is no need of investing in new security controls.Similarly, when ARMold=0, then above mentioned PIF formula will produce infinite value. Therefore, for the calculation of PIF,following bound should exist:

with these ranges, performance improvement factor can be expressed as follows:

4.4 Cost/benefit measure (CBM)
Cost/benefit measure indicates that how much cost is incurred for providing the security service. Here, the cost can be taken in general e.g. cost of implementation, local resource utilization in terms of computation and memory, network resource utilization in terms of transmission overhead of extra messages for authentication and key exchange, etc. In this work, we considered only the local resource utilization cost that we modelled as the number of encryptions used to implement the security control. In our case, the security control does not significantly add additional network utilization therefore we took its value as negligible. Similarly, the benefit is taken as the efficiency with which a security control blocks the attempted attacks. In this sense,cost/benefit measure is the ratio of number of encryptions used by the security control to the attack resiliency measure of the security control against particular attack instrument. Although resource utilization cost of symmetric and public key encryption is different and also depends very much on the implementation,however, for the sake of simplicity, we took symmetric encryptions, public key encryptions and cryptographic hashes with equal weights.

As shown in table 1, ARM, PIF and CBM are Quantitative, Relative and Indirect measures in nature. Quantitative in terms that we calculate these metrics and assign numeric values to them. All three metrics are relative because they do not provide absolute sense. As we don’t have complete knowledge of weaknesses and number of adversaries and their capabilities, therefore, absolute security metric cannot be measured. ARM depends on upon the number of attacks attempted which can be computed only from the known and available attack instruments that is the incomplete set.PIF is relative because it is a kind of ratio of two ARM values. Similarly, CBM is relative because it is the ratio of cost to the efficiency measure. All three metrics are indirect. ARM is derived from the ratio of the blocked attacks to the number of all the attempted attacks and PIF is derived from the ARM values.
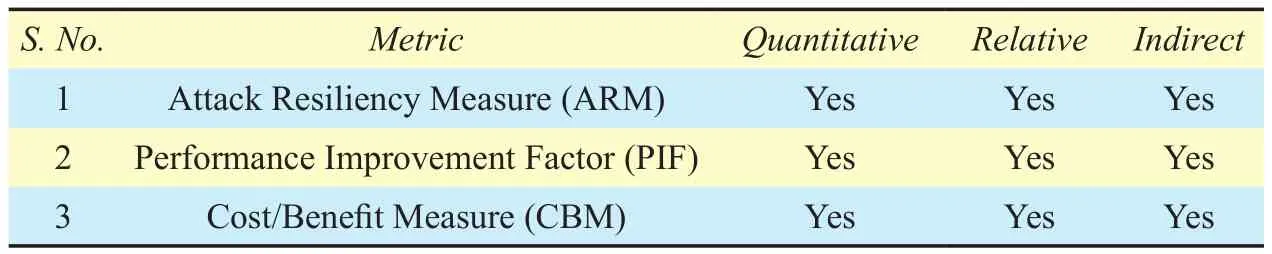
Table I. Summary of nature of metrics used in the proposed security metric model.
V. EXPERIEMTNAL SETUP
For the evaluation of the metrics presented in this paper, the proposed relative security metric model needs two components. One is the security subsystem as Target of Assessment(ToA) and other is the attack instrument. We took secure virtual machine migration protocol as the target of assessment and took a formal security verification tool as the attack instrument.
5.1 Secure virtual machine migration protocol as target of assessment
We took a secure virtual machine migration protocol as the target of assessment [7]. Virtual machine migration is an important feature of the virtualized computing environments in which virtual machine running on one computing node can be physically migrated to some other computing node without disturbing the services on the migrated virtual machine. At one side virtual machine migration provides many advantages like load balancing and fault tolerance in the virtualized environments,however, at the other side it also poses some security risks [30, 34]. In literature many security mechanisms have been proposed to mitigate these security issues [31], however, none of these modelled and quantitatively measure the effectiveness or the overhead of these solutions. This paper attempts to model and measure the effectiveness and the overhead of the security solution of the secure virtual machine migration protocol. The protocol is taken and evaluated in three different states of security controls using security metrics. These states are termed as the i) migration protocol with no security control, ii) migration protocol with the initial level of security controls, and iii) migration protocol with improved security controls.
5.1.1 With no security control
Virtual machine migration protocol with no security control represents the protocol state when no security is provided to the virtual machine migration process. We used this state to identify the number of threats to which migration protocol is vulnerable. In this state,migration protocol exchanges two initial control messages of migration request message and the migration response message. After a positive response message, the virtual machine migration data is sent and in response to this,the recipient sends back the acknowledgment.This process continues until all the data is transmitted at the destination end.
5.1.2 With initial security control
We took the secure virtual machine migration protocol presented in [7] as the migration protocol with initial security controls. The proposed secure VM migration protocol provides the security services of mutual authentication of two cloud domains, confidentiality of the VM data, the integrity of VM data, non-repudiation and identity protection. The content of the messages exchanged is given in table 2.We call it the VM migration protocol with initial security control because, during designed protocol analysis and formal verification, we found few unintended logical errors in protocol flow that may possibly result in many of security attacks. This methodology is generic and can be applied on any VM migration protocol proposed in the literature.

Table II. Message contents of secure VM migration protocol as initial security control.
where

and B

Table III. Message contents of secure VM migration protocol as improved security control.
5.1.3 With improved security control
The protocol vulnerabilities in the initial security controls state were mitigated by the modification of the protocol design. We call this modified security VM migration protocol as improved security protocol. These modifications include the addition of the service of the freshness of VM data, enforcement of order/symmetry of the messages exchanged and signature in the data and acknowledgment messages as shown in table 3. The lacking of these attributes or parameters was resulting in the introduction of new vulnerabilities in the protocol design which could be exploited by an attacker in future to launch some attack.
5.2 Attack models
We used the formal security verification tool scyther-w32-compromise-0.9.2 [28] as the attack instrument. Scyther is used for the automatic security verification of the network security protocols [38]. Three version of the secure VM migration protocol were modeled in scyther using SPDL (Security Protocol Description Language) and then two attack models i.e. DY attack model and KCI attack model are applied to the protocol. These attack models served as the attack instruments used to measure the values of the proposed security metrics.5.2.1 DY attack model
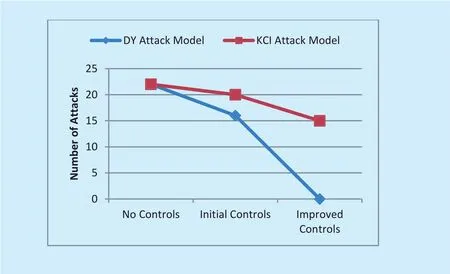
Fig. 4. Number of attacks using DY and KCI attack models with different security controls.
The first attack model used as attack instrument is Dolev-Yao model [5, 37]. This is a formal model to verify the properties of cryptography based security protocols. This model has two basic assumptions: i) network is under the control of attacker i.e. attacker can learn,intercept or spoof messages into the network,ii) second assumption which was later called as ‘Perfect Cryptography Assumption’ states that an intruder is only limited by the constraints imposed through use of cryptographic scheme and cannot decrypt any messages unless he has the decryption keys. In this model,conspiring agents or malicious insider/agent are those entities which conspire with the intruder and may provide him with some secret internal information. These abstractions are close to real time environment thus applying this attack model aids infinding out logical errors in protocol construction along with identification of various attacks that may possibly be launched.
5.2.2 KCi attack model
The second attack model is KCI (Key Compromise Impersonation) attack model. It is reasonably advanced and strong adversary model than DY attack model. It is stated as strong adversary model because it captures the resilience against key compromise impersonation attacks and provides the scenario where an adversary can reveal session keys, random numbers and long-term secret keys of participating nodes.KCI revolves around the property called Actor Key Compromise (AKC) which states that if an attacker compromises an entity A’s secret key due to whatsoever reason, A should still be able to securely communicate with other nodes depending upon the protocol used for communication [29] i.e. attacker must not be able to infer session key from the compromised long-term secret key. In the case of successfully launched KCI attack, an adversary with secret key knowledge of A can impersonate as A to some other node B [6].
VI. RESULTS
Figure 4 presents the number of successful at-tacks launched by two different attack instruments against different states of the security controls of the security subsystem. No control represents the state of the system when no security subsystem is available. Initial control represents the state of the system when initial level of security is applied to security subsystem. Improved control represents the state of the system when improvements are made to the security subsystem to thwart some specific attacks. We implemented the proposed secure virtual machine migration protocol in Scyther formal verification tool and used DY attack model and KCI attack model as sample attack instrument for our security metric model.Total twenty-two security claims are taken as reference. These security claims served as objectives of the security subsystem.
Figure 4 represents that with no security control in place, all the claims are compromised thus indicating that all the attacks launched by using DY and KCI attack models remained successful. With initial level security controls in place, some of the attacks are blocked while several attacks were still successful. With improved security control, all the attacks launched using the DY attack model are blocked, while some of the attacks launched by the KCI model are still successful.
Figure 5 represents the efficiency of the security controls in terms of Attack Resiliency Measure (ARM) against the DY and KCI attack models. As expected, with no control in place, the ARM value of the security subsystem is 0%. Whereas, with improved security control in place, the ARM value of the security subsystem is 100% against the DY attack model. However, the value of ARM is 32%against the KCI attack model.
Figure 6 represents the relative Performance Improvement Factor (PIF) of the improved security control with respect to the initial security controls against DY and KCI attack models. Positive values of PIF show that security of the system is increased with the improved controls of the security subsystem.PIF value corresponds to the effectiveness of the improved security controls.
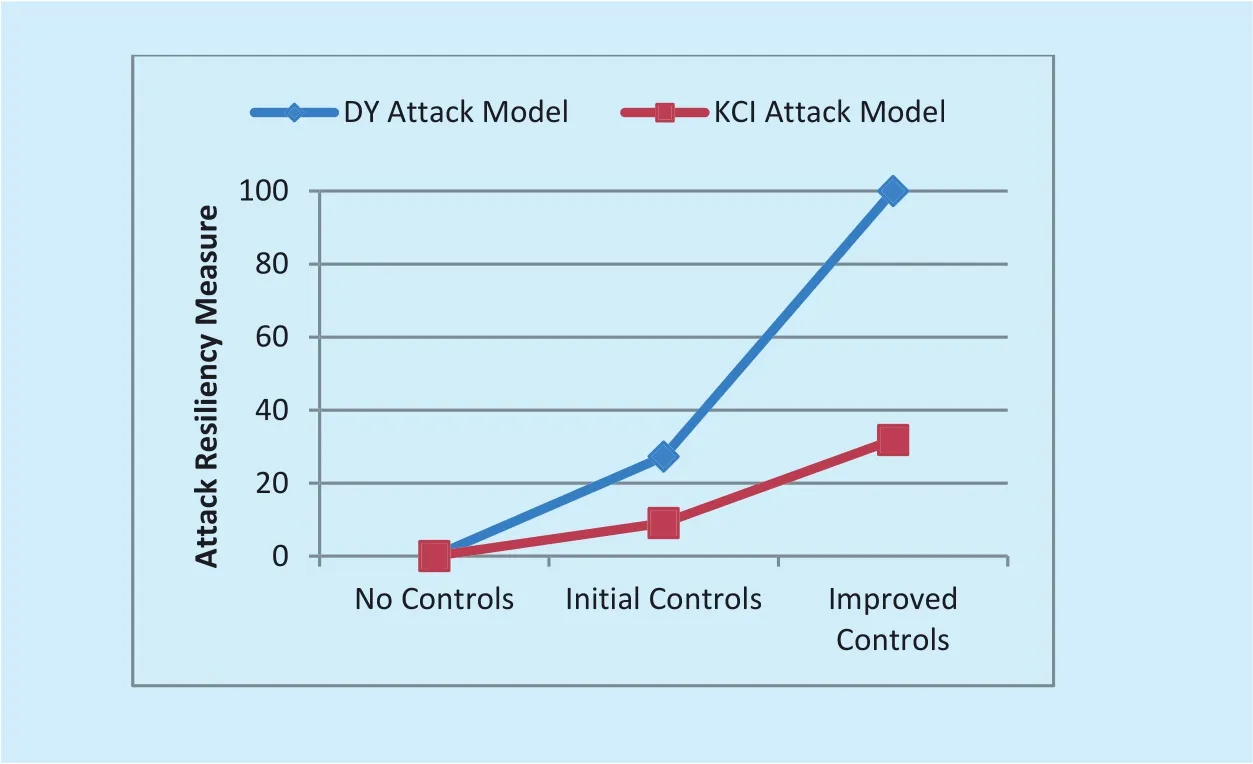
Fig. 5. Attack resiliency measure of different security controls against DY and KCI attack models.
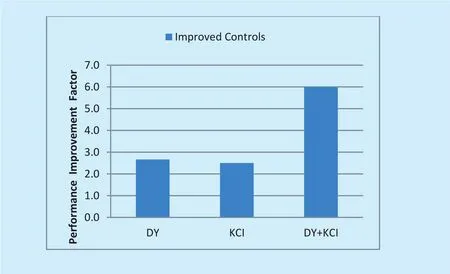
Fig. 6. Performance improvement factor of improved security controls with respect to initial security controls against different attack models.
Figure 7 shows the total number of encryptions used for implementing different security controls. These number of encryptions are used for calculating the cost/benefit measure of different security controls.
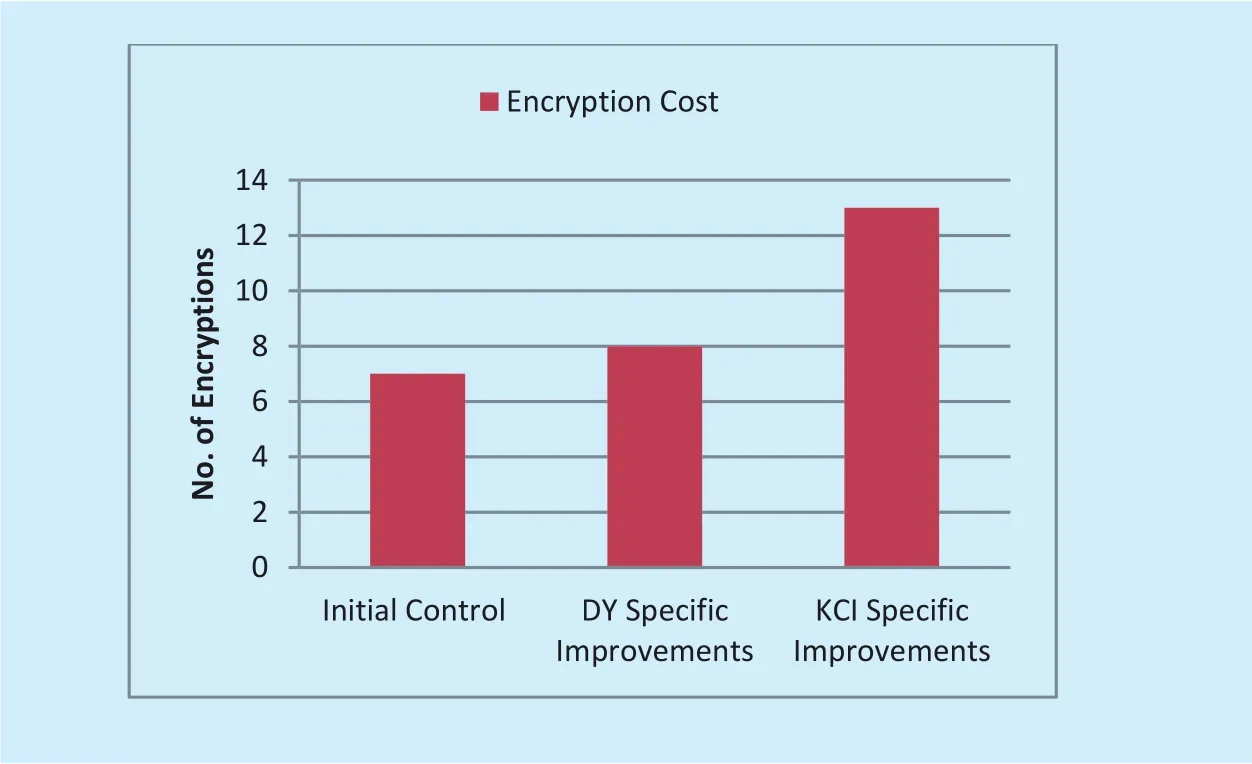
Fig. 7. Cost in terms of number of encryptions used in different security controls.
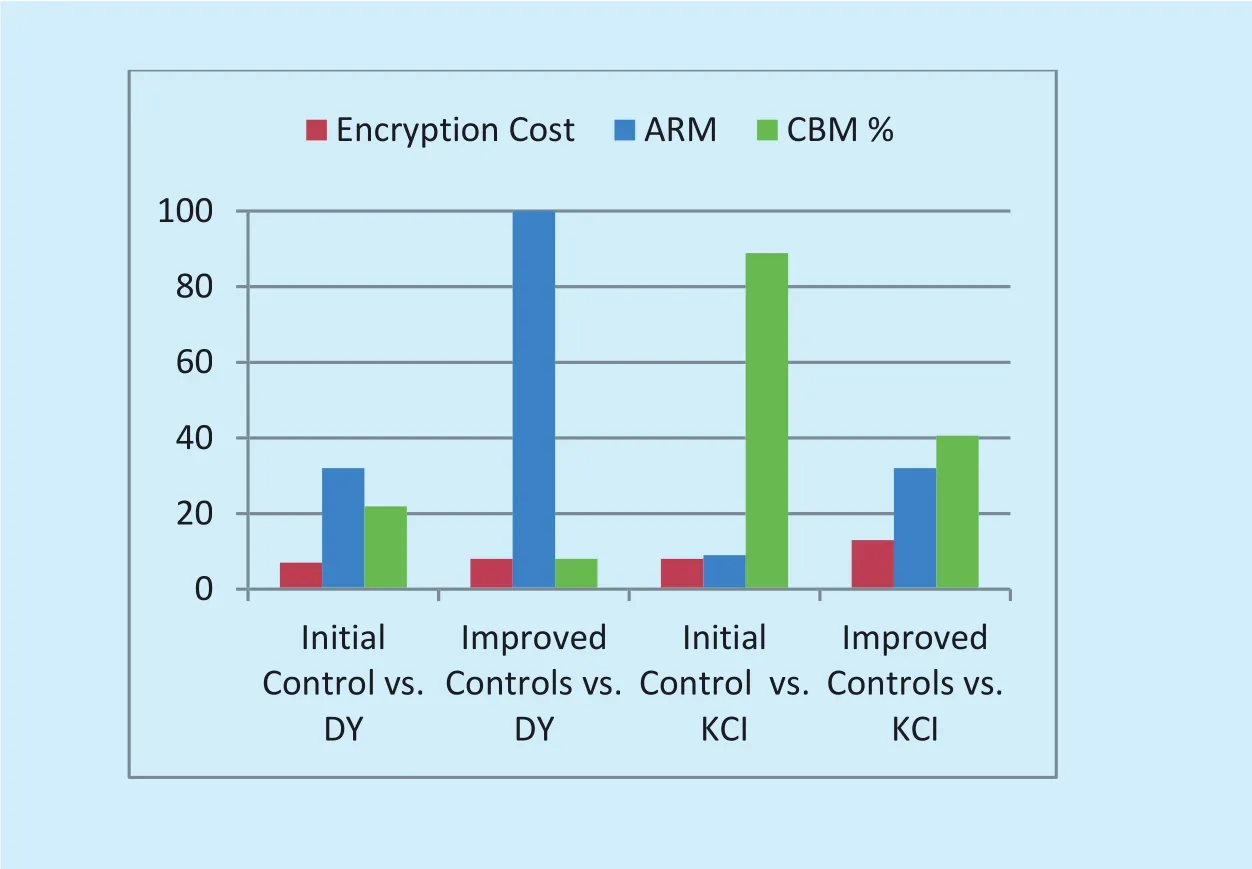
Fig. 8. Cost/Benefit Measure (CBM) of different security controls.
Figure 8 represents the cost/benefit measure of different security controls against DY and KCI attack models. The figure shows that CBM is high for the security controls provided to counter the attacks of the KCI attack model.The low value of CBM is always desirable. A high value indicates that cost of implementing the security control is higher as compared to the benefit gain of the security control against the attack model. In the figure, CBM is plotted as a percentage value to make it comparatively visible on the chart. Although the cost of“Improved Controls vs. DY” and the “Initial Control vs. KCI” is equal, however, proposed CBM measure tells that “Improved Control vs.DY” improvement results are better. Similarly,although the attack resiliency measure (ARM)is equal for both “Initial Control vs. DY” and“Improved Controls vs. KCI”, however, CBM measure tells that “Initial Control vs. DY” improvements resulted in better efficiency. This is the indication of the effectiveness of the proposed qualitative security metrics.
VII. CONCLUSION
This paper presented a n ovel approach for evaluating the security performance of communication and network security protocols through a relative quantitative security metric model. Three security metrics of attack resiliency measure (ARM), performance improvement factor (PIF), and cost-benefit measure(CBM) are formulated for the security evaluation of the security controls. As a case study,a secure VM migration protocol is taken as the target of assessment. Attack resiliency measure is calculated in terms of resilience of security control against several attempted attacks applied using two different adversary models. Performance improvement factor is a relative metric taking ratio of the difference of new and old ARM values to old ARM value.Moreover, CBM metric is the ratio of cost to benefit where cost is taken as a total number of encryptions required to implement the security controls and the benefit is ARM gain through the security controls. The results are given for three different security control states of secure VM migration protocol against two different adversary models. Results show that with improved security controls applied to VM migration protocol the ARM and PIF were increased against both DY and KCI attack models. However, cost-benefit measure value for KCI attack model (40%) shows that cost for implementing security controls against KCI attack model is more than the achieved ARM value (32%) whereas against DY attack model, CBM value was lesser (8%) showing that cost for implementing the security controls was smaller as compared to gain in ARM value (100%) in DY attack model.
ACKNOWLEDGMENT
The authors would like to thank the anonymous reviewers for their helpful and constructive comments that greatly contributed to improving thefinal version of the paper. They would also like to thank the Editors of this journal for their generous comments and sup-port during the review process.
- China Communications的其它文章
- A Stackelberg Differential Game Based Bandwidth Allocation in Satellite Communication Network
- Joint Resource Allocation Using Evolutionary Algorithms in Heterogeneous Mobile Cloud Computing Networks
- A Master-Slave Blockchain Paradigm and Application in Digital Rights Management
- The Coevolutionary Relationship of Technology,Market and Government Regulation in Telecommunications
- Mobile Jammer-Aided Secure UAV Communications via Trajectory Design and Power Control
- A Blind Spectrum Sensing Based on Low-Rank and Sparse Matrix Decomposition

